22 Apr Uh oh! You’re at greater risk of malware than ever before
Small and medium-sized businesses are at more risk of a malware attack than ever. It’s time to take action to protect your business. Here we tell you how....
15 Apr Be more productive with these Microsoft Edge features
In the never-ending mission to be more productive, the latest Microsoft Edge browser could be a powerful ally. We’re telling you about 3 of its best productivity features....
08 Apr Is this the most dangerous phishing scam yet?
Bad news: Cyber criminals have yet another new phishing scam up their sleeves and it could be the most dangerous one yet. They’re using genuine subdomains that have been abandoned. We tell you how to stay safe....
01 Apr Is Wi-Fi 7 worth the investment?
Is upgrading to Wi-Fi 7 the right investment for your business? We look at the pros and cons of the next-gen wireless connection....
25 Mar Cyber attacks: Stronger, faster and more sophisticated
A new cyber security report has brought some bad news: Cyber attacks are getting stronger, faster, and more sophisticated. We have all the details....
18 Mar The little things that make a big difference
Microsoft’s made another update to Windows 11, and while it’s a small one, it could make a big impact. We have all the details of what’s changing....
11 Mar And the award for most common phishing scam goes to…
Which phishing scam are you and your employees most at risk from? We tell you about the most common phishing emails and the easy way to stay safe....
04 Mar Before you replace your slow PCs…
Windows PCs running slowly? It doesn’t necessarily mean it’s time to replace them. There are some other ways you can give things a boost. We’ll tell you how....
28 Feb Mastering Email Deliverability: Navigate the Latest Google & Yahoo Updates with Our Expertise
In the ever-evolving landscape of digital technology, staying up-to-date and ahead of the curve is essential, especially when it comes to email deliverability. Google and Yahoo, two of the most influential players in the email service industry, have recently announced significant updates that could dramatically impact your email marketing campaigns. Understanding these changes is crucial for maintaining optimal deliverability rates, and we're here to guide you through every step. Google & Yahoo's Email Deliverability Enhancements Google & Yahoo are renowned for its commitment to user experience and security, and its latest updates are designed to further refine email deliverability. These enhancements aim to reduce spam and improve the accuracy of email filtering, ensuring that genuine, valuable emails reach their intended recipients: RETVec Platforms like Gmail, YouTube, and Google Play use text classification models to detect dangerous content, such as phishing schemes, inappropriate messages, and fraud. These models struggle to identify such content because attackers employ strategies like homoglyphs, invisible characters, and excessive keywords to skirt around the classifiers. To enhance the resilience and efficiency of text classifiers, a new multilingual text vectorizer named RETVec has been developed. This tool boosts the models' ability to accurately classify text while significantly cutting down on computational resources (Google Security Blog, 2023). Unsubscribe Button Sometimes users sign up for a service requiring only one-time access but end up receiving endless emails, making it challenging to declutter their inboxes. Companies often complicate the unsubscribe process, placing tiny, hard-to-find unsubscribe links at the bottom of emails. However, Gmail's latest update on Android simplifies this with a new feature. As noted by Android Police, Gmail now includes a prominent 'Unsubscribe' button at the top of email messages, allowing users to easily opt-out of further communications. By clicking this button, Gmail either directly halts future messages or redirects users to the sender's webpage to complete the unsubscribe process. (Skoulding, 2024). Email Authentication The latest policy revision impacts your domain's structure by mandating the implementation of SPF, DKIM, and DMARC for email authentication, confirming the legitimacy of your messages. These acronyms might sound complex, but they play crucial roles: SPF and DKIM records are essential for verifying the authenticity of your emails. They confirm that the domain mentioned in your "from" address actually belongs to you and that an authorized entity (like your mail server or any email service provider you use) is permitted to send emails on your behalf. On the other hand, DMARC provides guidelines on handling emails that fail to authenticate. For an email to clear DMARC, it must succeed in SPF and/or DKIM checks and alignment. (Monica, 2024). Get In Touch Don't let these updates catch you off guard. Reach out to us today to learn how we can help you adapt to these changes and leverage them to your advantage. Together, we can ensure that your online presence is strong, secure, and aligned with the latest industry standards. Contact us now for a consultation and take the first step towards mastering these updates with confidence....
26 Feb Which ransomware payment option is best? (Hint: none)
Cyber criminals are giving you more options when it comes to paying your way out of a ransomware attack. Our advice remains the same though. Find out what that advice is here....
19 Feb Bridging the trust gap between your employees and AI
Have you noticed your employees are reluctant to use AI in the workplace? It may be down to their lack of trust. We explain how to show them AI is a tool that makes work better for everyone....
12 Feb Don’t think your business is a target? Think again
Cyber criminals are targeting businesses of all sizes, all the time. And new research shows just how they’re doing it. We tell you how to stay protected....
09 Feb This new search feature in Edge is a revolution
Microsoft’s Edge browser has an amazing new search feature that we think is a total game changer, and the most compelling reason yet to switch. We have all the details....
29 Jan Windows 11 Moment 5 update
Microsoft will start to roll out its last Windows 11 ‘Moments’ update in a few weeks. After that it’s back to annual updates. We have all the details of the ‘Moments 5’ features you won’t want to miss. ....
24 Jan Microsoft wants you to pay for updates
Microsoft plans to charge for updates to Windows 10 starting next year (2025). We tell you your three options… and which we recommend....
12 Jan Google’s Next-gen email security
Sick of spam emails? We have details of a cool new tool to help keep us better protected....
14 Dec You’re not imagining it, video calls ARE stressful
Video calls stressing you out? You’re not alone. Scientists have warned about the negative effects of too much camera time. We have the solution for your team....
14 Dec New! A better way to find Chrome extensions
The Chrome Web Store’s been given a massive makeover, and it’s all about making your team’s life easier. We have all the details....
14 Dec Unwrap the gift of knowledge: 5 free AI courses by Microsoft
Microsoft has a little business-boosting gift that you won’t want to miss out on… five free courses about AI. We have the details, and the links to the courses....
14 Dec An AI-charged blast from the past
Microsoft Paint is all grown up, and it’s making a supercharged comeback thanks to AI. We have all the details...
20 Oct Quantum Cybersecurity: IBM Quantum Safe Technology
Quantum computing has been an idea for a while, and has recently been making steady advancements in the past 10 years. The first people who proposed the idea were Richard Feynman and Yuri Manin in 1980 (Microsoft, 2023). Since then, companies like IBM have taken interest in it. There is a point now in the world where there are physical quantum computers that are functional. With the advancement and realization of the quantum computer, IBM is taking a special interest in cybersecurity. Cybersecurity will need to evolve alongside the quantum computer. As we usher in the age of quantum computing, there needs to be a system in place to combat quantum cyber attacks. Enter IBM’s Quantum Safe Technology. “Governments and enterprises are rushing to form a quantum-safe strategy to protect critical data from quantum attack. Today, our IBM Quantum Safe roadmap helps organizations navigate this complex landscape by equipping them to track their quantum-safe milestones and achieve them using IBM technology, services, and infrastructure” (IBM, 2023). IBM has a roadmap specifically for cybersecurity. Here is what it looks like: (IBM, 2023). IBM is not the only one in the quantum market race. Many other companies are starting to dedicate research and development into quantum computers. Companies like D Wave, Intel, Microsoft, Alibaba, Bidu, and Google are investing into a quantum future as well. Having cybersecurity issues? Contact us for consultation and options for staying safe on the internet. References: IBM. (2023). IBM quantum computing | quantum safe. Retrieved October 20, 2023, from https://www.ibm.com/quantum/quantum-safe Microsoft. (2023). Quantum computing history - azure quantum. Microsoft Learn. Retrieved October 20, 2023, from https://learn.microsoft.com/en-us/azure/quantum/concepts-overview...
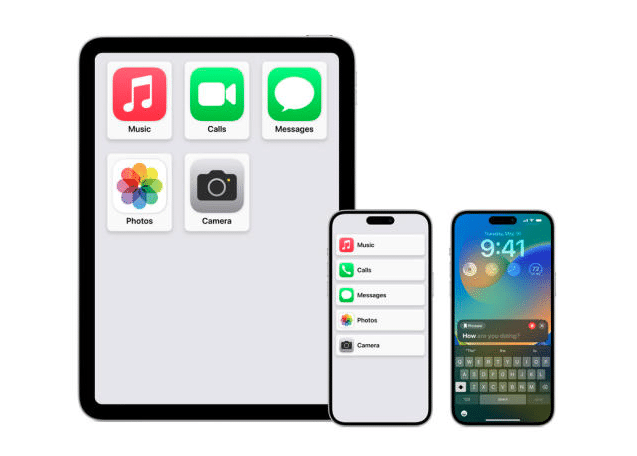
20 Sep Apple’s iOS 17 Brings Assistive Access
Apple's iOS 17 brings many new accessibility features aimed to lighten cognitive load. Among these features is Assistive Access. "Assistive Access uses innovations in design to distill apps and experiences to their essential features in order to lighten cognitive load" (Apple, 2023). This brings many cognitive accessibility features to the table. Tim Cook aims for Apple to be usable by any one with disabilities. Key Features of Assistive Access "Assistive access includes a customized experience for Phone and FaceTime, which have been combined into a single Calls app, as well as Messages, Camera, Photos, and Music. The feature offers a distinct interface with high contrast buttons and large text labels, as well as tools to help trusted supporters tailor the experience for the individual they support" (Miller, 2023). This makes it much easier to see apps and text on the screen, as well as streamlining the most essential apps. "For example, for users who prefer communicating visually, Messages includes an emoji-only keyboard and the option to record a voice message to share with loved ones" (Miller, 2023). How to Setup Assistive Access on iPhone Make sure you have iOS 17 installed. Step 1: Go to Settings > Accessibility > Assistive Access, tap Set Up Assistive Access, then tap Continue. Step 2: Verify Apple ID. Step 3: Choose layouts for apps. Step 4: Choose and customize apps. Step 5: Verify device passcode. Step 6: Set Assistive Access passcode. Step 7: Learn how to exit assistive access. Step 8: To enter Assistive Access later, go to Settings > Accessibility > Assistive Access, tap Start Assistive Access, then enter the Assistive Access passcode (Apple Support, 2023). These steps can be found in more detail here Need help setting up Assistive Access? Contact Us References Apple. “Apple Introduces New Features for Cognitive Accessibility, Along With Live Speech, Personal Voice, and Point and Speak in Magnifier.” Apple Newsroom, 28 Aug. 2023, apple.com/newsroom/2023/05/apple-previews-live-speech-personal-voice-and-more-new-accessibility-features Miller, Chance. “Apple Previews iOS 17 Accessibility Features: Assistive Access, Personal Voice and Live Speech, More - 9to5Mac.” 9to5Mac, 16 May 2023, 9to5mac.com/2023/05/16/apple-ios-17-accessibility-features “Set up Assistive Access on iPhone.” Apple Support, support.apple.com/guide/assistive-access-iphone/set-up-assistive-access-devcd5016d31/17.0/ios/17.0 ...
28 Aug The Dangers of Smartphone Ransomware
You’ve likely seen news coverage of ransomware targeting large companies or hospitals. Maybe you’ve seen Homeland when Claire Danes’ character falls victim to laptop ransomware during a surveillance mission. But did you know that ransomware attackers can also target your smartphone? A smartphone, after all, is a portable computer in your palm. Take a moment to imagine being locked out of your own phone. The hackers could gain access to your saved passwords and emails. You could lose access to your contacts, notes, and images, and even your three years’ worth of effort on Candy Crush. What You Need to Know About Smartphone Ransomware Also known as mobile ransomware, these attacks infect your smartphone. Instead of stealing the actual device, the bad actors take it hostage. They typically encrypt your data and make it so you can’t do anything. It may not be as widely publicized, but there’s already a long list of smartphone ransomware programs. The list continues to grow with examples such as ScarePackage, LeakerLocker, and LockerPin. ScarePackage can infect more than 900,000 phones in a single month. And before you think, “That won’t happen on my iPhone,” know that no smartphone manufacturer is secure. The type of ransomware may vary due to the different operating systems, but you can be at risk on both Android and an iPhone. Unlike other malware, the hackers usually want you to know they’ve gained control. Typically, they will notify you on your lock screen or home screen. You’ll often see a list of demands and a deadline to comply. That said, some mobile ransomware stealthily steals your data. What To Do About Mobile Ransomware The first thing to do? Be cautious. Keep these best practices in mind always: Regularly update your device's operating system and applications to patch any security vulnerabilities. Exercise caution when downloading or installing apps from untrusted sources. Avoid clicking on suspicious links or opening email attachments from unknown senders. Enable app and system updates to ensure you have the latest security patches. If you become a ransomware victim, try to disconnect your device from the internet. Turning off Wi-Fi and mobile data limits communication with the attacker’s server. Avoid paying the ransom. It’s tempting but not recommended. You are counting on hackers to keep their word and provide the encryption key. You can find decryption tools online for less complex ransomware. If the ransomware came from a malicious app, immediately delete that app if you can. What you can do will depend on the specific ransomware variety. In general, it's best to seek professional help. Work with an IT expert who can remove ransomware without further compromising your device. We can also help you restore clean, unaffected backups. Contact us today at 570-235-1946 or by filling out a contact form....
14 Jun Overheating Laptops
Is Your Laptop Overheating? Does your laptop have overheating issues?? Electronic components, including large capacity batteries, become warm in use.? Your laptop should never become too hot to handle though.? When a laptop turns hot to the touch or starts to sound like a jet engine, it's likely overheating. Modern laptops use nearly silent fans to cool components and keep the system is comfortable and safe to use.? In some cases, the sound the computer makes is the best tool you have to diagnose its running condition.? Excessive heat causes the fans to work harder and faster to compensate.? This jet engine sound is one of the first clues you have to indicate all may not be well. Why So Hot Because of their compact size and portability, laptop computers are particularly prone to overheating problems.? Their tiny footprint puts electronic parts closer together, creates less room for cooling vents and adds a heat generating battery which introduces more hot air into the system. Most laptops have small fans that suck in cool air,?passing it over metal fins to exchange heat from the case. The resulting hot air exhaust is expelled through vents back into the room.? This process prevents heat building up inside the machine.? The constant air cycle keeps the laptop running cool no matter the workload placed on it. This process can be interrupted by any number of factors during operation.? Alongside cool air, computer fans can also suck in dust, stray hairs, even cigarette smoke too.? Smoke in particular contains thick tar which coats the fins, fan blades, and internal components. Foreign debris inside the machine prevents components from working at their best.? Tar, dust, and hair slows down the internal fan and coats the heat generating components and cooling fins.? This coating prevents air exchange and keeping components warm as if they were under a blanket. Causes of Overheating Sometimes the way a laptop is used can cause it to overheat too.? Resting a laptop on thick carpets, blankets, or soft furnishings can block vents, preventing the fans from sucking cold air in or blowing hot air out. Leaving the machine running on carpet or furnishings can cause overheating issues and introduce extra dust into the components too. The best place to rest a laptop while in use is on a hard surface such as a desk, table, or lap tray.? This allows air free access to the vents and helps prevent dust and hairs getting inside the machine. You may also consider using a laptop cooling fan stand Overheating Results As the computer starts running hotter for longer, its fan will attempt to compensate by running faster and more often.? This results in the "jet engine" noise many users report when their computer is struggling to keep up. Unfortunately, once dust, hair, or tar has already found its way into the machine it is notoriously difficult to clean out.? The only way to reset the machine to run cool and quiet is to disassemble the base and clean out its components. Much like a car engine, computer components have a designed temperature range in which they can safely and reliably operate without any issues.? Extended periods of running above the temperature they are designed for can cause damage, sudden failures, and drastically shorten the designed lifespan of the computer. Unlikely Causes Often times seemingly random blue screen computer crashes can be traced back to components that have been overheating inside the computer.? As heat builds up, vulnerable components start to fail, sometimes temporarily, in the hotter temperatures. By the time the computer is rebooted and cooled down the issue is seemingly resolved.? Back in operation, the computer heats up once more and eventually crashes again.? These irregular crashes are highly inconvenient and can sometimes cause data loss too. However, these symptoms are minor compared to a complete write-off of the machine.? For some users, the first sign that their machine is too hot to run safely is when the motherboard is burnt out or their data storage has been irreparably lost. Check out this YouTube video made by HP Support that goes over How to Prevent Overheating an HP Laptop: If your laptop is running hot to the touch or has started to sound loud or irregular, bring it to us for a thorough clean. Visit our Contact Page or give us a call at 570-235-1946. ...
07 Jun MSP vs. MSSP: What’s in an Extra S?
Information technology (IT) has more than its fair share of acronyms. Often, it’s a matter of one letter differentiating the options. So, when it comes to MSPs and MSSPs, what’s the distinction? With MSP and MSSP you compare managed service providers with managed security service providers. But since MSPs also work to secure your IT infrastructure, the names alone don’t tell you enough. ? Key Differences Between an MSP and MSSP Distinguishing between these two can help determine which one better suits your business. The following helps you compare the options. Scope of Services MSPs and MSSPs focus on different aspects of IT management. MSPs typically manage, update, and maintain IT infrastructure and applications. They ensure business technology runs smoothly. They perform network and system health monitoring, as well as proactive maintenance. MSSPs specialize in security to protect networks, systems, and data from cyber threats. They protect your business from potential security breaches and support regulatory compliance. Practical example: An MSP might manage email, backup and recovery, or software updates, whereas the MSSP would offer services such as threat monitoring, vulnerability scanning, or incident response. Skill Set/Experience MSPs offer a more generalized understanding of IT and security best practices. They can oversee your IT operations either as a partner or your outsourced IT department. The MSSP’s experts typically specialize more in cybersecurity. They identify and mitigate complex security risks. Practical example: An MSP might have general IT technicians on staff. An MSSP's team specializes in areas such as penetration testing, threat intelligence, or compliance. Service Level Agreements (SLAs) MSPs and MSSPs meet different needs, so their SLAs are distinct. Expect an MSP to focus on response times, system uptime, or ticket resolution. The MSSP's SLA might relate more to incident metrics, such as detection and response times. Practical example: An MSP may guarantee a response time of four hours to resolve a system issue. The MSSP may guarantee to detect and respond to a security incident within 30 minutes. Cost Structure Expect different pricing structures depending on the service scope and expertise required. MSPs typically charge a fixed monthly fee based on the number of devices or services managed. This often costs significantly less than working with an MSSP. MSSPs may charge a combination of fixed and variable fees based on the number of security events, incident response, or forensic investigations. Practical example: An MSP might charge $50 per device per month. The MSSP might charge a flat fee of $5000 per month. You might also pay extra fees for remediating security incidents. Deciding on the Best Provider If your business primarily needs help with routine IT tasks, an MSP might be the best fit. Businesses with limited budgets or smaller-scale needs may also find MSPs more cost-effective. When you have sensitive data or compliance requirements, you could need an MSSP. MSSPs often have a deeper understanding of standards such as HIPAA, PCI-DSS, or GDPR. Choosing the wrong provider can waste resources and leave you potentially vulnerable. Contact our experts at 570-235-1946 or visit our Contact Page. We can help you make informed decisions about your IT management and security needs....
02 Jun Password Autofill: Convenience Compromising Security?
“What’s that password again? Wait, I changed it … Harrumph. I don’t remember!” We’ve all been there, sometimes many times a day. Password autofill on our Web browsers felt like the sun was shining on our online activity again. Sorry to tell you, but this convenience may not be entirely safe. Most browsers will ask after you’ve entered a new password into a site or changed a password if you want it stored for you. That way, when you revisit that site, the browser can autofill the access credentials for you. It saves you the struggle of trying to keep all your passwords straight. The problem is that some sites, including legitimate sites, can be compromised with a hidden form. You’ll never see it, but your browser will. So, it will autofill that form, and in clear, unencrypted text. This allows bad actors to capture your username and password without your knowledge. Another risk? Irresponsible digital marketers may use hidden autofill forms to track your online activity. That’s done without your consent. Using browser autofill with a password manager can also cause confusion, especially if your browser autofills, whereas the manager asks before filling in forms. Using both at the same time you also run the risk of duplicating passwords, which could make it difficult to track your passwords and increase the risk of security breach. ? How to disable autofill You can protect your passwords by disabling autofill on any browser you use: On Microsoft Edge, go to Settings, then Profiles, then Passwords, and disable “Offer to save passwords.” On Google Chrome, go to Settings, then Passwords, and disable “Offer to save passwords.” On Firefox, open Settings, then Privacy & Security, then Logins and Passwords, and “Autofill logins and passwords.” On Safari, from the Preferences window, select and turn off Auto-fill. Can I keep using password managers? A password manager, such as LastPass or 1Password, typically provides more security than browser autofill. Password managers have strong encryption algorithms to protect your login credentials, which means that even if your device is compromised, your passwords are safe. Still, if the manager autofills your credentials, you face the same risks. Most password managers have autofill disabled by default. That’s good. Leave preemptive autofill off. You might see it called “Autofill on page load.” Keep that turned off, too. Our advice? Use a password manager that requires you to click a box before it fills in your credentials. This action avoids your information from automatically populating a hidden form. Securing your online activity is an ongoing challenge. Our geeks can help identify ways you can protect your privacy and data online. Contact us today at 570-235-1946 or visit our Contact Page....
26 May What is Zero-Click Malware?
What is Zero-Click Malware? You know not to open an email attachment from someone you don’t know. You also avoid downloading unexpected files or questionable popups when you go online. But did you know there’s malware that requires zero action from you? Zero-click malware can infect your device without any interaction on your part. Traditional malware required the user to click a link, download a file, or execute a program. It often relies on phishing and social engineering to fool you into taking action. Zero-click malware exploits vulnerabilities in your operating system (OS) or applications. It uses carefully crafted, undetected code to access and execute a payload automatically, and there’s no trigger. If one is present on the system you’re using, you’ll navigate right into it. This makes zero-click malware attacks all the more dangerous. After all, they happen without your knowledge or consent. Meanwhile, attackers can use zero-click malware to: gain access to sensitive data, such as passwords or financial information; take control of your device; impersonate you and send out messages on your behalf; carry out additional attacks. Understanding Zero-Click Zero-click attacks exploit bugs, misconfigurations, or design flaws in an application or OS. They can come in many forms as attackers: target email applications and messaging apps such as WhatsApp or iMessage; build malicious websites; hack and infect legitimate websites; exploit vulnerabilities in network protocols or services. In one well-publicized example, Amazon CEO Jeff Bezos suffered a zero-click attack. A WhatsApp message compromised his texts, instant messages, and potentially even voice recordings. Another well-known attack targeted the WhatsApp accounts of journalists, activists, and human rights defenders in several countries. The attackers installed the Pegasus spyware on the targeted device simply by placing a phone call to the device, even if the user did not answer the call. The malware could extract messages, photos, contacts, and other sensitive data from the device, as well as activate the device's camera and microphone to record the user's surroundings. How to Protect Against zero-click malware Protect against zero-click malware by keeping your device's software up to date. These attacks are often designed to exploit unknown vulnerabilities in software, enabling automatic updates can help ensure you run the latest, most secure software. Also, install and use security tools such as antivirus software and firewalls, which help detect and prevent the malware from infecting your device, and remain cautious about clicking on links or downloading files from unknown sources. Further reduce your risk by using strong passwords and two-factor authentication. Plus, limit your device exposure to public Wi-Fi networks and unknown devices. In case of a zero-click malware or other types of data breach, regularly back up your data, too. Store backups on a separate device that uses strong encryption and two-factor authentication, or use a secure cloud storage service. Not sure about the strength of your online protections? We can help secure your devices. Contact us today at 570-235-1946 or visit our Contact Page....
30 Mar How to Stay Focused Working from Home
Working from home is not for everyone - we've all heard that said before - but many of us worldwide are now being forced to work from home. It can be challenging, especially when you have to adapt in the midst of all the other uncertainties COVID-19 has brought. These strategies can help you stay focused when working remotely. Reserve your office space Set up a temporary home office. Pick a space, if you can, that is away from distractions and has a door that you can close. Try to organize this space so that you feel more as if you're going into the office. Clear those personal bills and photo albums waiting for assembly from your desk. Creating a distinct space can help with the mental association that you are going to work. You'll also find it easier to focus if you dress as you would for work. Shower, and put on makeup if you normally do. Getting out of your pajamas and putting on your "game face" puts you more in work mode. Stick with your routines Keeping a similar schedule can help, too. If you go to the office at a certain time every day, that's when you should show up at your home workstation. If you took breaks at consistent times when on-site, do the same at home. This helps tell your brain it's business as usual, even when you're working in the laundry room on a folding card table! You may not be able to go out and grab a coffee or eat lunch out with colleagues, but you can still go have a cup in the kitchen or order lunch from a local business that's delivering - help them to stay in business too! If you used to write emails first thing, do that still. If your team had a weekly conference call Wednesdays at 11, try to keep that, too. You can use voice or video conferencing to stay in touch while remaining at a safe distance. Avoid distractions This is going to mean different things for people. Working from home with children is tough, especially as you're now supposed to be supervising their online learning. Giving them a dedicated space for schoolwork can help to keep them motivated and away from you. You might tell younger children to expect your attention at breaks (e.g. "I'll play three rounds of Candyland when the big hand reaches 12 and the little hand reaches 3"). The news and social media are other traps for those working from home. No one is watching over your shoulder, and it's easy to think, "I'll just check …" That's how you lose 30 minutes of productivity watching pandas wrestle on a zoo-cam. Still struggling? You could consider setting up one operating system account for work and another for personal use creating different browser profiles. And if you're still getting distracted, you could install a browser plug-in that forces you to stay on track. Keep deadlines Setting deadlines can help you stay motivated. The longer you have to get something done, the slower you'll work - it's inevitable. So, maintain some pressure by setting tight, but realistic targets. Share your deadlines with other colleagues using an online task management tool. This can help with accountability. Be patient This is a stressful time, and you're being asked to deal with many changes. So, you need to be patient. Working in sprints could help your motivation and attention span. You might set a timer and focus completely on work until the bell chimes. One theory is that the most productive people take a 17-minute break every 52 minutes, but you'll want to see what works for you. Another approach is to say you'll do 30 minutes of good work on that thing you're avoiding. Worst case: you get only 30 minutes of it done. At least you're further ahead. But you might find it only takes 30 minutes to complete or that you're so close to finishing that you keep going and get the job done. Have the right tech Make sure you have the right tools to do your job. Working from home is challenging enough, so make it easier with reliable internet and Wi-Fi connections, and access to the required files. Need help with working from home? We can't actually be there to cheer you on and keep you motivated, but our tech experts can get you set up with the most efficient home office solutions. Contact Now...
25 Mar Steer Clear of Corona Virus Scams
With the world grappling with a health pandemic, scams are shocking. Regrettably, bad actors are everywhere, always looking for opportunities, and they're seeing one in the corona virus. This article outlines what you need to watch out for and how to stay cyber safe. The last thing you want to read right now is that there's another threat out there - sorry, but it's true. Cybercriminals take advantage of fear. They take timely concerns and use them to target victims. Using the anxiety and upheaval around coronavirus is their mission. So far, several coronavirus-related attempts to cyberscam people have been reported. There are examples of: emails that appear to come from government health departments; offering a tax refund to get people to click on malicious links; memos to staff that appear to come from large employers; COVID-19 test offerings from private companies; fake websites promising to sell face masks or hand sanitizer; soliciting donations to help fund a vaccine. Scams to Watch Out For Another concern is the number of bogus websites registered with names relating to COVID-19. The site can look legit but is set up to steal information or infect the victim's computer with malware. You may get an email promising the attached information offers coronavirus safety measures, or information shared by the World Health Organization (WHO) if you click on the link, or a similar email pretending to be from a reputable news source, such as the Wall Street Journal (WSJ). In another example, an email impersonating a healthcare company's IT team asked people to register for a seminar "about this deadly virus." Anyone who didn't question why IT was organizing the meeting clicked to register. By filling out the form, they gave their details to hackers. What to Do Against Corona Virus Scams Be cautious. It's understandable that you're anxious, but don't let that stop you from taking cyber precautions. You should still: be wary of anything that tries to play on your emotions and urges immediate action; question where emails are coming from - remain vigilant even if the communication appears to come from a reliable source; hover over links before clicking them to see where they will take you - for example, in the WSJ example, the Web address was for the "worldstreetjournal"; avoid downloading anything you didn't ask for; doubt any deals that sound too good to be true ("a mask that stops the virus 99.7% of the time!"); ignore any communications requesting your personal information; don't be suckered by fraudulent pleas for charity. Global health organizations generally do not send out emails with advice. Instead, navigate directly to that reputable health institution for real news. Covid-19 related scams If you're still not sure about the validity of the communication, check it out. Do so by calling or using another medium to get in touch with the "source" of the received message. While there is not yet a vaccine for COVID-19, you can put anti-virus protection on your computer. Also, make sure that you've applied all available security updates to keep your software safe. We hope you'll take care and stay healthy both physically and online in these tough times. Need help installing security software and keeping your technology safe? Our cybersecurity experts can give your home a tech immunization. Contact us now!...
09 May What Windows 7 End of Life Means, and What You Can Do About It
Windows 7 is Dying Windows 7 reaches its "end of life". This means that Microsoft will no longer be working on it, causing it to become extremely unsafe and more inefficient, similar to how versions such as Windows XP and Windows Vista already are. Starting in 2020, Windows 7 will be a target for hackers like no other, putting your data and personal security at risk. The solution? Upgrade to Windows 10! It's faster, safer, more powerful, and overall a great decision to make for anyone using an older operating system. Windows 10 is the latest and greatest from Microsoft, receiving new features and performance improvements all the time. Windows 10 is set to reach its end of life state in 2025, so all of its users will continue to receive constant support for another six years! See if your computer meets the minimum specifications to run windows 10 Security: Windows 10 is by far the most secure version ever released. This is in part due to the fact that it's newer, smarter, and more aware of modern security threats. However, a large portion of the security of Windows 10 comes from continuous security updates from Microsoft. These updates come so frequently that your computer will install them automatically. Constant security updates are crucial to the safety of an operating system. It's time to upgrade. Speed: You may think that because Windows 10 is newer and has more features than Windows 7, it may run slower. This is not true! Windows 10 not only brought new and helpful features to the table, but it also increased the speed of several things like startup time, time taken to wake from sleep, and general computer performance speed. Even on older machines, Windows 10 speeds up computers by being a more efficient operating system than Windows 7. Features: It goes without saying that a new version of anything comes with new features. Windows 10 is no exception, as it's chock-full of new things relating to user assistance, visual design, ease of access, and computer maintenance. An operating system has never been so easy to navigate with the addition of Microsoft's new AI assistant, Cortana. A Siri-like program that can answer various questions about the operating system, general knowledge, or your data that you've input into it such as contacts and calendar events. The new design of Windows 10 is also sleeker than ever, taking the top spot on many people's lists of most attractive operating systems. This is all accomplished while still retaining that old and reliable Windows 7 layout of things. You won't have to wonder where most things are in Windows 10, because Microsoft didn't waste time by reorganizing every utility just so users would have to re-learn where to find things. The content and design of the latest Windows operating system is more solid, consistent, and robust than ever. Worried about the transfer? If you’re concerned about having to learn to use a new operating system, don’t be. Windows 10 is largely similar to Windows 7 in its layout, and Windows 10 is equipped with a much greater range of helpful tools to assist all users in navigating their computers. Additionally, the upgrade from Windows 7 can be completely seamless, maintaining all of your programs and personal files in exactly the same place as they were. At NEPA Geeks, we guarantee that the process will be as simple and as stress-free as possible. Need help making the switch? Call us at 570-235-1946, and we'll handle it all from backing up your data, to protecting your computer by upgrading it to the latest version of Windows. You won't look back. Contact ...
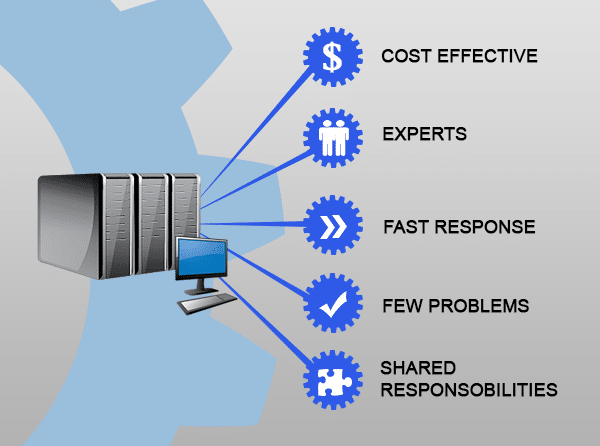
28 May 4 Advantages of Managed IT over In-House IT
4 Advantages of Managed IT over In-House IT It’s tempting to hire an in-house IT technician to take care of your network. Instead, consider the advantages of managed IT. If you’re like most businesses, you’re always on the lookout for ways to save money while improving results. This means expanding your staff to include a team of tech specialists. This can be an unnecessary expense that leaves you with highly paid employees with a lot of downtime. For SMEs who are looking for the best of both worlds, we recommend Managed IT services. Put simply, Managed IT is our solution which gives you a team of specialist technicians and network experts. Naturally, you’d rather see your IT budget working to support your growth and kept as low as possible. We don’t simply maintain and repair your systems, we proactively monitor to avoid downtime and work with you to ensure your IT increases productivity and efficiency. Whether you already have in-house IT and are auditing the value, or are curious about what having IT support might be like for your business, we’ve put together a few factors to consider before making your choice: Availability: Most employees work 9-5, but what happens if something goes wrong with your systems outside these hours? Your in-house technician won’t appreciate being woken at 1am for emergency repairs. It’s more likely that they simply won’t answer the call (or hear it), or if they do, expect some hefty contract renegotiation come 9am. Managed IT is very different as we expect problems after hours and have support technicians ready. We know that every minute of downtime is affecting your revenue, plus your business reputation, so we prioritize getting your systems up and running asap. As a bonus, with our Managed IT these types of disasters are rarer as we’re constantly monitoring and correcting problems before they occur. Total cost: One of the things that may have attracted you to having an in-house technician is the cost. But while you may be able to pay them a lower hourly rate, there are extra costs like hiring, training, ongoing training, healthcare and retirement. Once you start adding up the cost of an in-house technician, you might find it’s eating up your IT budget and leaving you scrambling to fill gaps you didn’t expect. Upgrades get delayed, opportunities missed, and IT expenses become a sore point. In comparison, Managed IT is one fixed monthly rate including access to specialists across all software applications and technology. Ongoing Training: Your technician will spend weeks away upgrading their skills. Those training costs quickly add up. With a salaried technician, you’ll have to pay all ongoing training and certification costs, plus travel costs for industry conferences. We know how important it is to remain current, certified and skilled in new technologies, so we spend the money to invest in ourselves so we can serve you better. We’re part of industry related communities and attend multiple conferences each year, all at our own expense. Different goals: For most employees, a higher wage is the goal and many will job-hop to achieve that. A salaried tech may be looking for the first opportunity to leave and get paid more, often leveraging all the training you’ve just provided. In these modern times, switching jobs regularly is expected, with an average of only 3 years in each position. Considering how much it cost your business to acquire, train and upskill your technician, 3 years is an unreasonable ROI. Our goals couldn’t be more different - we only aim to keep you a happy customer for as long as we can! In the end, your business needs to find the right balance between profit and expertise. When you partner with our Managed IT, you’re securing availability, ever-increasing expertise and commitment to your success. We work closely with you to provide the very best support and protect you costly disasters, taking preemptive action to keep you safe and operational. There’s no doubt Managed IT is a better decision than hiring an in-house technician, and we’d be delighted to prove it to you. Talk to us about Managed IT for your business. Call us at 570.235.1946 or visit our Contact Page...
21 May How Refurbished Computers Save You a Bunch (and Get You a Better System)
How Refurbished Computers Save You a Bunch (and Get You a Better System) Refurbished computers are almost like an insider secret - you can get great system specs for a fraction of the price. It’s how many families are meeting their back to school needs and upgrading their old systems, complete with warranty. There’s one hot tip these people know: a refurb is NOT the same as used. You’re right to avoid those 2nd hand computers you see on Craigslist or Gumtree because there’s a reason that person is selling it! Quite often, refurbished computers start their life as business machines, built to the latest specs with business-grade components. When the budget or lease says ‘replace the computers’, that’s what the business does, whether the computers need it or not. There’s nothing wrong with them. These are great machines that are fast for home use, both desktops and laptops. Rather than send these impressive machines to landfill, we check and replace necessary components and re-install a clean operating system. Benefits of Buying Refurbished Saving Money: Get a computer that’s set up and checked over by an expert technician for less than the cost of buying new. When you score a refurbished business computer, you’re also getting more durable, higher-quality components that will last you for years. Warranty: Warranty included with our refurbished computers. If anything pops up that’s giving you trouble, we’ll fix it fast. Environmental: Fewer machines end up in landfills, and fewer resources are used for manufacturing. Considering each computer requires a certain amount of precious metals to be mined and plastics to be created, refurbished is the right choice for a greener future. Refurbished Reliability Some people think refurbished computers are more likely to break, when in truth, they’re actually more reliable than brand new. Manufacturers have an expected failure rate, a percentage of computers that go straight from the factory to buyers who discover their expensive new system is dead-on-arrival or breaks within weeks. A refurbished computer has already stood the test of time and it performed without missing a beat. Check out your favorite computer brand's website, as they may have a refurbished section on their site. Checkout PCLiquidations for great deals on refurbished computers! If you need a better computer on a tight budget, give us a call at 570.235.1946 or visit our Contact Page...
14 May 3 Essential Steps Before You Fire an Employee
3 Essential Steps Before You Fire an Employee What are the 3 essential steps before you fire an employee? Employees need access to various business accounts, but what happens to those passwords when they leave or get fired? Nobody likes to think of firing their employees but nonetheless, it’s a responsibility every business owner must face. Most of the time, the former employee leaves under good terms. If you’re lucky, they’ll even manage hand-over to their replacement so your productivity losses are minimal. Other employees may leave your business reluctantly or in a storm of anger and suspicion. While you’ll have very different feelings about the two scenarios, the risk to your business remains high until action is taken. Here are 3 steps you can take to protect your business from retaliation and other password-related disasters. Limit Employee Access to a need-to-know basis You might be surprised how often a new employee is presented the entire business on a platter when their actual job requires little more than a computer login. Accounts, strategy, customer details, industry secrets...
07 May 3 Internet Habits To Keep Kids Smart and Safe
3 Internet Habits To Keep Kids Smart and Safe Internet habits to keep kids smart and safe while browsing the web is imperative. It’s a common concern as all parents want their kids to be protected and happy whenever they go online. Safe internet usage goes beyond reminding them not to talk to strangers. With the evolution of the internet and the way it’s now woven seamlessly into our lives, the focus needs to be on ingrained habits. That means ensuring your children have the tools and predefined responses to online events so that no matter what happens, they’re not placing themselves (or your family) at risk. Setting up these habits is easy, and begins with three basic understandings: Internet Habit of Restricting Downloads Most kids can’t tell the difference between a legitimate download and a scam/malicious link. The online world is full of things that will trick even the most savvy adult. Kids tend not to take that extra moment to check where that link is pointing. They want to get back to what they were doing. If something pops up, their first instinct is to click ‘yes’. Unfortunately, that single ‘yes’ just opened the doors to malware and viruses that will ruin their computer. To keep your kids safe, set a family rule that they need to ask permission for all downloads (and an adult will check it first), and to never click a popup. Talk through exactly what you’re checking and why. As your child matures, get them involved in this process. Critical Thinking Internet Habits Kids think the internet is a magical place and can’t imagine their life without it. To them, the internet is on the same level as oxygen! With that acceptance though, comes unwavering trust that the internet would never lie to them. While we adults know better, it’s only because we already view the internet with a certain level of distrust. The best way to keep kids safe is to teach them to approach the internet with critical thinking. That includes teaching them to question the motives of other people online. All kids need to be aware that predators use the internet to target and lure children. Ensure your children tell you immediately if a stranger makes contact. Along with this stranger danger, teach them to identify what marks something as suspicious. The Internet is Forever Kids have an overwhelming drive to contribute to the internet, they don’t think twice about recording a video, jumping in a chat room or onto social media. The world really is their playground! But what they don’t understand until they’ve been burned, is that anything they upload, write or say is on the internet forever. Even if they delete it or use a platform where content self-erases, someone can still screenshot and send it right back out. Many cyber-bullying cases are based around this exact type of blow-back. Once your kids know that everything they post is permanent, they’ll be more likely to pause and think. Read more about keeping your kids safe on the internet We can secure your computer and help keep your family safe – give us a call at 570.235.1946 or visit our Contact Page...
23 Apr Are You Backing Up the Right Way?
Are You Backing Up the Right Way? The 31st of March is World Backup day and it’s a great time for backing up. So this is your reminder, that even if you only do this once a year when the calendar tells you to, it’s time to flip that to-do list and make it happen! But how? What’s the easiest, most effective way for your business to backup? You've probably heard of file backup by a number of names: Cloud Sync, Cloud Backup or Cloud Storage. They’re all similar enough to be confusing and meaningless enough to be anything. Here’s what they mean and which one you need today. Cloud Sync Backing up is possible with Google Drive, Dropbox, iCloud, etc. They are services that sync up with a single folder on your computer. They mirror it. When a file changes in one, the sync service rushes to change it on your computer too, so they are always the same. Cloud Sync services are hugely flexible for remote employees. They’re ridiculously easy to use, require no training, and the free tiers are enough for most individuals. This all sounds amazing, right? Except...
16 Apr How to Maintain Your Computer (Without Lifting a Finger!)
How to Maintain Your Computer (Without Lifting a Finger!) If you want to maintain your own computer, this is the article for you. There’s so much to keep track of that it’s no wonder most people forget the routine maintenance. Of course, the problem with being reactive is the damage is already done. Photos and files get lost forever in a crash, and information gets stolen in a hack. By then it’s far too late. It’s a bit like closing the gate after the horses have already fled. This is where proactive people come out on top. Thousands upon thousands of homes around the world are using managed services to put computer problems firmly behind them. It’s a done-for-you maintenance program we offer, and here’s why it’s the best choice. You’re Always Up to Date It seems like every second day there’s some new and urgent update waiting to be installed. Whether they’re patching security flaws or adding new features, they seem endless. Sometimes, it goes beyond inconvenient, it gets overwhelming! Even if they do install automatically, they tend to do it at the worst possible moment, leaving you to wait up to 30 minutes when all you wanted to do was quickly check your email. Using our special managed services software, we can make sure your computer’s updates are all finished and done - before you sit down to use it. After all, updates are supposed to make your experience more secure and more enjoyable! You’ve Got Super Anti-Virus The best anti-virus is the one that’s up-to-date and running, yet you’d be surprised how many people switch it off or never let it update. While you might be in the habit of scanning files and browsing safely, others in your home might not have the same priorities. Having managed services ensures your anti-virus is always running and dealing with any viruses it finds. As soon as a new virus becomes known, we make sure your system is actively protected against it. We also monitor for cyber-attacks and can alert you before they become a problem. Your Hardware Stays Healthy Our special software monitors the health of your hardware, eg, your hard drive, looking for early warning signs of failure. If detected, we can let you know in advance. This means you’re able to get it repaired at your convenience, making sure no files are lost and no other hardware is damaged in a domino failure. You Never Miss A Backup The worst part of a crash or hack isn’t the financial cost, it’s losing your files forever. People have their entire collection of photos stored on their computer, plus important family files, most of which can never be replaced or recreated. Managed services ensures your backup is working correctly. Backed up files are ready to go when you are, and losing files to corruption, failure or theft is a thing of the past. Support is A Phone Call Away Just got a new printer and it won’t play nice? Got a weird error popping up? Your laptop won’t talk to the wifi? Our remote support team can help with whatever technology issue has been bugging you and wasting your time. No nonsense advice is just a phone call away, and our team can remotely connect to diagnose and fix many problems. This means you can likely skip the cord shuffle and carting your computer into the shop, and still get your most pressing computer issues fixed. You’re Always Optimized Whether your computer is actively playing up or not, our monitoring service can keep in touch with your event logs, services and processes and look out for anything that needs correction. This means we’re effectively stopping problems before they get to you, making sure that when you sit down to use your computer, it’s doing exactly what you want. Put computer problems behind you - get managed services today. Call us at 570.235.1946 or visit our Contact Page...
09 Apr Why Spam is a Small Business Nightmare
Why Spam is A Small Business Nightmare Spam has become a small business nightmare. 15 years after the world united to crack down on spam emails, we’re still struggling with overloaded inboxes. All that unwanted email continues to flood the internet, much of it targeted towards small businesses, and the impact goes wider than you might think. Here’s the full breakdown of how modern spam works and how it’s hurting your business. What is Spam? Spam is any unwanted message that lands in your email, comes via text, social media messaging, or other communication platform. Most of the time, spam is annoying but relatively innocent messages from another business inviting you to buy/do/see something. They’re newsletters, reminders, invitations, sales pitches, etc. You may know the sender and have a previous relationship with them, or they might be a complete stranger. Occasionally, spam may even be part of a cyber attack. Why You're Getting Spam Maybe you or your employee signed up for a newsletter or bought a $1 raffle ticket to win a car. Perhaps you got onto the mailing list accidentally after enquiring about a product, not knowing that simply getting a brochure sent through would trigger a spam-avalanche. Often there’s fine print that says they’ll not only use your details to send you their marketing, but they’ll share your details with 3rd parties so they can send you messages too. That single email address gets passed around like wildfire. Before you know it, you’re buried under spam. More than Annoying We all know spam is annoying, but did you know it’s also resource hungry? Your employees are spending hours each week sorting their email, assessing each one for relevance and deleting the spam. Add in the temptation to read the more interesting spam emails and productivity drops to zero. On the other side of the business, your email server might be dedicating storage and processing power to spam emails, occasionally to the point where inboxes get full and real mail is bouncing out. While most spam is simply an unwanted newsletter or sale notice, there’s also the risk that any links may be a cyber-attack in disguise. After all, one click is all it takes to open the door to viruses, ransomware, phishing or other security emergencies. How to Stop the Spam The 2003 Can Spam Act (a global set of anti-spam laws) requires all marketers to follow certain rules, like not adding people to mailing lists without permission, and always including an ‘unsubscribe’ link. So firstly, make sure you’re not accidentally giving people permission to email you - check the fine print or privacy policy. Next, look for the unsubscribe link at the bottom of the email. Unfortunately, not all of them include the link, or they hide it somewhere impossible to see. The worst spammers take that ‘unsubscribe’ click to confirm that your email address is valid/active and then sell it on. Talk to us about your anti-spam protections. Call us at 570.235.1946 or visit our Contact Page...
02 Apr 5 Signs Your Computer is Crying Out for Repair
5 Signs Your Computer is Crying Out for Repair It’s pretty obvious when your computer is already broken, but how do you know when it’s about to break? Even before it falls into a heap and refuses to turn on, or flashes big messages about how your files are now encrypted, you’ll be given multiple hints that something is wrong. Here are the common signs your computer needs repair, sooner rather than later. It’s running slow Most people assume their computer is running slow because it’s getting older, but it could actually be a variety of reasons. A program behaving badly, a virus, overheating or even a failing hard drive can all cause a massive slow down. You might only notice it when booting up or starting a program, or the problem may have taken hold to the extent that even moving your mouse becomes torture. Sometimes the slow speed is simply due to some newer software that your hardware can’t keep up with. Your system is running hot A very common sign with laptops, running hot can be both the sign and cause of damage. Computers have fans to blow out hot air so they can cool off their internal components. At the same time, fresh air is drawn in through vents to create an effective cooling system. Unfortunately, just about every vent in a computer can quickly become clogged with dust and pet fur, essentially choking off the circulation and leaving components to overheat. Desktop computers have more space inside to circulate air, but you’ll still need to keep their vents clear. You’ll know your computer running too hot if your system shuts down frequently (safety cutout), the fan is working serious overtime, or your laptop is too hot to use on your lap. Blue Screens of Death are everywhere A classic Windows error, this is quite literally a blue screen that covers your view. The system will still be running, but something has gone wrong. You’ll be shown some text and an error code, often with Windows suggesting a restart. If a restart fixes your problem, perhaps something didn’t load properly at bootup and your computer had a whoopsie. It’s rare, but it happens. If you’re getting blue screens all the time though, that’s a sign a hardware or software problem needs to be resolved. Your computer will continue to give blue screen errors more and more frequently, so it’s best to take action as soon as you know something’s wrong. It’s making strange noises Your computer has a number of moving parts. You’ll know by now which noises it normally makes, from the startup beep to the whirring fan. When your computer starts to make extra noises...
23 Oct Feeling the Budget Pinch? Here’s How Managed IT Can Save Money
Feeling the Budget Pinch? Here’s How Managed IT Can Save Money When it comes to running a modern business, technology is always a growing line item in the budget. Costs seem to creep up every quarter, along with a new learning curve for simply keeping everything running along smoothly. One universal concern for businesses are tech budget restrictions. When the tech department gets the budget pinch, managed IT can be a great solution. You’re balancing the outlay of maintenance with replacement, plus securing against threats – making sure every dollar gives maximum ROI. Sounds exhausting! The tech department budget gets stripped to a bare minimum. Now, imagine if budget wasn’t an issue. Imagine all tech expenses predicted and capped. Sounds good, doesn’t it? Put simply, that’s how a Managed IT Service works. Managed IT is a service designed for businesses with a limited budget and time for tech issues. For a fixed price each month, you get a team of IT technicians actively monitoring your systems in order to catch issues before they occur, repairing problems on the fly, and ensuring your business is always as secure as possible. Included as part of your Managed IT Service, you also get expert business consulting around the solutions you need now, which solutions will help you rapidly scale, and which technology you don’t need. All for one predictable, fixed price each month. It gets better: You’ll reduce downtime and associated revenue loss Forget scrambling while systems are down, with Managed IT Services you’ll know which tech is failing and can proactively repair or replace before it impacts your business. Downtime is planned/minimized and staff are working uninterrupted. You’ll skyrocket efficiency You’ve probably been responding to your IT events in ‘firefighter mode’, essentially dealing with problems as they arise and switching to new, improved tech only when you must. Managed IT Services automatically report problems. Technical issues slowing down productivity are detected and solved. You’ll secure against data loss Whether you’ve been following the news and worrying about the next cyber-attack, or you’re working with confidential customer or proprietary data, your Managed IT Service has you covered. Our technicians secure your business against attack using the latest technology, full backups, software updates and leverage every drop of their know-how to keep your valuable data safe. Learn more ways Managed IT Services can benefit your business - give us a call at 570.235.1946 or visit our Contact Page...
16 Oct Should I Upgrade or Buy a New Computer?
Should I Upgrade or Buy a New Computer? Well, it depends – mostly on who you’re asking! A department store salesman will always recommend a new one, but when you get down to the nitty gritty with a trained technician, you’ll often discover you have more (and cheaper) options than you thought. Where can one start when figuring out if they should upgrade or buy a new computer? Start by taking stock of what you’ve got. Sometimes a computer upgrade simply isn’t worth the trouble and it’s painfully obvious. For example, if your car is 30 years old, demands a constant supply of special fuel and you can see the road whizzing by thanks to the ‘custom’ holes in the floor…it’s time to replace the rust-bucket! However, if your car is decently modern and in reasonably good condition but happens to stall at stop signs, a few quick fixes can be just what the mechanic ordered. If your computer does need to be replaced, chances are you already know this. But if you’re not sure and some days it could go either way, this will help. Common upgrades and the impact they’ll have: Video card upgrade: It might not be your computer that’s getting old. Instead, games are getting more and more demanding. The days of stick-figure animations are gone and lifelike 3D is the new normal. With that improved experience comes a huge strain on your computer’s resources. If you have a gamer in the house, you can often super-power your computer with a single component upgrade – a new video card. For hardcore gamers, it’s a necessary buy, as some new games refuse to install if the video requirements aren’t met. Love smooth animations and responsive gameplay? We know all the best games out now (and in the works) and can match you with the right video card. Hard drive upgrade: New hard drives are a popular option, both in size and speed. Running out of space is less of a problem now, but speed is a major concern. You’ve no doubt sat there twiddling your thumbs and urging a file to hurry up and copy. Many upgrades are to an SSD (Solid State Drive) that has zero moving parts and can find/transfer data in a flash. They even make booting up lightning fast! And you’ll have the choice of keeping your old drive for general storage, complete with all your existing data. Memory/RAM upgrade: Some cheaper computers are underpowered from day 1. In truth, most of the ones in the department store could use at least an extra 4GB of oomph! Sometimes though, even a great computer falls behind as new applications come out and need more resources. Adding extra memory can revive your existing computer and set it up for a couple more years of happiness. Find out if your computer can handle more RAM by checking out Crucial's Memory Upgrade Finder on Crucial's website. Where to draw the line: There are other upgrades such as the CPU, which is basically the brains of the computer; and the motherboard that all the parts plug into…but once you’re in that territory, it really is time to go for a full replacement. You’ll save money by getting a computer that meets your needs and can grow with you. Is your computer letting you down? Contact us now!...
09 Oct 6 Simple Tips to Protect Customer Data
6 Simple Tips to Protect Customer Data In this day and age, businesses must protect customer data. As cyber-attacks continue to make headlines, hackers are exposing or selling customer data files in record numbers. But just like with any threat, there are actions you can take to minimize risk and ensure your business retains a positive reputation among customers. Stop Using the Same Password Repeatedly Set a mandate for all staff that passwords must be unique for each user and for your workplace. That means it can’t be remotely like the one on their home PC, tablet or online banking. Passwords are hacked more than ever, so when you’re prompted for a password change, dig deep and really think about what goes into a hacker-proof password. If remembering them is a problem, consider one of the latest password management tools. Go On a Shredding Spree How much sensitive data is being dumped into the recycling bin? Valuable customer data is often taken from the bins of small businesses and quickly sold or published. It’s not just good practice to shred sensitive documents, it’s the law. Take 5 seconds to run documents through the shredder or book in the services of a secure shredding company. Ditch the Accounting Spreadsheets Still using an Excel doc for all your number-crunching? Besides making your accountant’s job harder (and more expensive), you’re opening your business to a massive range of vulnerabilities. Even with password-protection, spreadsheets aren’t designed to safeguard your financials or those of your clients. Upgrade to a proper accounting solution with built-in customer data protections and security guarantees. Train Staff Explicitly You can’t rely on common sense because what you think is a given might be news to someone else. It can be extremely beneficial to hold special data-safety training sessions once or twice a year as a reminder, as well as take the time to induct new staff into the way things are done. Limit Access to Data Just like the bank manager who guards the keys to the vault, you can limit who accesses your data. Revoke employee access as soon as they leave your business for good, and set rules around who can access what – and when. Do they need access to sensitive information while working from home? Should they be able to change the files, or only view them? Keep Software Updated Possibly the most preventable hack, having outdated software can be an open invitation for cyber-criminals. They look for known weaknesses in business software and waltz right in. While the nagging pop-ups and reminders to update can feel like a selling ploy, they’re actually helping your business to stay in the safe zone. Updated software gives you protection against new viruses and hacking techniques, plus closes off those nasty weaknesses. If you would like to make sure your business is secure from data breaches, give us a call at 570.235.1946 or visit our Contact Page...
02 Oct Why Do People Create Viruses?
Why Do People Create Viruses? You’d be right in thinking it’s hard to program a computer virus that can spread across the world in a flash - we’re talking days of constant desk-jockey nerd-work. So why do they bother? Well, it generally comes down to 3 reasons: Money, showing off their skill, or to simply being a jerk. While showing off or being a jerk is pretty self-explanatory, the money side is fascinating. Here’s how people are making money with computer viruses: Bank Account Theft: Virus creators are more than happy to help themselves to your bank details, sneaking in to grab your login details or credit card info. They can either transfer your funds away or use your credit card details to go on a shopping spree. Sometimes they’ll leave the fun to another person though, and simply sell your details to the highest bidder. Ransomware: Rather than a financial snatch and grab, sometimes a virus will encrypt your files and demand money for the unlock code. Without a true backup plan in place beforehand, you’re at their mercy. You’re given helpful information on how to pay, then your files are destroyed. Ad Swappers: A cheeky technique, this is when they create a virus that either puts annoying ads on websites you visit, or places affiliate codes on pages so that when you buy something legitimately – eg, from Amazon – they get a percentage as a ‘referral fee’. Their kickback doesn’t make your purchase cost more and you may not even know you’re supporting their activities. Bitcoin Mining: Digital currency is used for payment, but did you know you can also earn them with your computer processing power? Unfortunately, ‘renting’ out your computer’s processing power means paying more in running costs than you’d make – unless you were very clever and sneaky, and used a virus to rent out other people’s computers. Botnets: Certain infected computers can be remotely controlled to do whatever the virus creator wants. In this case, they’ll usually set the infected bot computers to overwhelm a target web server, like an e-commerce store. Sometimes it’s done as revenge, but more often it’s blackmail. The ‘Botmaster’ says “pay me thousands of dollars or I’ll crash your site during the biggest shopping day of the year.” Account Stealing: Subscription accounts like Netflix and Hulu are often hijacked. Sometimes, virus creators go one step further with online gaming accounts. All those digital items that you fought so hard for (special clothing, weapons etc.) can carry real world value and be stolen from your account and sold on a black market. Yes, that’s cheating! Give us a call at 570.235.1946 or visit our Contact Page to make sure your computer is secure and protected....
21 Aug 7 Bonuses for Small Business in Office 365
7 Bonuses for Small Business in Office 365 You’ve seen all the ads for Office 365. They’re popping up on your desktop, your employees are sending you meaningful looks, and clearly, it’s not going away. You’ve probably even jumped online to see what all the fuss is about. But is Office 365 a necessary upgrade for your small business? The answer is yes. It’s more than a refreshed set of tools, it’s an efficiency and productivity powerhouse. Here are 7 spot-on reasons why small business owners should upgrade now. Data security is built in Office 365 was created with data security at its core. The built-in compliance and security protocols mean your cloud storage is safe, and you can control access so your valuable data remains exactly where you want it. Storing your data in the 365 cloud keeps it safe in case of emergency, with 1TB of storage per user included at no extra cost. Ditch the licensing drama Software version differences can be a real nightmare in a small office. Not every system can do the same things, and half the time, they can’t even open the same files. It quickly becomes a hodge-podge of workarounds and lost time. Office 365 includes site-wide licenses with upgrades at the same time. Mail storage for real people Not everyone lives in the land of inbox zero. In fact, most people tend to leave messages in their inbox forever. Occasionally we’ll do a quick clean up, but only when the alert comes in that the mailbox is full. Meanwhile, new emails from customers may be bouncing away with the old ‘mailbox full’ message. Eek! In Office 365, your employees can communicate without worrying about storage space. Better time management Every person in your business is juggling meetings, emails and contacts – usually across multiple platforms. Office 365 brings all those elements together, integrating seamlessly for more efficient time management. Contacts updated via mobile while offsite are automatically updated across all connected devices. Meetings scheduled in an email are added instantly to the calendar. You can even access files from any device, edit on the run and then back in the office, simply pick up where you left off. Predictable costs Forget about planning (and delaying) those costly upgrades. Office 365 has small business covered. You can choose a plan based on your unique needs and change at any time. You can even add or decrease the number of users as you scale and streamline. It’s so easy to fit Office 365 into your monthly budget while knowing you’ve got the very best and latest in small business software. Work on the go The days of fiddling with private network and security settings are over, thanks to Office 365. You don’t even need any special IT skills or extra software. Users can now securely access their files from home, during their commute, or in meetings for on-the-fly impressive presentations. Got an internet connection? That’s all they’ll need to squeeze productivity out of every day. Stay up and running with no downtime A whopping 25% of small businesses shut down permanently after flood, fire, crash or cyber-attack. With Office 365, all your data is stored in the cloud with built-in backups for redundancy. No matter what happens, your data will be there, letting you stay up and running – and always ahead of the pack. If you are ready to take your email to the next level, give us a call on 570.235.1946 or visit our Contact Page...
14 Aug Why is my Computer Running SLOW?
Why is my Computer Running SLOW? Is your computer running slow? Your computer used to speed through startup and let you open almost everything at once, but now it’s struggling to crawl along! Everything takes so much longer or crashes without warning. Something isn’t right. If it’s gotten so bad that you’ve found yourself drooling over the idea of a new computer, even though your system isn’t that old, we’ve got some good news: you can get your whizzy speeds back with a little TLC. Computers generally start slowing down within 12 months, but it’s not because their parts are broken. And it’s not because they’re faulty. It’s not even because you have so many browser tabs open that you lose count. Slow computers have a number of causes, but the most common ones are easily fixed. Background programs Whenever your computer is turned on, it’s running programs in the background. You didn’t start them and they may not be essential to operation, but off they go anyway. You can’t even see some of them, they don’t have windows or anything to look at. A good example is your antivirus program. You don’t need to see it all the time, but you know it’s running in the background, protecting you. Over time, more and more programs might slip into the background and casually suck up your resources, like iTunes helper, Acrobat updater, Cortana listening, Skype or Spotify. We can speed up your system by setting these background programs to run only when you need them, or remove them completely. Application bloat How do you improve last year’s version of a program? Add more features! The problem with this is the applications become bloated with features you may not need (or even know about), but that keep needing more and more resources. Each time the developers review their programs, they assume you’ve bought the latest and greatest computer and can run whatever they release. This means a slow computer can sneak up after an auto-update. You may not even know the update happened, just that your computer is suddenly making you very unhappy. Eventually, your system grinds to a halt. We can remove unused applications or increase your computer power as required. Slow hard drives Your data is stored on a part called the hard drive. It’s usually a mechanical type that works like a record player, with a spinning platter and a ‘needle’ reading it. If your data is spread out across lots of places on the platter, the hard drive head 'needle' has to go backwards and forwards thousands of times just to retrieve a single file. Unsurprisingly, that takes more time to bring up your file. We can optimize your data to give the hard drive head a break, but an even better solution is to upgrade to an SSD. That’s a Solid State Drive that stores data in memory chips, like your USB drive, and has no moving parts. Without the physical need to move a hard drive needle, your computer can access data much faster. Read more about the differences between HDD and SDD here. Unfortunately, once your computers starts slowing, for whatever reason, the problem only gets worse. The background programs will continue to multiply, the bloat keeps coming, and the hard drive begs for relief. Rather than buy a whole new system though, it’s completely possible for your current computer to go back to being lightning fast – and for a fraction of the cost. Give us a call at 570.235.1946 or visit our Contact Page if your computer is running slow...
07 Aug Boost Your Email Impact With These Smart Strategies
Boost Your Email Impact With These Smart Strategies Boost your email impact with smart strategies. Most small businesses rely on email as their preferred form of communication. Either internally or externally to clients, customers and suppliers, email is the go-to format we’d be lost without. Our love affair with it is no surprise – it’s quick, simple and provides a paper trail. But its convenience doesn’t always mean relaxed. In fact, poor email communication can hurt your reputation and cost you customers. Here’s how to be smart with your business email: Manage your inbox Your inbox is only for items you still need to access. Once you’re finished with an email, you should delete it or archive it. If you were to imagine your inbox as physical letters, you’d never let it grow to a 6-foot high stack of chaos. Instead, you’d either throw them out or do the filing. It’s not hard to identify which ones to keep for reference, so create inbox folders to sort them accordingly. As emails arrive and are actioned, move them to the relevant folder or the delete bin. Read more about maintaining business email inboxes here. Write professional messages Stepping across the line from casual to careless is easy if you skip the basic elements of good business writing. Grammar will always be important and the sentence structure of your language hasn’t changed. All email programs include a spell-checker, many of which draw attention to errors immediately, so there’s really no excuse. Typing in all CAPS is seen as yelling, and breaking your text into paragraphs makes your message so much more readable. One last thing before you click send, quickly glance over your email to make sure your tone is appropriate and no mistakes have snuck through. Embrace the subject line Many emails are missed because the subject line was empty or meant nothing to the receiver. Writing these attention-grabbing nuggets can be tricky, but if you simply summarize the message, you’ll do fine. Just remember to keep them under 5-8 words so they fit on mobile displays. Be smart with attachments Keep attachments small – under 2MB – as they can clog up the email server. For larger attachments, share the file location as a link using cloud storage. When you’re sent an attachment you’d like to keep, save the file and then delete the email. And as always, be careful with unexpected attachments, especially from unknown senders. It’s more important than ever to scan all attachments with an antivirus before opening. Keep your CC/BCC under control The carbon copy (CC) and blind carbon copy (BCC) let you send the email to additional stakeholders, more as an FYI than anything else. As a rule, use BCC if you’re using an email list or privacy is an issue. But before you add extra people to the email, make sure the email IS relevant to them. There’s nothing worse than being stuck in a pointless email chain! Call us at 570.235.1946 or visit our Contact Page for help with your business email....
31 Jul 4 Simple Tips to Keep Your Internet Banking Safe
4 Simple Tips to Keep Your Internet Banking Safe Online banking has boomed in the past few years to become the new norm. Branches are out and apps are in. Half the time when you visit a branch, you’re steered towards a computer for a DIY transaction – with optional assistance. But is internet banking really safe? You’re always told to keep your financial details private, but now also to jump on board the online banking train – talk about a push/pull scenario! The good news is you CAN bank safely online with a few simple precautions. Always type in the website address Many attackers will attempt to trick you into clicking a fake link to your bank website. Usually sent as a ‘phishing email’, they’ll claim there’s a problem and ask you to click through to your bank and correct it ASAP. The link points to a fake website that looks almost exactly like your real bank site and is recording your private account info. You can avoid scams like this simply by accessing your bank by manually typing in the website or using a bookmark. Read more about phishing emails here. Avoid public computers and networks Jumping onto a PC at the library or mall might seem like a quick and easy way to check your account, but public computers are often targeted by scammers. In just a few moments, they can install keyloggers to record usernames, passwords and other private data, then sit back as all future user details are emailed to them. The same problem applies with free, unsecured Wi-Fi. You’re better off using an ATM or a data-enabled smartphone. Use a strong password with 2- factor authentication Create a unique password for your online banking, something you’ve never used anywhere else. Mix up words, numbers and symbols to create a complex password that can’t be guessed easily. Avoid giving attackers a head start with data they can find on Facebook, like kids names, pet names, birthdates, etc and really think outside the box. And of course, never write it down anywhere near your wallet, phone or computer. If remembering is likely to be an issue, you might like to consider a secure password manager app. Many banks will also help boost your security with two-factor authentication, sending random codes to your phone (or a special LCD device they provide) to verify any activity. Check page security before entering data Finally, take a micro-second to spot the small padlock icon before you enter any data. You’re looking for a padlock appearing as part of the browser itself, not just an image on the webpage. It will be either in the bottom corner or next to the URL. The address will also start with httpS:// instead of http://. If you don’t see these things, the page is NOT secure and you shouldn’t log in. Would you like us to give your computer a new lease on life? Give us a call at 570.235.1946 or visit our Contact Page...
24 Jul When is Your Business Ready to Move to the Cloud?
When is Your Business Ready to Move to the Cloud? Is your business ready to move to the cloud? Cloud computing has become a natural step in business growth, thanks to the numerous (and continually growing) benefits. More and more applications are coming out in web-based form and staff are exceptionally comfortable with this type of change. So when is the right time to move your business computing to the cloud? Many businesses are facing this question now that cloud computing has become a mainstream norm. After all, you’ll be able to roll out new apps in days, not weeks, and nobody ever says ‘no thanks’ to increased security and efficiency. Like any strategic business decision though, timing is everything. Here’s how to assess your need before you make the switch: Age of servers and workstations If your workstations and servers are reaching their end of life and a large capital investment is coming up, you’ll be able to minimize the expense by moving to the cloud. You may even be able to skip certain upgrades completely. Your staff will still need devices to access the cloud data, but you’ll have a lot more flexibility in your choice and they won’t need to be as powerful. This can be a huge cost saving made in just moments. Need for remote and mobile access Many businesses are growing while on the move, with a mobile workforce needing to access files from anywhere at any time. This could range from moving around the one location, between offices or even working from home. Forget frustrating connections and lost productivity, cloud computing allows staff to work securely and efficiently from any location with internet access. Current support setup If your business currently outsources all your network management, you’re perfectly suited for the move to cloud computing. Network maintenance and monitoring becomes a non-issue, handled 24/7 as part of your cloud service. Network efficiency just keeps rising too, as your cloud provider is always improving their systems. You’ll find problems are fixed before you knew they existed, and server downtime becomes a thing of the past. Need for predictable IT costs If it feels like IT costs can spiral out of control at times, challenging your budget and patience, cloud computing will seem like a dream come true. When you make this shift, you’re moving from a capital expense to an operational one – server and system replacements are no longer your concern. You’ll be able to budget for IT costs in advance, knowing no blowouts are hiding around the corner. Monthly costs are known and (usually) capped based on what you use, leaving your cash flow much relieved. Today’s cloud computing is more advanced, secure and priced more competitively than ever before. At its core, cloud computing is purely about doing things better, and it can have a massive impact on your profits, productivity and even staff satisfaction rates. If your business requires a robust, always available infrastructure with easy monthly costs, it’s time to take a serious look at your cloud computing options. We offer a variety of cloud services to help your business. Give us a call at 570.235.1946 or visit our Contact Page to discuss how we can improve your business IT....
17 Jul How to Make Your Photos Last A Lifetime (and Beyond)
How to Make Your Photos Last A Lifetime (and Beyond) Digital cameras are great, and thanks to smartphones, we have one with us almost all the time. We're taking more photos than ever before, and building a lifetime of digital data. But despite the enormous value of these photos and videos, most people don't have a backup. It's time to shine a light on this essential task and make it a regular habit before those precious memories are gone forever. If you asked someone what possession they'd save from a house fire, most would say photos. But with digital photos, you don't need a fire to lose everything. Digital photos can disappear in the blink of an eye with hardware failure or theft. There's no warning, no smoke alarm, and without a contingency plan there is no chance to recover the data. It's time to get set up with a true backup system. Is one copy enough? You might think saving your information to an external hard drive or flash drive is enough. You're right, it's better than nothing, but since the data is stored in only one place, this isn't a backup - it's just storage. That drive could fail at any moment, perhaps from age, malfunction or plain old theft. Often enough, that drive even becomes lost over the years, put somewhere 'safe' and promptly forgotten! And with the way technology is moving, accessing that data in 5 years might even bring up compatibility issues ñ some newer computers don't even have CD/DVD drives, yet hundreds of thousands of homes would still have photos stored on a disc. Two copies? You might have your extra storage drive as backup and keep a copy on your computer. This is a better solution, and how most people store their data, but it still isn't enough. While you're protected against device failure, that house fire is going to take both copies up in flames. Thieves grab the external drive while they're bundling up your computer too, so again, you'd be left with zero copies. It's close, but it's not a true backup system. The rule of three We subscribe to the backup rule of three, also known as the 3-2-1 Backup Rule. Just reading this may sound like overkill, but tech is fragile and device failure is a constant risk. We recommend keeping one copy on the computer/device, another on an external drive, and a third copy as last resort tucked safely away in the cloud. If the day comes that you need your data back, it's ready and waiting in perfect condition. Cloud technology also means your data is far away from any potential fire or flood, it's secure and with the right provider, guaranteed against loss. There's a saying in the IT industry: "There are two kinds of people: those who backup, and those who have never lost all their data". No matter what the cause of your data loss, it always has a deep impact, particularly when it comes to precious data. While re-creating some homework or the family budget might just be inconvenient, there's no way to recreate photos once they're gone. It's a loss that hurts for a long time, but it's also so very avoidable. If you value your data, give us a call at 570.235.1946 or visit our Contact Page...
10 Jul What is the Cloud? Where is it?
What is the Cloud? Where is it? What is the cloud? There has been a ton of talk about the cloud. Cloud this, cloud that. It’s okay if you don’t know, most people don’t understand it and even some tech people tend to wave their hands towards the sky when trying to explain it! Since it actually has nothing to do with the white fluffy things in the sky, let’s lay it all out: Cloud computing is about storing and retrieving your data (personal or business) within your own piece of the internet. Access it from anywhere. Colleagues in different locations can even collaborate on documents in real time. If that all sounds a bit futuristic, think about how an email service like Gmail works. Emails are stored on the Gmail server, not on your hard drive or device. Your read/send/receive changes are applied instantly, remembered for next login. This is a form of cloud computing. So is Netflix, where you can stream movies and TV shows on demand. Video is stored on a computer somewhere else in the world, and sent to your device in tiny packages. Netflix remembers what you watched, where you got up to, and if you’re hopping from one device to another, it still has it all ready to go. Where is ‘cloud’ data stored? Good question. And it’s why the term ‘cloud’ causes so much confusion. Companies who offer cloud storage have huge warehouses dedicated to holding servers. By huge, we mean HUGE. In terms of location, the US and UK are popular server farm locations, but the company could also have copies of your data stored elsewhere in the world. This is so they can fulfill their redundancy guarantees – if disaster hits one location, the other still has a copy. Having additional locations and copies also increases the speed of access. With some companies, you can choose your preferred location. Data doesn’t have to travel quite as far across the world, increasing speed even further, which of course, saves time and money. Collaboration, security, redundancy, AND savings? We’d call that a win. Ready to take advantage of cloud computing? Give us a call at 570.235.1946 or visit our Contact Page...
03 Jul Everything You Need to Know About Facebook Privacy
Everything You Need to Know About Facebook Privacy Discussing Facebook privacy poses a challenge in balancing privacy and enjoyment. It connects friends worldwide but also shares information we previously considered private. Searching for people based on education, location, clubs, and relationships raises the question: when does it cross the line? When signing up on Facebook, your birthday is the first information collected. It's enjoyable receiving birthday wishes, but now it becomes public knowledge. However, when verifying your identity with institutions like banks, they often ask for your birthday. Password recovery systems may also inquire about your high school, assuming it's private knowledge. Unfortunately, you've inadvertently shared these details on Facebook. Oops! We've all heard stories of people who've lost their jobs after less-than-wholesome pictures or statements have gone public. If you have a reputation to keep, you definitely don't want pictures from last weekend's private party showing up, especially if you really let your hair down. While you can't control what others do with photos they take of you, you can control whether or not you're tagged in them. Fortunately, there are settings in Facebook that allow you to control who sees what information and what happens when youíre tagged. Despite what you may have heard or seen floating around in a Facebook share hoax, you do have complete control over your Facebook privacy, and it's easy to adjust. How to Check and Adjust Your Facebook Privacy Settings See what your account looks like to an outsider From your Facebook homepage, click your name on the blue bar at the top of the page. Click the three dots next to 'View Activity Log' and then select 'View as' Run a quick privacy checkup Click the question mark in the top right corner and choose 'privacy checkup'. Think about what you really need to share ñ do people need to know the YEAR of your birth or just your birthday? Your friends will still get the notification, and you'll still get the balloons. Edit advanced privacy While the checkup covers the most obvious info, you can go much deeper. Click the V-shaped dropdown to the right of the question mark. Go to settings and choose privacy. Adjust timeline and tagging In the privacy settings, you can explicitly control who can tag you, who can see or share the tagged content, and what shows up on your newsfeed. Read more about controlling your privacy on Facebook here. Tightening your Facebook privacy only takes a few minutes, but it can save you a whole lot of trouble in the future. If you need help with this, just give us a call at 570.235.1946 or visit our Contact Page...
30 Jun Should You Use Remote Support?
Should Use Remote Support Should you use remote support? If you’ve ever had a sudden computer problem, you know it can be very stressful. So much of our day-to-day life requires having access to a working computer. Homework, budgeting, bills, even browsing dinner recipes all have a degree of urgency that mean dealing with a broken computer isn’t comfortable for long. Your computer technician offers two options: remote repair or bring it in. Which is the best choice for you? Benefits of Remote Support Speed: If remote repair is a possibility, your technician can connect via the Internet and have you operational in no time. You might also choose to just leave it turned on in the morning and go to work as normal, while the tech logs in to conduct the repair, ready for your return. Without this option, you’d need to juggle time in your diary to drop the system off as most in-store techs only work 9-5. Many large-scale remote support services are even available 24/7, eliminating all unnecessary delays. Convenience: You get to skip the unpleasant tasks of unplugging the PC, untangling the cables and carting it into the repair store. Even then, once repaired, you’d still be privileged with carrying it back home and playing a game of which-plug-goes-where. Computers may be getting smaller, but they’re still heavy and fiddly! Laptops are designed to be moved around often and it may not be a problem to stop at the repair store, but traveling with a desktop PC requires a little more effort and a lot more inconvenience. Negatives of Remote Support Limited repair options: A remote connection can only repair certain software problems, not hardware problems. It’s impossible for the technician to swap out a failed part remotely, and unless you’re confident in your own repair skills, guided physical repair isn’t viable either. Occasionally the problem will also be outside the computer, perhaps a troublesome peripheral or connection. Your technician may be able to walk you through correcting some of these minor problems yourself, but most invariably require a physical call-out or taking your computer in-store. Connection speed: A slow or unstable connection will make a remote repair take longer and increase the difficulty of the task. The extended time impacts the cost for the call, and in extreme cases, can negate any benefits of skipping the physical inspection. Your connection needs to allow the technician to see real-time responses as if they were sitting there in person. Accessibility: If your computer won’t start or can’t connect to the Internet at all, your technician can’t log in. This includes seeing a ‘blue screen of death’, boot failure and Windows load failure. As much as they’d like to help you, being able to log in to your system is a vital step in the remote repair process. Remote support and repair is the ideal situation, purely for speed and convenience. As a bonus, in the event the remote repair is unsuccessful, it also means your tech now has a better idea of the problem and can speed up any on-site or in-store repairs. Remote support is the best option for many repairs and gets your computer working again with minimal disruption and lowest cost. Need a repair? Call us at 570.235.1946 or visit our Contact Page for rapid remote support....
28 Jun 5 Ways Managed Services Can Grow Your Business
5 Ways Managed Services Can Grow Your Business Managed Service Providers (MSPs) can help grow your business with a proactive approach to managing their technology without the expensive step of hiring an in-house team. Your MSP is essentially a collection of niche technology experts working behind the scenes to keep your data safe, generate solutions to IT problems and keep your software updated. Even larger businesses who already have an IT person will often call in an MSP when daily support becomes overwhelming or a specific certification is required. Let’s explore 5 specific business breakthroughs an MSP can give you: It’s extremely cost-effective: There’s only so much in the budget for IT and responding to events on a break/fix basis will quickly exhaust your accounts. An MSP works by getting ahead of problems before they occur – making equipment last longer, defending against costly security breaches and keeping the business up and running. Instead of calling for a repair at a high hourly rate, you get a wide array of expert services for one predictable monthly fee. You have access to multiple experts: Businesses usually end up adding extra tasks to an unqualified but enthusiastic employee’s workload, resulting in costly problems. With MSPs, you have access to many people who are experts in very specific areas, and your existing staff can focus on tasks within their job description. Speedy problem resolution: Downtime and business don’t mix, so your MSP will provide a reliable expert on call (usually with 24/7 options) to troubleshoot and resolve any problems. Much of the time, you can also skip the delay of an on-site repair with rapid remote support available in just moments. Fewer problems: A large part of your MSPs service is fixing problems before they happen. While fixing things as they break isn’t the worst approach to IT management, it generally means you’re also suffering productivity losses, downtime and losing money by the second. Your MSPs primary goal is to ensure these problems are avoided completely, through system monitoring and robust security measures. They’ll also make sure every important software update and security patch is applied immediately, closing breach points and keeping your business safe. Shared responsibilities: As your business grows, so will your IT systems. A good MSP is on top of what your future needs will look like and knows which products and infrastructure are suitable to help you get there. Your MSP doesn’t just monitor your system and repair as required; they share responsibility for your system. This means measuring, reporting, analyzing and optimizing, working with you to introduce new technologies and processes. Depending on your level of contracted services, your MSP can actually become a catalyst for growth. Sounds good, doesn’t it? With managed services, your business always has the maximum security against threats, downtime and productivity drops. But for the savvy business owner, it’s also a way you can afford to leverage cutting-edge technologies, with complete peace of mind and ongoing support. Boost your business with managed services. Call us now at 570.235.1946 or visit our Contact Page...
23 Jun 4 Important Reasons to Use Anti-Spam Filtering in your Business
4 Important Reasons to Use Anti-Spam Filtering in your Business Why use anti-spam filtering in your business? Remember when spam was obvious, and unless you desperately needed a special blue pill, it was easy to identify and ignore? Those were the days! The impact on your business would have been minimal, as spam was more an annoyance than anything else. Unfortunately, spam has matured into an aggressive threat, marked by sophisticated attacks and rapidly evolving techniques. It’s not just random electronic junk mail anymore and it’s putting a costly strain on your business resources. How Spam Impacts Your Business Spam now contains malware, with hackers sending cleverly disguised emails to your business. This is called "malspam." Once clicked by an employee, it infects your computer system (virus) or steals your private data (phishing). The malware can then spread across the entire computer network and beyond, including to your clients and vendors. The very fact that your employees must pause and examine every single link and attachment adds hours of lost productivity. Occasionally, spam is so convincing that only an expert would be able to visually identify it. Employees are also more likely to miss an important email, either not seeing it arrive at the same time as a spam attack or becoming overwhelmed with the sheer number of emails. How Anti-Spam Can Save Your Business Block threats: The spam filter’s purpose is to block the spam from ever reaching your employees’ screens. The threat is automatically identified and either held securely or immediately deleted. This is the best way to avoid activating spam malware, as it’s so easy to click through links in an email that seems authentic and important. The effects of that one spam click may be instantaneous or may lie hidden for months. Removing the email before it becomes a risk is a much better option. Filter legitimate emails: Real mail needs to be able to stand out and avoid the trash. Anti-spam filtering has sophisticated recognition abilities which block spam only and allow real mail to land safely in mailboxes. Meet data regulations: Many businesses are subject to strict privacy and data storage regulations, some more so than others. To continue operation, they have to meet conditions including always using spam filtering to reduce the risk of data breach. Protect your business reputation: You can see how uncomfortable CEOs are when they hold press conferences to admit a breach. They must acknowledge that they failed to protect client data, or that users may be infected with a virus. Not only do they then face financial loss, their business reputation takes a nosedive. Anti-spam filtering can ensure these types of scenarios don’t happen to you. Filtering has come a long way in recent years, with complex algorithms identifying and catching spam before it becomes a risk to your business. Real emails can now pass safely through without the classic catchcry of ‘check the spam folder’, and businesses can work with greater productivity and safety than ever before. You need email, but you definitely don’t need spam or the chaos it brings to your business. We can block spam and keep your legitimate emails flowing. Call us at 570.235.1946 today or visit our Contact Page...
21 Jun 6 Brilliant Ways Managed Services Can Work For You
Make Managed Services Work for You There are ways managed services can work for you. Wouldn’t it be great to know you could access the internet from every room in the house? Many homes are embracing the flexibility of multiple devices, but this comes at the cost of increased headaches. In effect, people don’t realize how complex their tech setup has become. Residential homes commonly have 4 mobile devices, 2 tablets, a desktop or laptop, printer, smart TV, media streamer, and game console, all of which need access to the same secure internet connection. For that reason, using managed services has the benefit of providing one, predictable bill for every part of your technology services, including: Managed Services Advice and setup: Our experts love to talk tech and can help you make product decisions, plan and create your ideal network environment – building in all the parental controls and security your unique situation needs. In effect, they'll help educate your family on best practices, cyber safety, and common threats. Remote Support: Save time and energy if services goes wrong, our experts can securely log in to remotely diagnose and repair many issues. Backup: Never worry about losing personal files, photos, video and music if your device is broken or stolen. Our experts ensure everything that’s important to you is backed up regularly. Maintenance: Devices need regular maintenance and cleaning. This extends the life of your device greatly and has the added benefit of making it run like new again. Security: Every device under your managed services IT plan will be automatically monitored for security issues and updated regularly. In detail, our tech experts will ensure your network is secure, protecting you and your family on autopilot. Cloud: We’ll make sure you have access to all your files, no matter which device you’re on, giving you true digital flexibility and (a safeguard against forgetting homework!). With new connected devices finding their way into homes each year, it’s important to ensure your network grow with security at all levels. Remember, it only takes one unprotected device to let the malware in. Therefore, our managed IT services will free you from worrying about security and maintenance. Find out how Managed IT Services can help you by calling us at 570.235.1946 or visit our Contact Page...
19 Jun Why Your Windows Updates Are More Important Than Ever
Why Your Windows Updates Are More Important Than Ever Windows updates keep devices secure with the latest security updates. Stories about hackers and virus attacks seem to be making the news almost every day, and many of these news stories include tips on how you can avoid becoming a victim. One common theme among these tips is making sure your Windows operating system up to date. Every day hackers are trying to figure out new ways to break into Microsoft Windows and once they do find a weakness, they try and find a way to spread it. This could be through a malicious email attachment or even something that spreads without your involvement. Windows Updates Explained Whenever Microsoft discovers a potential flaw, they push out a small piece of software to all Windows computers running a supported version. If set correctly, your computer will check if there’s any updates or patches and install them automatically. In new versions, this usually happens when you’re shutting down or starting up, and doesn’t impact your experience at all. Unfortunately, some users will manually disable or delay their updates, creating a risky situation. The update may include security patches, drivers or a simple tweak to address bugs or issues with Windows. Sometimes, they even include new features or applications to improve the stability of your operating system. They’re a good thing! Not All Versions Get Updates Some older Windows operating systems are no longer supported, which means unless there are extenuating circumstances, Microsoft won’t issue any new updates. Not a single one – generally, if cyber criminals discover a flaw after support ends, they’re free to exploit it. For example, Windows XP support ended in 2014, and Windows Vista just ended in April this year. The moment an operating system is retired it becomes a playground for cyber-criminals. It’s not just Microsoft walking away from these old versions either. Third party software like the Google Chrome browser will still work, but they’ve also stopped supporting old versions with crucial updates and patches. It might seem like everything is working fine because your anti-virus isn’t pinging in alarm, but it just becomes a case of risk, upon risk, upon risk. What to do with older Windows As much as you’re comfortable with your older version of Windows, each time you boot up you’re exposing your system, important files and entire network. It only takes one weak entry point in the chain to allow malware into all connected devices. That could mean your photo storage, media center or even smart appliances. It’s not worth it - if you’re running Windows XP or Vista (or older), you need to update to a more modern operating system ASAP. Give us a call to upgrade your computer. We can also monitor your system remotely and apply your Windows updates with our Managed Services packages, ensuring you are always up to date and protected. Give us a call at 570.235.1946 or visit our Contact Page...
16 Jun Internet Lingo 101: Cheat Sheet for Beginners
Internet Lingo 101: Cheat Sheet for Beginners Having an internet lingo cheat sheet for beginners is important. The Internet is growing and evolving so fast even the dictionary has trouble keeping up. Here are 12 suddenly common terms that are helpful to know. Browser A browser is a free piece of software that lets you view web pages, videos and other online content. It’s a core requirement of going online, as it converts the computer languages HTML, Javascript and XML into human-readable form. The most popular browsers in 2017 are Google Chrome, Safari, Firefox and Microsoft Edge*. (*Internet Explorer has been superseded and is no longer recommended due to security concerns) Email Electronic Mail (formerly spelled with a hyphen: ‘e-mail’) is typed messages sent from one person/business to another via the Internet. It’s delivered almost instantly and then waits patiently for the recipient to open and read it. You’ll need a webmail service (e.g. Gmail) or installed software (e.g. Outlook) to read, write and send, but you can also set your smartphone up for this. Most emails are in the form of letters, newsletters or catalogs, often with a more casual tone. Email can include text, links to the internet and images, but not video/sound. Encryption Before important data is sent over the internet, it’s scrambled to turn it into gibberish that means nothing to anybody who might intercept it. Unless there’s been a massive security breach, only the sender and intended recipient will have the decryption key to turn it back into readable data. You don’t have to encrypt your own data as it happens automatically. Your email provider and important places like banks and online stores have digital security systems that take care of the encryption/decryption for you. Firewall A firewall is a security measure designed to act like a door bouncer to your network. When an unauthorized user attempts to gain entry, the firewall blocks their path until it’s checked them out thoroughly. If there’s anything suspicious, the firewall refuses to let them in. HTTP and HTTPS These are acronyms for the rules of how data is transmitted to your computer screen. The actual mechanics are incredibly complicated, but the terms have one very important distinction: HyperText Transfer Protocol (HTTP) means the images, text and links should appear in your browser. HyperText Transfer Protocol Secured (HTTPS) means the page has an added layer of security to hide your personal information from hackers. Data sent through pages with this prefix is securely encrypted before transmission. IP Address Every device that accesses the Internet is assigned a unique IP address to identify itself. It’s used to make sure when you request a page or document, it’s sent to you – and not someone in Alaska. Your IP will look something like ‘202.9.64.55’ and may be referred to as fixed or dynamic. ISP Your Internet Service Provider (ISP) is the company that allows you to connect to the Internet. They’ll also offer extra services like email or web hosting. It’s impossible to bypass the ISP level and connect directly to the Internet. Malware A broad term to describe viruses and malicious software from hackers. Malware can manipulate you into paying money, take control of your computer, steal your private details or break your computer in some way. Instead of listing each specific threat, you’ll commonly see them lumped together under ‘malware’. Router The traffic system for your network, connecting computers and devices within the home and acting as a defensive gateway to the Internet. These hardware devices can be wired or wireless, and allow you to share one Internet connection amongst all the computers/devices in your home. Social Media A broad term to describe all the websites and applications that let you share and interact with others online. To fit this umbrella, the site needs to allow user profiles, live updates and the ability to add friends/followers. The most common social media applications are Facebook and Twitter. Spam and Filtering Any unsolicited messages sent over the Internet, usually in bulk, are called spam. Usually, it’s electronic junk mail, but it’s also a technique hackers use to trick people into clicking links to their malware. Email applications are reasonably good at identifying spam and should shift it automatically to a spam folder before you see it. Occasionally, the filters get it wrong and you may find a relevant email needs to be dragged back to your inbox. URL Each website has a unique address on the web known as a URL (Uniform Resource Locator). URLs commonly end in .com but can also end in a country specific extension like .com.au or .fr, or more recently, in new and exciting extensions such as .xyz or .me Need more consultation on technology topics? Call us today at 570.235.1946 or visit our Contact Page...
14 Jun Cyber Security: 4 Ways to Travel Safe For Business
Stay safe from cyber attacks while traveling for business. Managers, owners, and employees are all embracing the flexibility of working while traveling, making it the new global norm. While you were in the office, you were protected by professionally designed firewalls, security infrastructure, and robust software. As soon as you step away from the building, those protections disappear, leaving your device and the data inside at risk. Cyber attackers love to collect any data they can obtain, often preferring to hack first, assess value later. Almost all data can be sold, including your personal details, those of your clients and suppliers, as well as your proprietary business data. The information stored on your device is usually worth much more than the device itself. Here are 3 ways a hacker will attack: Flaunting Opportunity: Whether your employee left their laptop at a café or a thief stole the device, the outcome is the same – that device is gone. Hackers will take advantage of any opportunity to gain access to a device, including taking them from hotel rooms and even asking to ‘borrow’ them for a few minutes to install spyware. Spoofing a Wi-Fi Hotspot: We’ve all come to expect free Wi-Fi networks wherever we go. Hackers will take advantage of this trust to create their own free, unsecure network, just waiting for a traveler to check a quick email. Intercepting an Unsecure Network: Hackers don’t need to own the Wi-Fi network to steal content from it. Data traveling across an unsecure network is visible and available to anyone with the right software. It’s okay, you don’t need to lock all employees inside the building or cancel all travel plans. Taking these four precautions will increase cyber safety and help protect your business data while on the go. Create backup before travelling: In the event your device is lost or damaged, you can replace the device with a new one. Don’t use public Wi-Fi: Wait until you have access to a secure network before going online. Use passwords and encryption: Secure your device with a password or full drive encryption. Act fast after loss: If your device is lost or stolen, immediately notify the appropriate people. This includes your IT provider, your bank, and any staff who need to be aware of the breach. Need help with mobile cyber security? Call us at 570.235.1946 or visit our Contact Page...
12 Jun How Much Could A Ransomware Attack Cost You?
How much could a ransomware attack cost? Have you ever thought about how much your data is worth? Cyber attackers target valuable information like client databases, accounting software, inventory management, and intellectual property. The WannaCry ransomware outbreak made businesses rethink the value of their data and the consequences of such attacks. Ransomware attacks typically require payment ranging from $150 to $600 for file release. Meanwhile, new client calls are still coming in and you may find yourself unable to operate with your systems down. Paying the ransom or restoring from an unaffected backup seems like a quick fix, but it doesn’t end there. There’s still the downtime involved to restore all your data – possibly days – and that’s a lot of lost productivity. Plus, if word gets out that your data has been compromised, you may find confidence in your business plummets and your existing clients head elsewhere. That $150 ransom may end up costing well over $150,000! Prevent Ransomware Attacks on your Business Keep your systems up to date: WannaCry took advantage of a flaw in older versions of Windows, one that was since patched by Microsoft. But to be protected, businesses had to be up to date with their patches AND be running a supported version of Windows. Delaying patches and updates puts your business at risk - we can help you update automatically. Lock down employee computers: Very few staff will require full administrator access to your business network. The higher their level of permissions, the more damage a person can do – either accidentally with a whoopsie click, or by inadvertently installing malware. By locking down your employee computers, you have a better chance of containing a malware attack to non-vital systems. Our experts can design an access management plan that gives you best of both worlds: flexibility PLUS security. Educate your workplace: Most employees believe they’re being cyber-safe but the reality is quite different. Many malicious links and embedded malware have become hard to spot in an instant – which is all it takes to click and regret. We can work with your staff to establish procedures around checking links for authenticity before clicking, awareness around verifying the source of attachments, and the importance of anti-virus scanning. We’ll help get the message through! Have a solid backup plan: When ransomware hits, a connected backup = infected backup. Unfortunately, synced options such as Dropbox immediately clone the infected files, rendering them useless. The only safe backups will be the ones both physically and electronically disconnected, with systems designed to protect against attacks like this. Our experts can set you up with a backup system that makes recovery a breeze. Be proactive: The best way to avoid the financial cost of a ransomware attack is to prevent it from happening in the first place. Remember, many businesses were able to watch WannaCry from the sidelines, completely unaffected and seizing opportunities while their competitors were down. Our managed services can help protect your business against the next cyber-attack. Call us today at 570.235.1946 or visit our Contact Page...
09 Jun Does Dropbox Make Sense For Your Business?
Does Dropbox Make Sense For Your Business? It seems so easy! Drag your files into a Dropbox folder and you’ve got yourself a file sharing system that brings your business in line with modern expectations. But then again, maybe not. Dropbox has grown to become one of the main file sharing and cloud storage solutions of choice. In some cases, sticking with the familiar blue box can provide good value, and of course, it never hurts when your staff already know how to use your software. In other cases, you’ll need to consider alternatives designed to meet your needs more explicitly. When Dropbox is a Good Choice Micro-sized: If your business is small with no more than a handful of employees (or none); No sensitive information: This includes accounts, customer details, vendor, staff or proprietary data; plus Nobody ever accidentally deletes anything: Dropbox is a syncing service, which means when a file is deleted, it deletes it from all machines. By the time you realize the file is missing, it may be too late to recover it. If you’re thinking those attributes sound more like a fictional business, you’re not far off. Somehow, Dropbox’s popularity in the consumer sphere has snuck into business environments, despite the risks. Key amongst these is the fact that Dropbox is designed for syncing, NOT backup. This means while your data is sprawling across all connected devices, it’s a mirror of the source only – when you delete or change the original file, the Dropbox version immediately syncs with it. When Dropbox is a Bad Choice In some cases, this can spread malware between your connected devices and put all of them at risk. Your business also misses out on important security controls, such as user-level access control and password protected links. Rather like a free-for-all, the shared files are sitting there available to anyone with either a connected device or an unsecure weblink. You’ll also miss collaborative editing, losing out in productivity and data resilience as multiple employees overwrite each other simultaneously, with no record of who even opened the file, let alone changed it. If Dropbox makes sense for your business, there’s no reason to change. But if it’s clearly not a good choice for you, there are multiple corporate grade syncing solutions. These are designed for business with security, encryption and collaboration controls built in. Rather than the easiest solution which may pose a risk to your business and digital security, consider implementing a scalable solution that meets all your needs. Call us at 570.235.1946 to discuss syncing solutions for your business or visit our Contact Page...
07 Jun How Many Good Battery Habits Do You Really Have?
Batteries are rarely talked about. The truth is, they’re a miracle of engineering that gets taken for granted when full and cursed when flat. If it feels like your battery is running out faster, you might be right. Modern lithium-ion batteries in phones and laptops wear out over time, unlike older battery types like NiMh. Fortunately, extending your battery life is easier than you think! Which of the following GOOD battery habits do you have? Good Battery Habits Charge whenever you can: Lithium-ion batteries don’t like being charged all the way then drained down to 0%. No wonder, it even sounds exhausting. Give them a little charge here and there, and they’ll be happy. Leave your laptop plugged in all the time: You can’t over-charge the battery. The laptop also helps out by cutting the flow of power when the battery registers as fully charged. Watch for overheating: If you can, remove your laptop battery while charging, because while it won’t overcharge, it may overheat. You might also consider removing the battery if you’re using your laptop plugged in all the time. You might lose data if there’s a power outage, but overheating is a far more common occurrence. It’s been proven to degrade battery life. Check your vents are clear with good airflow, and if necessary, help it out with a cooling laptop stand. Leave your phone plugged in all night: Just like your laptop, your charger knows to stop when the battery is full. Those chargers do generate heat though, so make sure you have enough airflow around both charger and phone, and never sleep with it under your pillow. Charge batteries before storing: Make sure to give them a half charge before storing. They’ll naturally discharge and age over time, so this gives them a fighting chance to still be viable when you need them. Keep your cool: We know to avoid water with our phones, but we’re less careful about exposing it to heat. This includes leaving it in your car all day, placing it on top of your PC, or even in a sunny spot by the window. Wireless and rapid chargers can also be an issue, as the amount of heat they generate will affect your battery. How did you do? Is keeping your lithium-ion battery happy easier than you thought? Your battery will wear out over time, but you can push that day a few years into the future if you remember to keep it charged and keep it cool. Having battery issues? We can help! Call us at 570.235.1946 or visit our Contact Page...
05 Jun WannaCry Ransomware Explained: Is Your Business At Risk?
WannaCry Ransomware Explained: Is Your Business At Risk? You’d be hard-pressed to miss May’s biggest headline, the WannaCry cyber-attack sent shockwaves around the globe. Businesses of all sizes and even police departments found themselves under attack without warning. Among the most prominent victims were many NHS hospitals in the UK, affecting up to 70,000 individual devices such as essential MRI scanners and blood-storage refrigerators. But by the time it hit the news, either your system was protected, or it was infected. Here’s how it all went so wrong. What is WannaCry? The WannaCry cyber-attack was a type of malware called ‘ransomware’. Just like the name suggests, it’s actually a demand for money. Like all ransomware attacks, WannaCry encrypts your files and holds them hostage until you pay. In this case, the price was set at $300, payable with internet currency Bitcoin, and you had 3 days to pay before it doubled. If you didn’t pay, the ransomware threatened to delete your files permanently. It’s yet unknown how much money the WannaCry hackers have earned with their latest attack, but you can be sure plenty of people have paid the ransom. Even the FBI recommends paying the ransom, especially if the ransomed files are of a sensitive nature or weren’t backed up. How It Spread So Fast It seems WannaCry may be a ‘computer worm’ that self-replicates and spreads, rather than a phishing attack that needs to be activated with a click. So far, no common trigger has been identified, as is normally the case with phishing links. WannaCry moved rapidly from system to system, spreading out through the entire network, including all connected backups and storage devices. At the same time, it spread out to infect other networks, who then spread it further, and so on. Given the nature of the internet, it was everywhere within hours. Why Some Businesses Were Safe WannaCry could ONLY infect systems that have fallen 2 months behind in their Windows updates. It was created to take advantage of a specific vulnerability in Windows, one which Microsoft patched months ago. Without that patch, the ransomware could waltz right past the firewall, past the anti-virus and directly into the system (the NHS were reportedly running Windows XP – no longer supported). Those running Windows 10 or a fully patched, recent version of Windows were completely unaffected. It just goes to show the importance of staying up to date. We haven’t seen a second spike in WannaCry attacks yet, but that doesn’t mean there won’t be one. A quick update could protect your business from weeks of downtime and lost revenue, making attacks like this a non-issue. With our managed services, we can make sure you stay up to date – and protected. Give us a call today at 570.235.1946 or visit our Contact Page...
05 Jun How To Keep Your Tech Squeaky Clean
How To Keep Your Tech Squeaky Clean Our tech is something we use every day, but did you know it’s also the most disgusting? Your screen may look clean, but studies show that a mobile phone can be 18x dirtier than a public restroom – ew! It gets worse. That keyboard you tap at while eating your morning toast? It’s probably the biggest bacterial threat in your house, with about 20 000 times more germs than a toilet seat. It’s not just sickness we’re up against, because as dust builds up inside gadgets, they also slow down, malfunction or overheat. Your device essentially chokes on ick, as vents and filters are clogged by sucking in pet hair and floating debris. Here’s how to clean your essential tech items without damaging them: Skip the Household Cleaners Most cleaning products are too harsh for our technology and can end up causing permanent damage. You want something that can kill germs and remove everyday grime, without scratching or leaving behind a scented residue. Your best bet is Isopropyl Alcohol. You’ll find it in the first aid section of supermarkets and pharmacies, or at the hardware store. Power Down Completely Turn your tech off all the way, not just sleeping, and unplug from any power sources. Switch wireless keyboards, mice, etc off underneath or remove the batteries. Remove any Cases or Covers Undress your device as much as you can, but leave screen protectors on (unless there’s grime underneath). If your screen protector needs replacing, have a new one ready to apply. Grab a Microfiber Cloth Dampen the cloth with Isopropyl Alcohol and wipe screens and external surfaces gently. Older build-up may require extra effort. Go Deep You can use a toothbrush or cotton tip to clean between most crevices, but some areas will need a bit more ‘oomph’ to clear. You’ve probably seen people use vacuum cleaners on their keyboard, but these are often TOO powerful and may suck keys or internal parts loose. They also generate damaging static electricity. Another option is to use a tech-specific vacuum, but these are usually underpowered. Insider Tip Use a can of compressed air to blow the dust out. You can get these from many stores and they come with a long nozzle so you can really get in and direct the pressure. You’ll be surprised what flies out, so it’s best to do this outside! We don’t recommend using compressed air on your computer’s internal fans though, as this can make them spin too fast and damage them. How often you clean your tech is up to you and your lifestyle. But it’s a good idea to blow out computer internal dust at least twice a year and wiping your tech down 1-2 times per week will definitely reduce germs and grime. Is your computer making too much noise or getting too hot? Give us a call at 570.235.1946 or visit our Contact Page and we’ll clean the internals for you....
27 Feb Why Your Business Needs A Strong Firewall
Why Your Business Needs A Strong Firewall You may not be storing military secrets or running a billion-dollar empire, but your business is still an attractive target for hackers. Enter the firewall - a guard standing at the door of your network to stop the bad guys from getting in. A surprising number of businesses are operating without a firewall. For most, it’s a risk they don’t know they’re taking because they assume all systems have built-in protections. A firewall is a type of hardware or software that acts as a protective shield between the computers on your network and cyber dangers. Data passes through at lightning fast speeds, invisible to the user experience. What Does Firewall Do? Filtering: A firewall looks for known viruses, phishing emails and spam, and then blocks them before they enter. Business firewalls also monitor data in both directions. When a computer goes online, data coming in and out is inspected. If it doesn’t pass the test, the firewall instantly blocks it and records the details in a log. Performance: You can use your firewall to set network traffic priorities. For example, it can make sure a Skype call gets all the resources it needs to allow for flawless video and voice quality, while someone watching YouTube videos at the same time will receive reduced resources. Rules can be set to allow certain applications to be treated as a higher priority than others. You can tailor your network performance to meet your unique business needs. Management: Business firewalls allow you to see who’s doing what and when over your network. You can create rules for specific users, devices and times. You might allow your employees to access Facebook during lunch breaks only, while keeping it unblocked for you or your marketing team throughout the whole day. Thorough logs are kept automatically and can be used to troubleshoot problems. For example, your firewall logs might show that a computer inside your network connects to a low-income country at 3am each night, which would certainly be worth investigating. Connection: A strong firewall allows your remote workforce to access your servers with ease and security. Remote work arrangements are growing in popularity and necessity, often requiring server access at a moment’s notice. You can set your firewall to authenticate the identity of users before allowing access, and create a virtual private network (VPN) that keeps any transferred data safe from interception. We install, configure and manage business firewalls - Call us at 570.235.1946 or visit our Contact Page ...
20 Feb How to Make Computer Issues A Thing of the Past
How to Make Computer Issues A Thing of the Past Computer issues can be a thing of the past. Computers have a habit of dying at the worst possible time. We’ve combined our repair services with preventative measures to ensure this doesn’t happen to you. Our managed IT services can remotely take care of all the computers in your house or business. Preventative Maintenance Anti-virus always up-to-date: While many homes have anti-virus software installed, they don’t often have the latest virus and threat definitions. These systems are at risk every minute they spend online, as the anti-virus simply will not pick up and stop an unknown threat. New viruses and hacking threats arise every day, and there are entire companies dedicated to creating anti-virus updates to catch them. We can make sure your anti-virus definitions are always up-to-date, keeping your computer secure against even the newest viruses. Software patches: Hackers like to spend their time figuring out new ways to break into computer systems. Software companies like Microsoft and Apple release regular patches to close these security holes. Patches should be applied automatically. However, we often find that isn’t the case – patches didn’t download, were canceled or produced an error. Our services involve remotely checking that each patch is applied successfully. Early failure detection: Some parts in your computer send out alarm bells when they’re about to die. We monitor these and advise repairs as required. Data protection: Hard drives which store your information do eventually wear out, but they’re one of the parts that send out early failure warnings. We can monitor this and give you ample warning so that you have time to back up your important files. When it’s time, we’ll work with you to arrange drive replacement, making sure to either clone or re-install your operating system, whichever suits your needs best. Tune-ups: Even the most cared for computer will slow down over time. Hard drives become cluttered, operating systems corrupt and ghosts of uninstalled programs still remain. We can remotely schedule and run a regular maintenance routine that will keep your system running in top condition and lightning speeds. Our managed IT service happens entirely behind the scenes, so there is no disruption to your experience. You simply enjoy the benefits of having your own IT specialist team at one flat, low cost. We fix problems before they occur. Try managed IT services today by calling 570-235-1946 or visiting our Contact Page...
13 Feb Should You Buy A Consumer or Business PC?
Should You Buy A Consumer or Business PC? Before you buy a pc, it’s important to consider whether your best bet is to get a consumer model or one built specifically for business use. You’ve probably seen business computers with the same brand name that you have at home, but that’s where the similarities end. Investing in the right system now will pay off long term, saving you time, money and a whole lot of frustration. Here’s what you need to know to make the best choice for your business and budget. Business-class Features When you invest in a computer, you want certain inclusions built-in and ready to go. For a business, those include features that will make your network more secure and staff more productive. For example, fingerprint readers, remote desktop software and data encryption tools. The operating system that comes pre-installed on a business-class computer will also have features the consumer options don’t, including the ability to join corporate networks. Computers designed for home use come with Windows Home or Starter editions, which may require hours of expert assistance to link into a secure business network. Usage Requirements Work out how often you’ll be using the computer for business. If the computer is mostly for home use and only occasionally for work, then a consumer PC with the appropriate work software and settings will be fine. On the other hand, a computer that is mostly for business use should be a business-class computer, not just for security but also build quality reasons. Durability and Reliability It’s probably no surprise that consumer PCs don’t have the same build quality as business ones. In fact, consumer models only have an expected lifespan of around 2 years. They just aren’t built to last. Business-class computers are built to last several years, with higher quality components and rigorous testing at every level. Most parts (if not all) are name-brand with an emphasis on reliability and long term durability. Warranty and Service Unfortunately, when a consumer PC fails, the burden is on the owner to send it away for repairs. The terms of the warranty will usually state that any other attempt to repair it will void the warranty. Repairs can then take weeks and often involve a frustrating process of paperwork and following up. Contrast that with what happens when a business computer needs service – the technicians will come to you and fix it on the spot, often within hours. Business users enjoy a professional experience with priority status and a dedicated support line, all designed to reduce down-time and get you operational, faster. Talk to us today at 570.235.1946 or visit our Contact Page to learn more about choosing the right computer for your needs....
06 Feb 5 Ways to Love Your Laptop (and Make It Last Longer)
5 Ways to Love Your Laptop (and Make It Last Longer) Laptop computers are one of the most fragile pieces of tech you’ll ever buy. Here's how to love your laptop and make it last longer. Avoid Sharp Movements During Use While some newer laptops have an SSD drive with no moving parts, many laptops still have mechanical drives which work a bit like a record player. It has a head which is like a record player needle, and a data storage platter like a record. The head hovers just microns over the surface of the spinning disk and a knock can cause them to collide. Just like a deep scratch on a record, whatever data was on that section will be corrupted and lost. Make sure you always power down the laptop before moving it or packing it away. Keep It Cool Your laptop has 2 sure ways of telling you when it’s too hot - the fan and auto-shut off. Each component in your laptop is generating heat, and the harder it’s working, the more heat each creates. The fan runs to blow that heat out the vent and keep the components cool enough to continue operating. Because there’s no clear temperature indicator, your fan volume is the best guide to monitoring laptop heat. While the laptop is working hard (and getting hot), the fan will spin faster and louder. It’s not uncommon for it to sound like a hair dryer at times! Help it out by keeping your fan vent clear of books, blankets, and other blockages. Respect the Cords Inside those robust looking power cords are a bunch of delicate wires, begging you to be gentle. You’d think they should be able to take a beating, get bent, twisted and run over with chair wheels, but unfortunately not. Keep cords clear of sharp or flat-edged items, and when wrapping for transport try to mimic how it came out of the box. Wrap the cord gently around itself or the power adapter and secure with Velcro or similar. Carry It in Padded Style Look for a bag that not only fits your laptop but also provides padding. Your system will endure countless bumps and bangs as the bag is moved around, even with careful use. Ideally your bag has bottom, side AND top padding, as well as a waterproof outer. If backpacks aren’t your style, look for padded or hard-shelled sleeves. Back It Up Laptops give us fantastic mobility but as mentioned above they’re quite fragile. While a backup won’t make your laptop components last longer, it will make minor repairs that much easier. You’re more likely to take it in for a service if your data is accessible elsewhere, and of course, in the event of accident or theft, you’re fully prepared. Consider an off-site backup for additional protection, so no matter what happens with your laptop you still have your important files. Call us at 570.235.1946 or visit our Contact Page to give your laptop a life-extending service....
30 Jan Why Your Business Should Upgrade To A Managed Anti-Virus System
Why Your Business Should Upgrade To A Managed Anti-Virus System It is important to upgrade your business security with a managed anti-virus system, but why? Anti-virus programs don’t catch viruses when they’re not running. Yes, it’s blatantly obvious, but what’s not always clear is how often your staff are disabling your anti-virus programs so they can squeeze in a little playtime. Maybe download and install a game, free app or get through the block to a suspicious website. It happens in businesses across the country, and more often than you think. Unfortunately, the biggest threat to your data and network security is your staff. Fantastic, loyal, hardworking people, who make occasional silly decisions. Even the innocent ones, like ignoring the virus software update that keeps popping up, requesting to download the latest protections. Your staff aren’t intentionally putting your systems at risk, but they are creating a weak link that exposes your business to attacks that may cost you thousands. Free Vs. Managed Anti-Virus That’s the key difference between free anti-virus and managed anti-virus. The license on free solutions is usually only for home usage. This is because in a business setting, even the slightest gap in your digital walls can lead to lost revenue, delays and even lawsuits. With a managed anti-virus system, your staff can’t do those things. They literally can’t disable the protections or uninstall it, and updates happen automatically. With the benefit of human oversight, we’re able to see when machines aren’t fully protected or have already become infected. Managed anti-virus means just that – we manage it for you – so that we know when there’s an issue and can take the necessary actions. Often working invisibly to your employees, we can remotely fix small problems before they become big problems, which leaves your employees feeling trusted while your business remains secure. Managed anti-virus gives your business protection on a much higher level, because let’s face it, the stakes are much bigger. It takes software control out of the end users hands and puts your system security in the hands of an expert. The program can’t be disabled without a password, nor can it be uninstalled by anyone without the highest permissions. When updates are released they are downloaded and applied automatically. No delays, no putting it off until later, no gaps in your digital walls. When to Switch This is around the size where it becomes impossible to monitor each computer individually without a full-time IT technician on your team. Users spread out across the network and you’re way too busy to supervise. Need a managed anti-virus system? Call us today at 570-235-1946 or visit our Contact Page...
23 Jan Will That Click Cost You Thousands?
Will That Click Cost You Thousands? Just one click can cost thousands. Ransomware has undeniably been the biggest security threat of 2016. No-one was safe. Hackers targeted everyone and everything, including home PCs, earning themselves upwards of $846million from US reported incidents alone. Business is booming for hackers, with thousands of attacks each day bringing in an average of $640 per target. More alarmingly, the financial cost of each individual attack is on the rise. The more ransomware proves to be an easy earner for them, the more they demand each time. For a quick payday, some hackers offer to ‘rescue’ you from immediate danger – for a fee. One method is to trick you into thinking you have a virus that will spread if you don’t pay money to remove it immediately. Another much scarier method is to pretend to be the FBI and say your computer was involved in a crime (anything from money laundering to child pornography) and you can avoid going to prison by paying a few hundred dollars. Thousands of regular people are also waking up every day to discover they’ve been locked out of their own files. Entire music and video libraries, digital photos from the past 5 years, personal budget files and even their secret novel draft …all held hostage until the user pays a ransom. The encryption is so strong and unbreakable that paying the ransom often becomes the only solution. Ways Ransomware Gets Into PCs The way ransomware gets onto your computer is deviously simple. Generally, the hackers convince you to click an email attachment/link or pop-up. With both approaches, the hacker usually offers helpful information, for example: Tracking an unclaimed parcel Alerting that a virus was found and needs to be removed Advising details of a recent traffic fine It’s so tempting to click through for more details and that’s what the hackers count on. Their messages and pop-ups aren’t obvious threats and so slip easily under our radar. Unfortunately, they’re not the most trustworthy bunch so paying may not actually unlock your files, and one payment can quickly become several. To make matters worse, they can encrypt any backups connected to your computer too, like a USB drive. Having a backup is super important in any situation, but in cases like this, the right backup is needed. Not only one stored separate from your network, but one created recently with all the files you can’t bear to lose. Before restoring your backup, however, you’ll need to make sure the malware isn’t lurking in the background, ready to not just re-infect your restored files but also the backup drive itself. To avoid finding yourself up to the waist in ransom demands or sending hackers money each month, we recommend being wary of email attachments, even from friends and family. If you’re not sure what the file is, don’t click it. They may not have sent that email intentionally; their infected system may be auto-emailing everyone in the address book. You should also be careful with any popups that appear out of place, especially ones that try to make you panic. If it doesn’t sound right or look right, don’t click it. Ransomware is just too dangerous to risk. Call us at 570.235.1946 or visit our Contact Page...
16 Jan Why You Should Never Use A Free Email Address For Your Business
Why You Should Never Use A Free Email Address For Your Business Why you should never use a free email address for your business? There are many reasons. Many clients and customers choose to communicate primarily by email and as you know, it gives a fantastic ROI in your marketing strategy…unless you’re using a free email like Hotmail, Gmail, or even your internet provider. If that’s the case, you’re losing business each and every day. Here's why: It Looks Unprofessional First, imagine if banks used free email accounts – you’d never feel comfortable giving them your personal details let alone any money. How people perceive your business is what makes your business. Without that professional touch, you’ll appear temporary and fly-by-night. Consequently, it questions your credibility and sends the message that you're not serious about doing business - or worse - that you're prepared to cut corners. It Erases Your Experience Newer, fledgling businesses often start out with a free email address. The address clearly communicates that they are new and have little experience, and are perhaps testing the waters in a new direction. They’re not even remotely proven yet and are firmly within the hobby-zone. It’s Forgettable or Inappropriate Your business success hinges on being memorable enough to gain referral custom and results from your advertising. Unfortunately, free email addresses are by default filled with hard to remember clutter, for example – joesplumbing_1985@hotmail.com or milkshakes_mybabby@gmail.com. Both of these do not roll off the tongue, are not appropriate for business, and cannot be remembered without a high likelihood of typos and bounce back. Whereas using a branded email addresses such as joe@joesplumbing.com make running a profitable, scalable business much easier. It’s Not Permanent or Safe When you use a free email address you are at the mercy of the email provider. They may close down operations or cancel your account for any reason. Hackers often hack and leak free email addresses on a global scale.. Some will agree to keep the address open for a fee, but you’ll lose the control and flexibility you need to grow your business. With your own domain name, you own it and can move it to a new business-grade email service easily. In effect, you’ll also have complete master control over the addresses within your domain, resetting passwords and creating/closing accounts at will. Give us a call at 570.235.1946 or visit our Contact Page to set up your branded business email....
12 Jan Why Do Computers Slow Down Over Time?
Why Do Computers Slow Down Over Time? Computers slow down over time. Remember the awe you felt when you turned on your new computer and it loaded in a flash? Your computer was the envy of your friends and you weren’t afraid to bathe in that glory. Button on, ready to go, those were the days! What happened? After a year or two, it doesn’t seem to be quite as zippy…no, you’re not imagining it. It really has slowed down, not just in comparison to newer models and your expectations…There’s a measurable drop in speed and power that has nothing to do with worn out parts. The good news is a little maintenance can have that baby cruising at top speed again. Let’s take a leisurely walk through the system and spot the culprits: Start-up applications It’s super convenient to have Skype start automatically and your anti-virus too. In fact, many of the applications starting themselves with the computer are essential to your experience. But some of them are getting a little too ‘helpful’. For example, iTunes helper loads in the background to speed things up when you connect your device – but if you can’t even remember the last time you ran iTunes on your computer, then it can go. Programs like that are holding onto a portion of your processing power and adding to your speed issues. The average home computer automatically loads around 75 programs at start-up! Click to read more about configuring start-up applications. Temporary junk Computers are kind of messy. They leave temporary files and snippets of information all over your hard drive, each action leaving a trail rather like a roaming toddler with a sticky sandwich. Every webpage, every image on that webpage, every program you run and every game you play leaves something behind. It may be the tidbits of information called “cookies”, saved game files, auto-restore files or even a log so that you can hit the undo button 100 times while it remembers your actions for you. The more junk your computer builds up, the slower it gets. Viruses and malware These infections sit in the background consuming resources while doing various nightmarish things. They may be spying on your actions, stealing your information or reaching out through your network to infect others. Occasionally, the impact is limited to seeing your computer slow to a crawl, however the flow-on financial costs of an infection can easily reach into the thousands. Bloating With every new version of software comes a new set of features, introductory sequences and design improvements. The problem with this is the application becomes larger and larger with each new version, requiring more system resources to install and run – and slowing your computer down. Just like a car, computers need regular maintenance - we offer a Tune-Up service to bring your computer back to its original speed and extend its life. Give us a call at 570.235.1946 or schedule an appointment to book in a Tune Up....
26 Dec Office 365: 11 Reasons To Upgrade Today
[caption id="attachment_2712" align="alignright" width="300"] 11 Reasons To Upgrade to Office 365[/caption] With Office 365, it seems common sense has finally prevailed, giving business the changes they actually want. It’s still Office, and your staff will still know exactly how to work it, but they’ll get so much more done. 1. The whole Mac/Windows drama is over Office 365 brings with it a stack of benefits, but perhaps the most relieving is the built-in file compatibility across all platforms. No more converting (or corrupting) files back and forth, productivity black holes have essentially been eliminated. 2. It’s always ready to go Microsoft are so confident in their cloud-based software and data storage; they’re giving a 99.9% uptime guarantee. You can even call a real life human for support. Work online, offline or mobile – the choice is yours. 3. Security is built in A large part of Microsoft’s uptime certainty comes from their extremely robust security protocols. Office 365 offers enterprise-grade admin controls at your end, as well as government-grade security at their end. 4. Generous data allowances Each user gets 1TB of cloud space for file storage, which can be shared at folder or file level. 5. Work anywhere, anytime Previously, staff needed to establish a VPN or manage security concerns which made working off-site difficult and cumbersome. Office 365 has solved that problem and working from anywhere is now easy. 6. Integrated across devices Calendar, email and contacts are all synced and updated across multiple devices: Laptop, desktop & mobile. 7. Yours for no upfront costs Once upon a time, updating your Office version meant paying a small fortune and half a day downtime. However, Office 365 comes with no upfront cost or installation delay. 8. Mailbox storage through the roof Forget the days of ‘user mailbox is full’ – each user is given a whopping 50GB in a gorgeous, easy-to-use mailbox. 9. Built in malware and spam protection Data security doesn’t stop at file storage: email is scanned for malware and spam, protecting your business from all manner of attacks before they happen. 10. Collaboration tools and virtual meeting Cancel your 3rd party services and bring all your collaborations into the one platform. 11. Integrated Team planning Schedule tasks, meetings and track allocations from a top-down level to know exactly how projects are progressing. We can help with your Office 365 migration and setup – give us a call at 570-235-1946 or visit our Contact Page...
19 Dec How To Protect Your Children While They’re Online
How To Protect Your Children Online Waking early to sneak in a couple hours of Minecraft, Roblox, YouTube or Xbox…grabbing their ‘educational’ iPad and Facetiming a friend…sending emails and texts…it’s open season during school holidays! Not just the younger children, but teenagers too. Adults have no idea what’s cool or what children have been introduced to at school. They’re digital natives and use it in ways we would never dream of. Children are going to using their devices and we won’t be able to watch them every second of the day. No matter how many Cyber-Safety talks they’ve had, how many times they can parrot the rules back, they are still children and they don’t always stop to think. They don’t realize certain search terms might not be such a great idea They trust they are messaging other children And they would rather not limit themselves to 2 hours per day Protect your Children with Parental Control Software A Parental Control Software (PCS) package is essentially an internet filter for children. It takes all the icky, inappropriate things online and blocks your child from accessing them, seeing them or even knowing they exist. Learn more about PCS packages. Adults can override and disable the software easily, so their own experience is unchanged and unmonitored. Parental Control Software can be used to put time limits on internet usage, or even log all online activity. While you may not feel the need to review the logs on a daily basis, they can be vital in identifying cyber bullying, sexting, or inappropriate relationships. Parents around the world credit these logs with saving their child’s mental health, and occasionally, their life. The best time to install Parental Control Software is now, before your children become comfortable with unrestricted access, and before they see things they shouldn’t. Contact us to set your computer up with Parental Control Software today....
12 Dec Should You REALLY Click That Upgrade?
[caption id="attachment_2714" align="alignright" width="300"] Should you really click that upgrade?[/caption] Should you click that upgrade? The pop ups won't leave. It’s been hounding you to upgrade your software and clearly, it has zero intention of giving you a moment's rest. That software wants to be upgraded and it wants it now. With a grudging sigh, you click and let it upgrade in the background. Maybe now it will let you get some work done. Except instead of grabbing a competitive advantage by having the latest and greatest edition, you quickly discover it's given you the exact opposite. Your essential hardware no longer works, you've got errors all over the place, and that application no longer runs at all. Your urgent upgrade was more of an instant downgrade. Before You Click that Upgrade Button Is the upgrade going to work with your current systems? If your project management software no longer talks to your scheduling software, you've got a problem. It's reasonable to expect the upgrade to have gone through robust testing and bug fixes, but even the mega corporations are caught out in an instant. Is your current solution still an option? Developers cease support of older software versions after a certain date. In these cases, continuing to use an outdated version leaves your system vulnerable, without patches and security updates. If your software is at the end of its cycle, you'll need to upgrade regardless. This, however, gives you the perfect opportunity to revise your selection and make some experienced decisions - upgrade or replace. Will this upgrade benefit your business? Some upgrades are purely cosmetic. They look great and the developers pitch them as the latest and greatest, but without additional innovation on offer, you're better to wait. On the other hand, if the upgrade is going to have a positive effect on productivity, efficiency or customer satisfaction, definitely put it on your to-do list. Hold off for just a few moments though, while your IT technicians research any conflicts that might arise. Being an early adopter isn't always the best idea. Sometimes you need to let your other software packages catch up, and compatibility issues will always be relevant. It's more important than ever before to take your time and research the upgrade to see how others have fared - before things come crashing down. If you have updating problems click here to read about Windows Update Troubleshooter Call us at 570-235-1946 or visit our Contact Page for a quick compatibility check before you click ...
05 Dec Staying Safe while using Social Media
[caption id="attachment_2713" align="alignright" width="300"] Staying Safe using Social Media[/caption] So how do you balance being social with staying safe? People happily share their private information online, building robust libraries that can easily become a one-stop goldmine for fraudsters. It’s not exactly the intention everyone has when they sign up, as the whole point of Facebook is to share your life with your friends. It hooks us into a global community and the experience does depend on us making certain privacy sacrifices. So how do you balance being social with staying safe? On Facebook alone, the average person shares 13 pieces of personal information ranging from a fairly innocent name/email combo, all the way to mothers maiden name and home address. It doesn’t sound like a lot, but those 13 pieces have the power to unravel your life within minutes. Even checking in at home has become the norm, helping to create a multi-dimensional online identity. The details are available to anyone who cares to look, whether they’re a friend keeping in the loop, or someone with a much darker agenda. The problem is, you just don’t know who’s looking at your profile or why. For example, someone could try accessing your email account by clicking the ‘Forgot password’ link. The email service follows its security rules and asks identifying questions like ‘which high school did you go to? What is your pet’s name?’ Unfortunately, the most common identifying checks and answers are probably available on Facebook. Once your email address is compromised, hackers can use that to break into other services and go through, clicking ‘Reset Password’ on site after site, account after account – they have full access to your email, so there’s nothing stopping them from emptying your bank accounts – or worse. 7 Ways To Secure Your Facebook Without Missing Out on the Fun Begin by previewing your profile as others see it Review what should and should not be visible to strangers Consider only sharing partial details, like birth day and month, but not the year Only ever ‘Friend’ people you know and trust Be wary of duplicate or ‘odd’ friend activity – hackers will often clone or hack a friend’s profile and initiate an urgent and uncharacteristic request for money Update your past privacy settings too Set default future sharing to ‘friends only’ Are your privacy policies up-to-date on Facebook? Click here to learn more about updating privacy and security settings on FaceBook. Make sure your computer is safe while using social media by giving us a call at 570-235-1946 or by visiting our Contact Page...
14 Nov Why Managed Services Will Save You More Than Money
Why Managed Services Will Save You More Than Money “Downtime costs money.” That’s no secret, but it doesn’t quite capture the whole experience…you arrive to work in the morning, grab your coffee knowing you’ve got a hectic day ahead, and are ready to dive in. For some reason the computer can’t access the database and neither can anyone else’s. You restart the server while fielding calls left, right and center, but are unable to answer any client queries. Your hands are completely tied…and now the server is beeping furiously…what’s going on??! You’re not just in crisis mode, you’re on damage control as you call every tech you can think of, trying to find one who can come NOW. Not exactly the day you had planned. The Break/Fix Days Are Gone Previously, businesses only addressed their IT needs when something broke. A few hours down meant little in the scope of things. In today’s fast world, businesses rely heavily on IT and downtime just isn’t an option. Even the legalities of simply restoring financial, legal or medical files after a breach raises issues. How Can Managed Services Help? The cost of break/fix is now too high, both financially and emotionally. Simply put, your IT services are remotely monitored and proactively managed by a professional, external business. Your Managed Service Provider (MSP) runs regular diagnostics on equipment to identify impending failure and resolves problems before they happen. Benefits of Managed services Small to medium businesses in particular benefit from managed services, because they don’t usually have an on-site technician to oversee the multiple systems in use. By subscribing to a managed service provider, businesses can have reduced labor costs, access to a knowledge base, future-pacing, better data security and reduced downtime. Businesses can also know exactly what their upcoming costs are and plan accordingly. Read more about managed services Some of the managed services we can provide are: Remote support – This allows us to help you quickly without needing to be on-site Hardware monitoring – We monitor your servers and workstations to catch hardware failures before they happen. Managed anti-virus – We make sure your anti-virus is up to date and take immediate action if an infection occurs Patch management – We make sure your computer’s operating system is up to date, closing access to known vulnerabilities as soon as possible How much down time can your business afford? Call us at 570-235-1946 or visit our Contact Page...
07 Nov 6 Quick Security Tips To Keep Your Business Safe
Every employee shares one inescapable flaw that is putting your business at risk. They’re human. 59% of data breaches can be traced back to something an employee did (or didn’t do), which invited a cyber-attack. The Scam Goes Like This To lock hackers out, build security awareness and respect into your company culture, so that maintaining digital security becomes as routine as making coffee. Use Complex Passwords Every employee, including management, needs to use an alphanumeric password that they haven’t used before. Password managers can assist with making sure they’re never forgotten. Verify Unknown Identities Not familiar with ‘Jenny from Accounting’ who has called to ask for sensitive information? Double check caller identity and access permissions before releasing any information. Hackers love to play on our desire to be helpful. Encrypt by Default People regularly transfer data to a laptop or smartphone so they can work more efficiently. Unfortunately, this equipment can be easily stolen. Set operating systems to encrypt data by default, so that it becomes useless in the wrong hands. Protect Portable Devices Laptops and mobile phones should always require a password and be set to auto-lock after a short period of time. Never leave them unattended in cars, buses, restrooms etc, and take them as carry-on luggage. Set Personal Usage Rules While you may have blocked productivity-vacuums such as Facebook, what are the rules regarding games, video streaming or shopping? Can they install their own software? When business computers are used for personal usage, security vigilance tends to slide, resulting in unintentional malware installation. Educate Often Digital security threats change regularly, and people become comfortable with a certain level of danger, thinking ‘it will never happen to me’. A 5-minute discussion once a month may be the barrier that keeps hackers out. Starter Topics Links in emails – Hackers often send emails that look like they are from your bank or similar. Be sure to check the link by hovering over it with your mouse. This is known as ‘phishing’. Tech scam popups – Be on the lookout for popups advising that your computer is infected and you need to call a phone number or download software. Email attachments – Never open an unknown attachment, and even from people you know and trust, always scan for malware before opening. If you need help implementing better security practices in your business, give us a call at 570-235-1946 or visit our Contact Page...
31 Oct Quickly Become A Google Fu Master… Here’s How
Quickly Become A Google Fu Master Kids are quickly becoming Google fu masters. They’ve become experts at quickly locating information online using search engines. That’s Google Fu, the ability to use search engines to whip up answers and research faster than a contestant on a radio quiz. No matter what age, you too can become a Google Fu Master. Level 1 Mastery: Tell It What You Need Google is smart and can understand “conversational searches”. Let’s say you came across a great recipe online, but the measurements were imperial. Google has you covered. Simply tell it what you want to convert, and what into. [number] [unit] into [unit] Enter “6 ounces into cups”…and hit enter. Google presents the answer, already calculated – AND it includes a handy drop down to change those measurements for your next ingredient. Release dates: [movie/game] release date Fast facts: [name of person] deathDurable – No moving parts to wear out Stats: [city] population Level 2 Mastery: Limiting Result Type With one additional click, you can tell Google that you only want images. Or videos. Or News, maps, shopping, books or apps. Your initial results are presented as a combination of all types – you can see the ALL tab highlighted up the top. Just click the tab to indicate which result type you’re looking for. Level 3 Mastery: Using Drop Downs. One of the most popular Google Fu moves is to limit results to sites from a particular country. This is great for locating bargains or local businesses. Click SEARCH TOOLS to drop down a second menu. You’ll see the option to limit Country and even Time. 2 extra clicks and my search is now limited to my home country and items from the past 7 days only. Level 3 Mastery: Using Operators. Your final level of mastery, often used as a last resort when you’re just beginning to doubt whether the internet has the answer you’re seeking. Finally, enclosing your search terms in “quotation marks” binds the term together so Google can’t break it up. E.G. “Project Management” Your Google Fu will soon be very strong. More Google search tips and tricks Want more business advice? Call us at 570-235-1946 or check out our Consulting page to fill out a form for a free consultation!...
25 Oct How To Spot A Tech Scam Before You Get Stung
If Your Computer Had A Virus, You’d Want to Know About It ASAP, Right? Tech scammers know we’d be lost without our computers, and that we don’t always know what’s going on behind the screen. In effect, they’ve been able to swindle millions from people across the world every day. Tech Scams Go Like This You receive a random phone call from someone with a heavy accent (usually Indian) saying they’re from Microsoft. Pop-ups appear on the screen indicating system is infected with a virus. Then, to fix the problem, they instruct you to download support software. From here, the technician gives you a special link to use. Thereafter, a technician uses that software to gain access to your system, and makes it appear as if your system is riddled with viruses. For example, flashing screens, mysterious diagnostics whizzing by, fabricated errors…they’ll do or say anything to invoke panic. Scammers go as far as claiming your system has been infected with illegal content, and can lead to criminal charges. Finally, scammers will make demands for credit card information. Once paid, scammers stop fiddling with your system to create the illusion that the problem is fixed. To continue the scam, they’ll soon access your system to recreate the problem, this time offering a subscription for ongoing protection. What To Do If Targeted By Tech Scams? 1. Don’t taunt them. Just hang up. Right now you’re only a phone number in their system and they’ll move onto the next. However, if you give them cause to target you personally, you may find yourself in a dangerous situation. The real Microsoft will never randomly call people like this. Ever. 2. If a pop-up appears, immediately run an anti-virus scan. Don’t click the pop-up or call the number. Already A Victim of Scams? Call your financial institution and have the charges reversed and your card reissued. It’s easier than you might think and helps the authorities locate the scammers. Give us a call at 570-235-1946 or visit our Contact Page and we’ll make sure scammers no longer have access to your computer...
24 Oct Could Your Backups Survive A Ransomware Attack?
More and more businesses and organizations are getting stung by ransomware attacks. Hospitals, schools, social networks…some days it seems like an epidemic that leaps around arbitrarily, and hackers are raking in millions. Losses in the Billions Ransomware attacks are devious in their simplicity. A user in the target business is tricked into opening a file, usually through a phishing email or download. The file contains malware which instantly encrypts your data and demands money in exchange for the password. Cost of Not Backing Up All of the target businesses should have backups, which they could simply revert to without paying any money. However, the FBI reports more than $209 million was sent to hackers in the first quarter of this year alone. Keep in mind, this was just payments within the US, and only counts those who came forward. Last year it was only $25million. Do Backups Help? Sometimes the backup solution fails and the data can’t be retrieved. This is particularly true in cases where the solution has been in use for years and something failed along the way. In other instances, the target business has a backup that can be restored, but it doesn’t include everything they need for full recovery. Finally, and the most common reason so many businesses are forced to pay the ransom: the ransomware attack affects the entire system. If the backup is also caught in the ransomware encryption, it becomes useless as a recovery method and the only options are to pay or lose the data forever. Each day spent trying to recover the data drains valuable business resources and in many cases, results in massive revenue loss. The only defense is to block the malware before it can infect the first workstation. Then, continue the protection with a comprehensive backup strategy for all workstations and servers. Want protection from ransomware attacks? Call us at 570-235-1946 or visit our Contact Page...
20 Sep On-Site Computer Repair Appointments Available Now. Book online!
Schedule Your On-Site Computer Repair Appointments Today! Remember the days when doctors made house calls and milk was delivered to your doorstep? (Actually, I don't...
18 Sep Winner, winner! We won the NEPA BlogCon Tech Blog of the Year!
Blog of the Year Awards 2015 NEPA BlogCon Tech Blog of the Year It's been several weeks since we closed up our computer repair shop in Mountain Top, making the Dolphin Plaza on Route 315 our permanent home. (Now located on 237 Old River Road Wilkes-Barre, PA 18702, in the rear of the Dolphin Plaza. Come on down and see our new place!) We're moved-in and the dust is still settling, but we are open for business. Fixing iPhones and iPads, desktop and laptop computers, etc. Don't forget, if you're having trouble upgrading to Windows 10, we are here to help. The bugs are still being ironed out, but quite a few people reported liking it much more than Windows 8. Yep...
11 Jun Windows 10 is Coming, and NEPA Geeks are Here to Help You Upgrade
Windows 10 is coming, and as the latest edition of the powerful operating system, it promises to be better than ever. Microsoft has set the release for Windows 10 to be July 29, 2015 -- only a few weeks away. But the really big news is that this version of Windows will be free to current users of Windows 7 and Windows 8. In fact, you may have noticed the new icon sitting in your task bar, asing if you want to upgrade. All you have to do is claim your copy, and it will waiting for you. But what then? That's when you call us -- NEPA Geeks. We'll ensure that the upgrade process is smooth and trouble-free. For a low price of only $99.99, NEPA Geeks will backup your existing data and upgrade your operating system to Windows 10. Your data will then be put on a DVD and returned to you with the computer. (Only applies to current Windows 7 and 8 users who have registered for their free copy of Windows 10) Curious about upgrading, but not really sure if it's for you? You will be able to find a TON of information on the new operating system over at Microsoft's blog, detailing almost anything you could want to know about it. Still unsure? Feel free to give us a call at 570-235-1946 or visit our Contact Page. We'll be more than happy to answer any questions you might have. And don't forget, the price of $99.99 comes with a free backup, ensuring that your data will be safe and secure in the event that you find incompatibilities with your software or hardware, or simply don't like Windows 10 and wish to revert back to your original operating system. Just let us know, and we'll discuss details about downgrading. So, are you ready for Windows 10? July 29 is just around the corner...
23 Apr It’s Spring Cleaning Time for Your PC!
It's Spring Cleaning Time for Your PC! Do you have a “dirty” computer? Chances are, you do. Dust, dirt, hair and other things can get inside your computer, causing anything from minor nuisances to reducing the lifespan of the components inside. But how do you know your computer is dirty if you’ve never looked inside? Here are some symptoms to look out for: Computer Slow Downs Slow downs are usually a dead giveaway that not everything is running smoothly on your hard drive. Over time, the constant adding and removal of files leaves gaps on the disc, where data is overwritten to make room for new applications and files. This is called fragmentation. As part of a tune-up, NEPA Geeks will make sure the hard drive is “de-fragged,” allowing it to work quicker without putting more wear and tear on its sensitive components. Excessive Heat Heat is extremely bad for your computer, and the inside of your computer can be like an oven if vents are blocked and fans aren’t working properly. Irreparable damage to the video card, CPU and memory chips can occur within minutes, leading to costly service and repairs. If your computer gives you odd errors, doesn't boot properly, or sounds like a jet engine taking off, there might too much heat inside. At NEPA Geeks, we will clean out the dust, hair and whatever else might have managed its way into your computer before it’s too late. We’ll make sure the heatsinks are free of dust and that vents are wide open for good airflow. Weird Noises You might not realize it, but there are a lot of moving parts inside your computer. Spinning fans can buzz if dust and other debris touch the fins. Additionally, they buzz when the ball-bearings begin to wear down. NEPA Geeks can replace fans before they fail altogether, allowing your computer to overheat. Hard drives might not look like it, but they have moving parts, as well. Inside is a spinning disc and a “read/write” head that scans the disc and writes or reads data. It looks like a needle on a record! Over time, these parts wear out, leading to buzzing and other noises. Other sounds, such as beeps and clicks, might indicate problems that aren’t immediately obvious or noticeable, but can lead to data loss or permanent damage to the computer’s components. Give NEPA Geeks a Call And there you have it! If your computer is running slower, hotter and making weird noises, it’s definitely time for a spring cleaning! Call us at 570-235-1946 or visit our Contact Page...
27 Jan Protect the Data on Your Home or Business Computer with Our Carbonite Online Backup Setup
NEPA Geeks Carbonite Online Backup NEPA Geeks is now a Carbonite authorized reseller. Now you can purchase Carbonite’s automatic online backup service for your home or work computer through us. We can even bundle it with our Geek Care Managed Services Plan! Subscribers in more than 100 countries rely on Carbonite to provide easy-to-use, affordable and secure cloud backup solutions. Carbonite has backed up more than 300 billion files, restored nearly 20 billion files, and currently backs up more than 350 files each day automatically. You’ll never have to remember to back up again! Carbonite offers automatic, continual and secure online backup for your home or business computers so you can rest easy knowing your irreplaceable files are protected. Once installed, your files will be backed up automatically to the cloud – no hardware required. File Access Anytime, Anywhere Not at your computer? No problem! You can get to your backed up files from any computer connected to the Internet or even from your smartphone or iPad® with Carbonite’s free app. And, with Carbonite’s Anytime, Anywhere Access, you can view your files anytime – whether you’re at home, or on the go! Protect your files with Carbonite today! Visit this link or more information on how you can start backing up the files on your home or work computers, contact us today by calling 570-235-1946 or visit our Contact Page...
28 May New Ransomware Scam Targetting iOS Devices Through Find My iPhone Exploit
Apple Users Beware of Find My iPhone Exploit We are warning all customers with iPhones and iPads to immediately back up their devices either to their iCloud account or personal computers. Several news outlets have reported that hackers are using a Find My iPhone exploit to remotely lock-up iPhones and iPads. The "Find My iPhone" feature is a safety mechanism that allows a user to lock-down and erase sensitive data if their device is lost or stolen. However, in the wrong hands, this feature can be used to disable devices and, in the case of this attack, demand a ransom to reactivate it. The hackers are using a classic attack known as "phishing" to set up sites that look like legitimate Apple websites. Users enter their email and password into sites, not knowing it is a fake. Then, hackers use this information to access and lock the devices using the "Find My iPhone" feature to demand a ransom in exchange for unlocking the device. Back Up Before Its Too Late Again, if you haven't done so already, backup your data to iCloud or your computer. Users should bring their devices to the nearest Apple store if they've been compromised. It is important to set up your iCloud account and backup your data immediately. Doing so is the only way to get your photos, pictures and music back after a hardware reset. For more information on this attack, visit BGR.com or ArsTechnica.com. Stay protected from exploits like this. Call now at 570-235-1946 or visit our Contact Page...
11 Mar Windows XP End of Life
Attention Windows XP Users On April 8, 2014, Microsoft will be ending its support for Windows XP. This means that Windows XP will be left open and vulnerable to any future attacks. In the past, hackers found security holes and exploits that would allow them to stealing your valuable information. In the past, Microsoft protected you with security patches. From April 8 on, however, these patch updates will no longer be released. That means any new holes or exploits will remain forever. If you are a home user, your personal information -- along with anything else stored on your computer -- could become accessible to anyone knowing how to exploit these security holes. As such, it's very important that you upgrade to any operating system later than XP. This includes Windows Vista, Windows 7 or Windows 8. If you run a business that has computers running Windows XP, it could mean the end of certain security certifications. Running a computer with XP will soon become a liability. If your business relies on storing the information of customers and clients, this data could be easily available to hackers capable of exploiting new found security holes in your systems! A quick call is all it takes to make sure you have everything you need to keep your computers running safe and secured. Call us at 570-235-1946 or visit our Contact Page...
09 Dec Bitcoin for Computer Repair Now Accepted at NEPA Geeks. You can even pay with Litecoin.
According to CoinMap.org, NEPA Geeks is the one of the only computer repair shops (if not the ONLY computer repair shop) in North-East Pennsylvania that accepts Bitcoin for computer repair. Well, as far as we can tell, based on the screenshot below: [caption id="attachment_2018" align="aligncenter" width="300"] This map shows businesses in NEPA that accept Bitcoin, including Centerline Guitar Repair Shop in Hazleton.[/caption] If you've never heard of Bitcoin, it's an open source peer-to-peer payment network and digital currency that was introduced in 2009 and has been steadily increasing in popularity and worldwide acceptance as a legitimate currency. One of the facets of Bitcoin that make it so attractive to businesses and merchants such as ours is the low transaction fee associated with transferring funds. Typically, the transaction fee is lower than the 2 to 3% charged by most credit card companies. This reduced fee helps us keep costs low, which we then pass on to customers and clients by keeping our rates for repairs low. All in all, if we can keep the regular cost of doing business down, it's better for everyone, and that's why we've decided to incorporate Bitcoin as a method of payment. We accept Bitcoin for computer repair, web hosting, iPhone and Android repair, and even game console repairs. The cost of parts and all of these services, and many not even listed here, are easily paid for using Bitcoin. So, if you're one of the many early adopters of this brave, new, digital frontier, we'd be more than happy to assist you by allowing you to pay in the currency of your choice! (Litecoin also accepted!) For more information, stop in or give us a call. We're always here to help....
03 Dec New malware, CryptoLocker, locks your files and holds them for ransom
Because we care about our customers, we want you all to be on alert for a new strain of malware going around. It's called CryptoLocker, and it extorts money from victims by encrypting their files and holding them for ransom. [caption id="attachment_2006" align="alignright" width="300"] Image source: GrahamCluely.com[/caption] What is CryptoLocker? It's a nasty piece of malware (or ransomware) that encrypts the files on a victim's hard drive, rendering them unreadable. Photos, documents, PowerPoint Slides, etc...
15 Nov Shop Small and Save Big on Small Business Saturday, November 30
Shop small and save big on repairs this Small Business Saturday As part of Small Business Saturday, NEPA Geeks are extending an offer to save 20% on all repair services. To redeem the offer, just bring your broken computer, phone or video game console into the shop on Saturday, November 30 to receive a 20% discount on the service charge to repair it. That's all there is to it. Cracked screen? Overheating XBox? Viruses and spyware plaguing your laptop? We'll take care of it, and you'll reap the savings. Small Business Saturday is an effort that is sponsored by American Express and began as a way to show support to all small and local businesses in cities and towns across America. We're just one of the many shops that are taking place in this great cause that helps stimulate the economy, create new jobs and improve the community. Over 100 million people shop at independently-owned and operated businesses each Small Business Saturday, and we'd be very honored if you chose to shop small by bringing your computer or cell phone to us for repair. As always, computer diagnostics are free, and our technicians are always willing to make house calls if you can't bring your equipment to the office. For any questions or problems you might be having, just give us a call at 570.474.5100 and our address is 108 N. Mountain Blvd. Suite B, Mountain Top, PA 18707. We can also be reached at staff@nepageeks.com For more information on Small Business Saturday, visit ShopSmall.com....
01 Oct NEPA BlogCon is this Saturday! See you there!
This Saturday is the 2nd annual NEPA BlogCon, and the NEPA Geeks are very proud to be a part of it! If you haven't heard of NEPA BlogCon, it's an annual, day-long conference set to take place at the Luzerne County Community College in Nanticoke, PA on October 5, 2013. Along with discussion of how to become a blogger (or a better blogger) there will be plenty of chances to meet and mingle with many of the other notable bloggers and blogging personalities that live and work throughout North-East Pennsylvania. Not only will we be attending the conference, one of our technicians, Dale Culp, will be giving a presentation on the importance of setting up a domain name for marketing and branding purposes. So, if you happen to be there, be sure to sit in on his presentation. And, afterwards, meet up with the Geeks to talk more about how our hosting services can help take your blog to the next level! In the meantime, the NEPA Geeks "geek blog" has been nominated for a NEPA BlogCon Blog of the Year award! However, we can't win the award without your help...
24 Jun NEPA Geeks is now fully accredited by the BBB!
[caption id="attachment_1855" align="alignright" width="226"] The BBB plaque on our wall.[/caption] One of the backbones of a good business partner is trust, and we work extremely hard to be worthy of that trust. From ensuring that we use only quality parts when replacing and repairing your electronic equipment to making sure our customers are satisfied with the work that we do at a fair price, trust goes into every step of the process. Recently, we've taken a much larger step towards building trust with our customers by becoming accredited with the Better Business Bureau. As of June 17, 2013, NEPA Geeks is a fully accredited business with the BBB. What this means is that we are being held to a whole new level of accountability. By becoming accredited, we've put ourselves out there as a name that can be trusted and a business that works hard to keep that trust. The standards for becoming a BBB accredited business include honest advertising, transparency, a vow to honor all promises, responsive service, integrity and the utmost of security when it comes to safeguarding your private information. Of course, these are standards we've held ourselves to long before becoming accredited, but now you know that we take these issues very seriously. When it comes to computer repair, web hosting, cellphone repair, or any of the many services that we offer, wouldn't you rather work with a business that pledges to keep and honor the practices and standards set forth by the BBB? We think so. And that's our promise to you....
07 May We are proud to be the NEPA Blogs and PA Live! blog of the week!
This week, we are extremely honored to be the NEPA Blogs "Blog of the Week" and featured on WBRE's "PA Live!" Each Tuesday, NEPA Blogs features a different blog that either caters to news and information about North-East PA or is maintained by a blogger located in North-East PA and presents them on WBRE's "PA Live!." Both Jason and I are proud to share this distinction as we each strive to provide a useful service to the community as well as building a successful business. Be sure to watch "PA Live!" at 4 pm on WBRE to see our blog! Update: Just in case you missed it when the segment aired on TV, the video is now available on the PA Live! site....
25 Mar Time for a PC spring cleaning? Dust can lead to a dead power supply, or worse!
[caption id="attachment_1798" align="alignright" width="300"] We've seen worse, but don't let your computer get this dusty before you come see us![/caption] Time for a PC Spring Cleaning It seems like the last few weeks, our number one service request has been to replace bad power supplies. The power supply is a metal box inside your computer (usually with a fan inside) and distributes power to the mother board, disc drives and various other components. It's the part with the black cable that plugs into your wall. You can see what one looks like in the upper right-hand corner of the picture to the right. So, why are we seeing so many dead power supplies? Well, between Jason and I, we came up with a couple of theories. DUST For one, despite Punxsutawney Phil's prediction that spring would come early this year, we just haven't seen it, yet. As a result, people are keeping their doors and windows closed -- many with weather stripping to seal up drafts. If you aren't dusting and vacuuming regularly, dust gets trapped and builds up inside your house, especially for households that smoke, run their fireplace or use coal for heat. Dust gets pulled into your computer and sticks to the fans, grates and other components, clogging up airways and acting like insulation, keeping the heat from dissipating when components begin to warmup. Dust that clings to fans can cause them to fail sooner as they struggle to keep the air flowing through your PC. A bad fan isn't just a noisy nuisance, though, it can allow a PC to overheat, which can lead to a cooked CPU and video card, burned out motherboard or power supply. Once a PC begins to overheat, if not immediately shut down, the various parts inside can be ruined in just a matter of seconds. It doesn't take long! DRY AIR Dry air isn't just bad for your skin, it's bad for your computer, too. Ever get a shock when touching a door knob or another person after rubbing your feet across a carpet? That tiny jolt might sting for a fraction of a second, but it can utterly destroy the vital electronics inside your computer. Dry skin rapidly sheds dead cells which become dust and mix with other particles in the air, each becoming charged and building up static electricity. Those charged particles build up inside your computers and can allow the components to short or discharge, frying them in the blink of an eye. This is also why it's important to be properly grounded if you ever venture to open your computer's case and poke around inside. If your body has built up a static charge, you could easily zap any of the chips inside and permanently damage them. It's best to keep your computer cleaned out, free of dust, and to never touch anything inside the computer if you're not grounded and have allowed the static electricity to safely discharge. WORKING OVERTIME Another drawback of the overdue spring is that people are staying inside, using their computers more instead of going outside to enjoy the nice weather. Our modern PCs are an endless source of entertainment and diversion, from playing video games to watching movies and TV shows, chatting online or catching up with friends over social media. Those long hours add up, and as the computer constantly works to stay cool, eventually it will wear out. Power supplies generally last well beyond the useful years of the average PC, meaning that you'll probably be ready to upgrade to a whole new system before you have to worry about one burning out. However, for the reasons I've stated here, some power supplies might burn out much sooner than others. In conclusion, whether due to wear and tear over the years from working under normal conditions, a build-up of dust that leads to overheating, or electrical shock damage from static or other sources (lightning strikes, power surges, brown outs) power supplies can go bad for a variety reasons. Why does it seem to be happening so often these last few weeks? That's anyone's guess. But with spring just around the corner, it's definitely time to look into getting your computer cleaned out. Give us a call if your computer isn't booting properly or is overheating, randomly shutting down, making a lot of noise or just needs a good cleaning out. We're more than happy to help! As a note of caution, if you decide to clean your PC out yourself, be extra careful around the power supply, and NEVER open it unless you are specifically qualified to do so! There are components inside your power supply that can build up a dangerously high level of voltage that can kill you if discharged. Play it safe! Contact an expert, like us, if unsure. ...
08 Mar Cracked Laptop Screen Repair
Cracked laptop screen? We can fix that. Earlier this week, we finished replacing the broken screen on a laptop that had been dropped. As you can see from the picture below, it was in pretty sorry shape. [caption id="attachment_1780" align="aligncenter" width="300"] Before and after shot of a cracked laptop screen.[/caption] Although it might seem like a catastrophe, this sort of damage doesn't mean the laptop has been totaled. As we often do with a job like this, we ask clients deposit the amount necessary to cover the price of a new part before we do any work. From there, we simply wait for the part to arrive (which, unfortunately, can sometimes take as long as a week) and then get the laptop back up and running in a matter of hours. And all this for much less than it would cost to buy a new laptop! Most of the time, replacing a cracked laptop screen or defective part costs so little compared to the price of a new laptop that getting the old one repaired is very cost effective. Sometimes, however, it isn't. In those cases, either when a part is soldered directly to the board, or when the laptop is so old that parts for it are no longer available, you don't get much of a choice. We'll make sure you understand your options and tell you when buying a new laptop is the way to go. If you're ever unsure whether a laptop can be fixed or not, it's always best to give us a call and let us take a look at it. You might even be surprised to learn that the laptop wasn't broken at all, it just needed some TLC to get up and running again. Another thing to consider when thinking about buying a new laptop is that, while it might be cheaper, it's not always more convenient. Your laptop is probably stuffed with old memories, projects and other things you don't want to lose. You probably have photos from vacations on there, movies and music, homework and gigabytes worth of other important data you can't replace. If the laptop is so broken that it can't even turn on -- assuming the hard drive isn't dead -- how will you get that data off? Fortunately, we have tools that can help. Whether you want the data backed-up to an external drive or transferred to the new computer, we're more than happy to assist you. Each of these laptops were repaired, cleaned and returned to their owners in perfect working order. Dell, Asus, Sony, HP...
14 Feb The Daring Librarian >> 4 Password Security Tips You Should Be Using
4 Password Security Tips You Should Be Using How secure is your password? Is it "password?" Come on...
08 Feb Ars Technica Article Covers the Basics on Malware
Protect yourself! Learn about malware. Viruses, worms, trojans, spyware and malware -- what does it all mean? If you're at all familiar with technology, you've probably heard a few of these words dozens of times. But what are they? What's the difference between them? This lengthy, in depth Ars Technica article covers the basics. We all try our best to keep our antivirus software up to date while practicing the "tried and true" methods of handling potentially malicious software. For example, you should never click on an email attachment, even if it looks innocuous. The problem is that some malware is very good at looking like perfectly safe file types, such as PDFs, Word documents or pictures, so these things aren't always obvious (which is why they work so well at being spread like wild fire.) The best thing you can do is educate yourself. Learn as much as you can about malware, how it works and how it spreads. Learn about the things that viruses can, and can't, do. This article from Ars Technica is a great start! Viruses, Trojans, and Worms, Oh My: The basics on malware is the second installment of Ars Technica's Guide to Online Security, and a good read for anyone who wants to know more about malware and how to protect themselves from it. From here, you can always look up information on Wikipedia or other security websites and blogs. There's a wealth of information out there, so take advantage of it! And, if worse comes to worse, you can always give NEPA Geeks a call. We specialize in virus removal and would be more than happy to assist you with any questions you might have....
28 Jan Phishing Scheme Poses as Facebook Security to Steal Passwords
We are urging Facebook users to be on the lookout for a phishing scheme that is looking to steal your passwords. NakedSecurity recently published a blog post stating that scammers are now using Facebook apps to dupe unsuspecting users out of their Facebook password. The scheme involves sending users an email purporting to be from Facebook's security team, telling them that their accounts have been found in violation of Facebook's terms of service and asking them to click on a link to log in and verify their account to avoid suspension. If you get this message in an email, don't click the link and DON'T enter your username and password! To keep yourself safe, don't reply to messages from ?ac?bóok S?cur?y or click on links in emails that ask for your passwords. No one from Facebook will ever ask for your password, and users should be wary of anyone posing as such. Looks can be deceiving Part of the scheme being used by the bad guys is a Facebook app designed to look like a legitimate Facebook security page. [caption id="attachment_1742" align="aligncenter" width="300"] Fake Facebook security page, via NakedSecurity.[/caption] This is a screenshot of the Facebook app users will see when they click on the URL in the email. Notice that the name ?ac?bóok S?cur?y is a made-up jumble of characters that were arranged to look like they spell out the words "Facebook Security." The app has nothing to do with Facebook and isn't from Facebook's security team. Pay special attention to the URL in the screen shot below: This screenshot, provided by NakedSecurity, shows what users will see if they click on the link in the email. Notice the incorrect spelling of the word "suport" in the "account_suport_help" part of the URL. This obvious, glaring flaw might be easy to spot by people accustomed to seeing these kinds of scams, but they can look pretty convincing to many who are less "tech savvy." Also be aware that this kind of scheme is very easy to replicate and may use any combination of addresses and designs to fool users into willfully handing their passwords over to criminals. ...
18 Jan “Secure Message” Scam Targets Victims in Email Malware Attack
Secure Message Scam Targets Victims in Email Malware Attack We all hate getting spam -- unwanted junk email -- in our email inboxes, but in this case, it's not just unsolicited ads clogging your inbox, it's a vicious virus attack. [caption id="attachment_1694" align="aligncenter" width="300"] An example of the secure message scam email, care of NakedSecurity.[/caption] A new twist on an old scam has victims of a malicious software attack download a computer virus through an email attachment disguised as a secure message from banks and other firms. Be wary of emails with a subject line that says something similar to "You have received a secure message," and then attempt to get you to download ZIP files (such as securedoc.zip) to read the message. A trojan virus, known as Troj/Zbot-DPM, could be inside and used to get control of your computer. Computer security site NakedSecurity wrote a blog post giving detailed information on the malware spam attack. What is a Trojan Virus? Remember the tale of the Trojan War, where the Greeks build a large, wooden horse and hid soldiers inside? The people of Troy, thinking the horse was a gift, brought it through their impenetrable gates. Once inside, when the people of Troy least expected it, the Greek soldiers unleashed their attack and gained a swift victory. That's essentially what's happening when you download this "secure message" ZIP file -- you're allowing a virus to infect your computer and give control of it to some unknown computer criminals. What to do if you receive this secure message scam First of all, don't click on the link inside or open any attachments that come with it. Simply delete the email and you should be ok. Even if the message looks clear or is from a source you trust, it could be a spoof set up by the scammers. Unless you fully trust the source and can identify the contents, you should be extremely wary. If you've already clicked on the link, downloaded the file and suspect you may be infected, it's not too late to correct the problem. Just give us a call at 570.474.5100, and we can set up an appointment to do a full virus removal on your computer....
13 Jan Patch update eliminates Java exploit infecting computers with FBI virus
Oracle Patch Eliminates Java Exploit Being Used to Install FBI Virus Good news! Oracle has released a patch to update Java. This update will fix the vulnerability that was being used to install the Reveton Ransomware (aka FBI Virus) on unsuspecting users' computers. Simply follow the instructions on the Java installer page to get the latest version of Java installed on your computer. If you have been infected, give us a call at 570.474.5100 to set up an appointment or bring your computer to us to have the virus removed. Click here for directions to our office in Mountain Top, PA. Java Exploit Eliminated, Virus Remains At Large On Sunday night, Naked Security published a blog post alerting everyone that the patch was now available. Once installed, the latest version does eliminate the current Java exploit. However, the virus is still out there and can infect computers that are not running the latest version of Java. There also still exists other ways to be infected by the virus. We therefore recommend leaving Java disabled unless there is a specific need for it. Other vulnerabilities may still exist, and there is always the threat of new Java exploits in the future. Unfortunately, there is no way to make the web 100% safe. If you do need to keep Java enabled, make sure you trust the applets that you need to run and be wary of sites that load malicious applets without your knowledge. The FBI Virus, Explained [caption id="attachment_1346" align="alignright" width="300"] FBI malware locks your computer, demands ransom to unlock it.[/caption] In case you missed it, on Friday we published a blog post about a recent Java exploit that was installing the so-called FBI Virus on users' computers and how to disable Java to avoid infection. The FBI Virus locks users' computers and displays a bogus message purporting to be from the FBI, stating that the computer was being used for illegal activity (pirated software, illegally downloaded movies and music, child pornography and hacking, for example) and the owner would need to pay a fine to restore their computer. In actuality, the message had nothing to do with the FBI and was, instead, from computer criminals demanding a ransom. As was often the case, this ransom was more expensive than what we would normally charge to remove a virus and carried no guarantee that the computer would ever be unlocked. As such, we still recommend customers and clients bring their computers to us if they suspect they have been infected rather than paying the amount being demanded by the message. Again, the message is NOT from the FBI and carries no legal weight. We'll have more information as the situation develops, but at present, this most recent threat seems to be eliminated....
11 Jan New Java exploit infects computers with FBI Virus
Java Exploit Infects Computers with FBI Virus According to a blog post on Malware Bytes' website, there's a new Java exploit that is being used to infect computers with the infamous FBI virus. The suggested solution is to disable Java. We have links to instructions on how to disable Java listed below. [UPDATE - 1/13/2013 - The latest version of Java eliminates the exploit being used to infect computers. We still recommend disabling Java, however, be sure to install the latest version of Java -- Version 7, update 11 just in case you absolutely need Java on your computer. And if you have been infected, give us a call at 570.474.5100 to set up an appointment or bring your computer to us to have the virus removed. Click here for directions to our office in Mountain Top, PA.] What is the FBI Virus? [caption id="attachment_1346" align="alignright" width="300"] FBI malware locks your computer, demands ransom to unlock it.[/caption] The Reveton Ransonmware, or The FBI Virus as it is more well-known, locks your computer and displays a message that says the FBI is aware that your computer has been used for some "illegal activities." The virus then demands that you pay an outrageous fine or risk further prosecution. In truth, the message isn't from the FBI; it's a scam by computer criminals looking to extort money from any user who falls for the scheme and pays up to have their computer restored. The FBI Virus has been spreading for quite a while, popping up on various tech news sites and security blogs. We first alerted users about the FBI Virus on this blog back in November, warning victims to NOT pay the fine and, instead, bring their computer in to be professionally cleaned. If you have been infected, we still stand by that original recommendation. However, if you haven't yet been infected, we're now suggesting that you disable Java to prevent the virus from infecting your computers. How to disable Java Java is a computer language used to make applications that run in your web browser. It requires a plug-in be installed in your web browser to run these applications. Naked Security, a computer security blog maintained by SOPHOS.com, lists several ways on how to disable the Java plug-in, depending on your preferred web browser. Listed below are direct links to the instructions for each browser: How to disable Java in Internet Explorer How to disable Java in Firefox How to disable Java in Chrome How to disable Java in Safari How to disable Java in Opera Pay the bad guys, or pay us to clean your computer? Choosing to simply pay the ransom to unlock your computer might seem like a cheaper, more convenient way to get rid of the problem. However, you have no guarantee that the computer will be unlocked. Furthermore, your computer will still be infected. That's why we suggest you bring it in to us at NEPA Geeks. We'll make sure the virus is gone and that your data is intact. We charge much less than the amount being demanded and have tools that can help prevent future infections. You get your computer restored to fully-functioning condition AND the bad guys don't get any of your hard-earned money. Doesn't that sound like the smarter alternative? It is. Remember: if you've been infected, DO NOT pay the fine being demanded by the virus. It is definitely NOT from the FBI. Further, if you haven't been infected, we suggest that you disable Java using one of the techniques listed above. Let's stay safe!...
09 Jan A warm welcome to our latest web hosting clients Antipode
A warm welcome to our latest web hosting clients, Antipode! We love sharing news about new clients who have decided to make NEPA Geeks their web-hosting home. For example, the latest clients to settle-in and set up shop with NEPA Geeks are Antipode -- a troupe of geek belly dancers from State College, PA. From their site: Antipode is a geek belly dancing troupe hailing from State College, PA. Fusing the theatrics of acting with a mix of cosplay, pop-culture, and off- beat humor Antipode brings the audience not just dance, but full geek entertainment. I first saw Antipode dance at the 2012 NEPA BlogCon. The troupe's dance theme that day was "Internet Memes," incorporating their dance routines with costumes, music and other props to recreate popular internet sensations that people couldn't stop talking about and sharing on Facebook, Twitter and Tumblr. The audience was very happy to see them dance as we all took a break from learning about blogging to eat some lunch, relax and network with other bloggers and future bloggers. Would you like to know more about Antipode? For more information about the troupe -- including pictures and information on how to book them for an event -- just visit their website at AntipodeBellyDance.com, proudly hosted by NEPA Geeks. Not only will you learn more about them, you'll also find the answer to a great question: Just what is an "antipode," anyway? While you're at it, take a look at the hosting packages we offer. Our variety of packages will easily fit within your budget. We also offer content and SEO services, just in case you need some extra "oomph" or "pizzazz" to get traffic to your site. Give us a call, today! You'll be in good company with other satisfied clients, like Antipode!...
07 Jan NEPA Geeks PC repair business mentioned in the local news
NEPA Geeks PC repair business mentioned in the local news It's always great to hear good feedback on our little PC repair business up here in Mountain Top, but this recent article in the January 2nd edition of The Mountain Top Eagle blew us away! I took a picture of the print article (as seen below) but you can read the whole thing on this blog post by Stephanie Grubert from The Mountain Top Eagle. We just wanted to take this moment to thank Stephanie for her kind words. It was a pleasure working with her and helping to get her computers and iPad back in working order. We never expected to open the paper and see something like this! As always, we look forward to each and every opportunity to help people out, whether they need a virus removed, a custom computer built or an iPhone screen replaced. We promise not to let this recent publicity go to our heads, so if you need help, feel free to give us a call. Although, no autographs, please....
04 Jan Watch out for DNS Services Invoice Scam
Watch out for DNS Services Invoice Scam Have you recently received an invoice from a company called DNS Services charging you for "DNS backup services?" Be warned, it's not an invoice, it's a solicitation from DNS Services. A client recently sent us a copy of an "invoice" he received from DNS Services -- DNSsvc.com, a DNS backup provider. Take a look at the picture below to see the actual letter they received: [caption id="attachment_1653" align="aligncenter" width="448"] (click the image to see full-size)[/caption] On the surface, it looks like a bill, complete with a mailer to send in with a payment of $65. However, if you look closely (the block of text below the total in the account summary details box), you'll notice that it's actually "a solicitation for the order of goods or services, or both, and not a bill, invoice, or statement of account due. You are under no obligation to make any payments on account of this offer unless you accept this offer.” In other words, it's not a bill; you owe nothing. DNS Services simply wants to charge you so they can provide a service that you are not yet receiving. Think of this more like an advertisement -- albeit, one so cleverly disguised to look like a bill that unsuspected customers might feel compelled to pay it, and that's the problem. Unsuspecting customers have been sending DNS Services money for a service they didn't want or need. What's worse, we've read first-hand reports from other sites warning about DNS Services that a lot of these folks are having trouble getting their money back. But what about a DNS backup service? Is this a service you actually want or need? Probably not, especially when you consider that NEPA Geeks already provide a backup domain-name server for web sites hosted with us. In general, 2 domain name servers are all you normally need. A DNS is, basically, an internet-connected computer that resolves a web address (the WWW.COM) to the computer where your website is hosted. It's very rare that these servers go down. Therefore, a backup service isn't really needed. In short, if you receive an "invoice" from DNS Services, throw it away. You owe them nothing. And would you really want to do business with a company that conducts themselves in this way? Probably not....
02 Jan How to fix iPhone’s “Do Not Disturb” not turning off
iPhone's Do Not Disturb not turning off? Not getting notifications on your iPhone, iPad or iPod Touch today? Wondering what the little moon icon on your status bar means? Read on. If you noticed that iPhone's Do Not Disturb won't turn off after January 1st, 2013, you aren't alone. This morning, I noticed that the crescent moon "do not disturb" icon on my iPhone was still being displayed in the status bar at the top of screen despite being scheduled to turn itself off after 7 a.m. I didn't think much of it until I learned that this is a bug that is affecting a lot of iPhone users. For some reason, if you set the feature to turn on December 31, 2012, it doesn't automatically switch itself off after January 1, 2013. Note that the built-in alarm in iOS still functions (as mine did, this morning) but you'll be missing notifications, including those from other alarm apps that you might be using. Fortunately, it's very easy to fix. To fix the Do Not Disturb not turning off bug, just turn it off. Seriously. The Do Not Disturb function will resume functioning as normal, turning back on and off at the scheduled times. Easy, right? Well, just in case, here's how to fix the iPhone's Do Not Disturb bug. Step 1: Tap the "Settings" icon on your iPhone. Step 2: If the Do Not Disturb switch is set to On (as seen in the picture below,) simply tap the switch to turn it off. Notice that the scheduled "switch on" time returns as seen in the next picture. And that's it! We're following along just to see if there are any other problems waiting to pop up since the date change, but this seems to be the one affecting most users. [Update] It seems that, while this does turn off the Do Not Disturb feature, it doesn't completely fix the problem. You can still turn the feature off and on at will, but the automatic scheduler doesn't work. The Do Not Disturb feature can only be switched on and off manually at this time. Apple is aware of the problem but has issued a statement that the bug will not be fixed until January 7. So, it turns out that the fix isn't as simple as we were hoping, but at least it can be routed around until Apple gets around to correcting in come Monday....
19 Dec NEPA Geeks now accepts payment via Square Wallet. What is Square Wallet?
Paying invoices just got easier with Square Wallet NEPA Geeks is proud to announce that we are now capable of accepting payments with Square Wallet. [caption id="attachment_1612" align="alignright" width="240"] Square Wallet payments now accepted at NEPA Geeks[/caption] What is Square Wallet? Square Wallet is an application that runs on your smartphone. It stores all of your credit card information and allows you to make transactions right from your phone whenever you're at a store that accepts Square Wallet payments. It works on iPhone and Android smartphones. (Check here for Android availability.) How to use Square Wallet Using Square Wallet is simple and quick. It's just like using a credit card, but there's no need to remove your wallet or swipe the card through a reader. In fact, with "hands-free" payments activated, you don't even have to remove your phone! Just say your name at the Square Wallet-enabled register and the clerk will know it's you when your picture pops up on the screen. You get all of these benefits, and it's still just as safe as paying by card! More Options, More Benefits When you use Square Wallet, you'll be able to see all of the other businesses in the area that also use Square Wallet. Many will even be offering deals, rewards and discounts just for using it. For example, we offer 10% off your first purchase when using Square Wallet at NEPA Geeks. You can use Square Wallet to send and receive gift cards, unlock special rewards and much more. It works on both iPhone and Android, so if you haven't already done so, sign up today! And be sure to use it when you stop in to get 10% off your first purchase at NEPA Geeks....
07 Dec NEPA Geeks’ Gift Certificates are a great deal!
Give the gift of healthy computing with NEPA Geeks Gift Certificates! [caption id="attachment_1579" align="alignright" width="403"] Mr. T. Claus says, "I pity da foo' who don't buy NEPA Geeks' Gift Certificates for their loved ones this year! Ain't dat right, Nancy Reagan?"[/caption] With roughly 17 days left until Christmas, you might be trying to square away a few of those hard to buy for people who seem to have everything. Gift certificates are a popular option for most people because they allow the gift-giver the chance to offer something meaningful without spending money on an unwanted gift. If you're looking for just such a gift, NEPA Geeks is here to help. Yes, we offer gift certificates! Many friends and relatives will be receiving new gadgets and computers this year. Wouldn't it be great if they had some kind of insurance policy for when things go wrong? A gift certificate from NEPA Geeks will help offset the cost of repairs and maintenance to get those problems taken care of, and they can be applied to anything we do! Repairs, maintenance, service calls, custom installs, web hosting and more. Do you know someone who is “accident prone,” who tends to drop their phone or spill drinks into their keyboards? We can help! Do you have an older family member who refuses to ever give up their old desktop PC? We can get it tuned-up and up-to date for them! Just purchase an NEPA Geeks gift certificate for any amount and they’ll be able to redeem it with us for repairs and other services. We use PayPal, so it's safe and secure to use, just like cash! If you have any questions, about NEPA Geeks' gift cards, just give us a call and we'll be more than happy to help you. 570.474.5100 or email us at staff@nepageeks.com ...
05 Dec Facebook, Instagram and Twitter are fighting over your pictures
Facebook, Instagram and Twitter are having a tiff about who gets to see your pictures. [caption id="attachment_1566" align="aligncenter" width="453"] When social networking sites fight, users lose.[/caption] There's a reason your Instagram photos aren't showing up properly on Twitter today. The New York Times goes into the details of the story, but the basic idea is that, ever since Facebook bought Instagram, the relationship between Instagram and Twitter has been falling apart. Those relationship problems came to a head today, December 5, when Instagram decided to stop supporting embedded photos within Twitter, causing them to show up cropped and off-center. Kevin Systrom, Instagram's chief-executive, confirmed his company's move and added that Twitter will be completely cut off from embedding photos in the future. As Instagram moves to make their photo-sharing more social by integrating with Facebook, Twitter has also been making moves to add the ability for Twitter users to add photo filters in much the same way Instagram does, negating the need for Instagram. In the meantime, the ability to "sync users" -- the ability to place an @ in front of a Twitter user's name and direct the photo at them -- is going away, as Twitter will no longer support the function on Instagram. It's not clear who all of this bickering is supposed to benefit, but one clear loser is us: the users. When social networking sites decide to stop getting along, it makes it difficult for everyday users to share photos with friends and family. Not all of your friends are on Twitter, just as not everyone you follow on Twitter use Facebook, so to cut off a large group of users not only keeps them from interacting with the things you do, but it can hurt your brand if you rely on those networks to bring traffic to your site. So, what can you do? Unfortunately, there isn't much you can do about Twitter and Instagram not getting along, but if you hosted your content on your own website, you'd be able to share it with everyone -- regardless of what network they choose. And, by using a content management system such as WordPress, there are plugins available that will allow you to share images easily with both networks, just like before. Why rely on the terrible choices and business tactics of others when you can do everything you want on your own site? That's true freedom!...
26 Nov Top 5 Reasons You Need A Blog! – A guest post by Darling Stewie
Our good friend and fellow blogger, Darling Stewie, wrote up a terrific guest blog post to give everyone her top 5 reasons you need a blog. If this post doesn't convince you to purchase a hosting account and set up your blog, right away, nothing will! Get ready to have your ironic, artisanal, hand-knitted socks knocked off. Top 5 Reasons You Need a Blog! Hey NEPA Geeks blog readers! This is Darling Stewie of DarlingStewie.com stepping in for a fun guest post to bring you some deets on why you should really consider having a blog. I've had DarlingStewie.com for 2 years, and helped run several other area blogs including NepaBlogCon.com/Blog and PepperJam.com/Blog - and I love it! But...
21 Nov Small Business Saturday
NEPA Geeks are proud to announce that we will be taking part in Small Business Saturday, this Saturday, November 24. What is Small Business Saturday? Small Business Saturday is a program sponsored by American Express to support small businesses that create jobs, stimulate the economy and help enrich their communities. American Express founded Small Business Saturday back in 2010 as a way to help small businesses increase their exposure. Last year, over 100 million people shopped at independently-owned businesses, and the hope is that we can all help to increase that number significantly! American Express offers tools that will help us, as a small, independent business, reach out and offer extra benefits and services to our customers. As part of the NEPA Small Business Saturday group on Facebook, we're honored to be a part of what they are doing to promote small business in NEPA! What does that mean for you? This Saturday, November 24, the NEPA Geeks office will be open and ready to serve you with any computer issues you might be having. Even if you don't have a problem with your current computer, we can help you upgrade to a new computer, order parts for your existing system or even set you up with a new website or blog! We're offering free consultations, 15% off computer repair services and 10% off web hosting! And, to top it off, NEPA Geeks offers its Complete Computer Overhaul package for only $99.99 -- a huge savings over our usual price of $129.99. Call or stop in on Saturday, November 24th. We'll be here to help you learn more about what NEPA Geeks can do for you! Our number is 570.474.5100 and our address is 108 N. Mountain Blvd. Suite B, Mountain Top, PA 18707. We can also be reached at staff@nepageeks.com For more information on Small Business Saturday, visit ShopSmall.com....
19 Nov How to defrag your hard drive
How to Defrag Your Hard Drive When was the last time you defragged your hard drive? If you're like most computer users, it's probably been a long time. If you answered, "Never," or, "I don't even know what that is!" we're going to show you, now. What is defragging? In simplest terms, it's taking all the bits and pieces of information stored on your hard disk and reorganizing them. Think of your computer's hard disk as a big closet where everything gets tossed. Shoes, clothes, old cell phones, other gadgets and odds and ends...
15 Nov Password Security: All but Dead in the Digital Age
Feeling safe and secure about your passwords? You might want to take a seat, because that is about to change. [caption id="attachment_1451" align="alignright" width="300"] How secure is your password? It might not matter anymore.[/caption] If you read only one article on password security this year, make it this one. In it, Mat Honan lays waste to the idea that passwords are anything but an inconvenience to hackers. After taking over his Apple, Twitter and Gmail accounts, hackers destroyed his digital life in the span of an hour. Documents, data -- even pictures of his 18-month-old daughter were wiped out. Think it can't happen to you? Think again. Do you reuse the same password on multiple sites? Do you use "dictionary" words less than 16 characters in length? Do you have your email account linked to multiple accounts, such as Twitter and Facebook? When you need to reset a password, is that the same email address the notification goes to? I have news for you: you are vulnerable. Learn some of Mat's suggestions and tips to keep your data more secure, such as setting up double-authentication on your accounts when offered, setting up an email address exclusively for password resets that isn't linked to anything else and the best way to answer those "personal" questions, such as, "What was your first car?" and "Where were you born?" Proficient hackers can usually answer these questions with a few strategic Google searches! The article may be a bit lengthy, but it provides an eye-opening education into what it takes to keep your data secure, these days. Note that we aren't suggesting you retreat from the web, just that you exercise a little more caution in what kind of information you publish and how securely you lock it down. Be safe!...
12 Nov Malware extorts money from victims by posing as the FBI
Don't fall for phony FBI malware! [caption id="attachment_1346" align="alignleft" width="300"] FBI malware locks your computer, demands ransom to unlock it.[/caption] This article on Ars Technica points out that so-called "ransom ware" is becoming an increasing cause for concern as it is responsible for bilking $5 million a year from victims. The malware in question disables the victim's computer, displays a serious-looking warning and then demands payment to unlock the machine, insisting that if the victim doesn't pay up, they will be arrested by the FBI. As scary as it may seem, it's not real. Don't fall for this scam! As the unsuspecting victim may not be aware, this message DOES NOT come from the FBI. You are not obligated in any way to pay this "fine," as it is simply an act of extortion. Again, this message is not from any law-enforcement agency -- it is a scam, an illegal operation only looking to extort money from helpless victims. It is the result of malware that has infected your computer and will need to be cleaned out immediately. DO NOT enter your information, and DO NOT pay the "fine!" If you see this message on your screen, or suspect that you may have been infected, we urge you to contact NEPA Geeks immediately so that we can evaluate your system and determine a course of action. Even if you feel that the amount is small and you simply want your computer to work again, don't give them what they want! There is no guarantee that the bad guys won't simply disable your computer again, demanding more money. The best course of action is to have us remove the malware for you. In the long run, it will cost far less to clean the system while dramatically reducing the risk that your personal information could end up in the hands of criminals. Be safe, be smart! We also offer software that can prevent such infections from happening in the first place. Contact us so we can help!...
05 Nov How to get started blogging – Part 4 – Your first blog post
How to get started blogging with NEPA Geeks - Part 4 - Your first post! Welcome to Part 4 of our series on blogging. So far, we've talked about what blogging is, how to buy a hosting account on NEPA Geeks to host your blog and how to set up your first blog using our easy hosting solution. Now, we'll show you how to make your first blog post and a simple "About Me" page. If you haven't done so already, log into your WordPress blog. (In case you've forgotten, to log in, simply add /wp-admin/ to the end of your domain name. For example, yoursite.com/wp-admin/ Enter your username and password in the boxes on this page and you're in!) Click on the Posts link in the left-hand menu or hover your mouse pointer over the word Posts and click on "Add New." You'll notice a box with the text "Enter title here" in grey text. This where you'll put the title/headline of your first blog post. You can enter whatever you'd like, but a short "Hello, World!" or "Welcome to my blog" message will do for now. Below the title box is a much larger box where you'll enter the body of your blog post. At the top of the body box is a small icon you can use to upload images and other media (such as music or video files). We'll focus on that later, but for now, the icons slightly below that are the text formatting buttons where you can make your text bold, italic, add strikethrough text, bullet lists and more. Feel free to play around with them just to get yourself acquainted with how they work, but they won't do much until you have some text entered into the body box. By now, you're probably familiar with applications such as Word or OpenOffice and have a pretty good idea of how to enter and format text. Or maybe you've used GMail, Facebook or other social networking sites and have seen similar setups to the one you're seeing here. If so, WordPress works much the same. Once you've got some text and a title you're happy with, go ahead and hit the "Preview" button. This will let you see what the post will look like on your blog when it's published. Don't worry about how it looks if you're not happy with it, yet. No one can see this post, it's just a preview that is only available to you. Ready to publish your first blog post? Go ahead and hit the blue "Publish" button to the right of the body box. Alternatively, you can save a draft to work on later or tell WordPress to publish the post at a later date, automatically. It's up to you. Many people like publishing their posts as soon as possible while others like to write a few blog posts at once then set WordPress to automatically publish them throughout the week, freeing them up to work on other things. Remember: you can always edit posts even after they've been published. You can also set them back to draft mode or remove them entirely by deleting them. Once deleted, though, they're gone forever, so be careful! Now, let's create a Page. Pages are useful for giving people quick access to important information about something. For example, an "About" page that talks about you, your blog, products or services you might offer, links to other blogs, or anything you want people to see. You can always reference or link back to a past blog post, but pages can have a tab or link at the top of your blog for a more prominent display, where they're sure to be noticed by visitors to your blog. To create a page, from the Dashboard of your blog, click on Pages (or hover the mouse pointer above the Pages link and click "Add New" in the menu that pops out. Look familiar? No, you're not experiencing deja vu… The way you build a new page in WordPress is exactly the same way you write a new blog post -- even down to who can see it, when it gets published and how it looks. You can even edit and delete pages. It's exactly the same! This is what makes WordPress so special; you can build an entire website right from the same interface, and it's as easy as composing an email or creating a new document in Word. From here on out, the sky is the limit. You have control over how the blog looks, what it's used for and what you say on it. Welcome to the world of blogging. Have fun!...
05 Nov How to get started blogging with NEPA Geeks – Part 3 – building your blog
How to get started blogging with NEPA Geeks - Part 3 - Building your blog In Part 2 of our series on how to get started blogging with NEPA Geeks, we showed you how to go through the process of purchasing an NEPA Geeks hosting plan. Now, we'll show you how to build your blog. If you haven't done so already, log into your account at http://www.nepageeks.com/hosting/clientarea.php Once inside, our one-click setup tool makes it a snap to get a WordPress blog installed on your hosting account. Simply click on the link to Products/Services in the right-hand side of the screen, or from the drop-down menu, click "Services" and then "My Services." On the next page, scroll down and click on the "View Details" button. It looks like this: Next log into cPanel by clicking the "Login to cPanel," which looks like this: Once in cPanel, scroll down and look for the "Fantastico De Luxe" icon (it looks like a blue smiley face, as pictured below): Fantastico will allow you to install more than a dozen services and platforms, but for now, click on WordPress under the Blogs section of the menu to the left. Next, click "New Installation." If this is going to be your main site, leave the install directory blank. Fill out the rest of the forms as you see fit and then click "Install WordPress." Assuming everything goes correctly, click "Finish Installation." Make sure to write down your username and password for your new blog. Once WordPress has been installed, it's time to log in to your WordPress blog. To log in, simply add /wp-admin/ to the end of your domain name. For example, yoursite.com/wp-admin/ Enter your username and password in the boxes on this page and you're in! Now you're ready to make your first blog post, which we'll cover in Part 4 of our series on how to get started blogging with NEPA Geeks....
05 Nov How to get started blogging with NEPA Geeks – Part 2 – Purchasing Hosting
How to get started blogging - Part 2 - Purchasing a hosting package If you've read Part 1 of our series on how to get started blogging and are ready to take the next step, read on. By now, you are eager to get started setting up your own very own blog. One of the great benefits about having a hosting account with NEPA Geeks is that you get full control over your blog. When it comes to the design and look of your blog, you aren't limited to a handful of templates that can't be changed. You can add plug-ins that increase your blog's reach and functionality, and it's a lot less expensive to have your own domain name with us. If you haven't chosen a hosting service, NEPA Geeks offers several options designed to suit the needs of a variety of customers. To get started with us as your host, the first thing you'll want to do is follow this link to purchase a hosting package. Feel free to explore each of the available options, but more than likely, entry-level bloggers who are just getting started will probably prefer NEPA Geeks Micro hosting package, with just enough features for you to post plenty of text, pictures and more. Once you've chosen a hosting package you have a few options to consider when it comes to your domain name. If you have a name you want, our form will allow you to see if it's available for purchase. However, if you have a domain name with another registrar and wish to transfer it to us, or if you just want purchase a hosting package and keep your existing domain where it is, you can do that, too. For now, we're going to assume that you want to purchase a new domain name. After choosing an available domain name, you'll have several options on how long you'd like to register it for. Note that if you register your domain with us and purchase an annual, biennial (2 years) or triennial (3 years) hosting package, your domain registration will be free. From there, simply proceed to the checkout and finish the purchasing process. Soon, you'll receive an email with your login information to get into your hosting account. Once you're able to log in, you'll be ready for Part 3 of our thrilling guide to setting up a WordPress blog with NEPA Geeks!...
05 Nov How to get started blogging with NEPA Geeks!
How to get started blogging with NEPA Geeks Have you often thought about blogging but didn't know where to start, or how to begin? It's remarkably easy, and a lot of fun. If you know how to send email or post status updates to Facebook, you've already got the basics. Now, you just need to take a few more steps, and we can help! We've prepared a series of posts on how to get started blogging with NEPA Geeks, from choosing a host to setting up your blog to making your first post. Ready to get started? Read on! What is blogging? In simplest terms, a blog (short for "web log") is like an online diary. However, the concept can go far beyond that, extending to the point where a blog can be like a daily newspaper or magazine. A blog can have a single author, just writing about their day to day lives, or a blog can have a team of writers and editors, covering a wide variety of subjects and topics. It can focus on a single subject, a community or an organization. The post you are reading right now, for example, is published in a blog that is maintained by myself and the owner of NEPA Geeks, Jason Percival. We write about various technology issues as well as what's going on here at NEPA Geeks. If we have news about new services and products being offered, you can be sure to learn about it here! It's a great way to keep in touch with customers. The NEPA Geeks blog is running on a software platform called WordPress. However, WordPress can be used to do much more than simply run a blog. Each of the pages that make up this website were also created and published using WordPress. That's the versatility of this powerful platform! That's also why we recommend WordPress so heavily, if you should decide to set up your own blog. Don't worry if a lot of what you've read so far sounds really complicated. In the next few posts, we're going to show you how to use NEPA Geeks' hosting service and WordPress to set up a simple blog and an "About Me" page. We'll even show you how to get your own domain name! When you're ready to continue, follow this link for Part 2 on how to get started blogging with NEPA Geeks....
05 Nov NEPA Geeks – Reliable Web Hosting For Your Site or Blog
Did you know that NEPA Geeks offers reliable web hosting for your site or blog? It's true! We're not just your local computer repair shop, we're also your local hosting solution! What is web hosting? A web host is a high-speed Internet-connected computer with a vast amount of storage space. It can either hold personal files that you wish to back up or it can hold your website or blog and display it to visitors who come to your website. Whether you're running a home business, a corporate site or just want to set up a personal WordPress blog, NEPA Geeks offers a variety of hosting packages that are suited to fill your needs. We offer one-click setup for dozens of platforms, allowing anyone to easily and quickly build a website. All of our packages run on Linux-based servers, so you can count on them for rock-solid performance and dependability. For customers with more advanced needs, we also offer Virtual Private Servers, giving you the benefit of having full access to the configuration and management of your server. These packages are recommended for customers who have outgrown shared hosting plans and need a much more robust hosting solution. Many of our customers who are interested in selling products through their website may be happy to know that we also offer SSL certificates. A Secure Socket Layer connection ensures that information between your website and your customer is secured from hackers who would tap in to record the information being passed along. SSLs can also be useful for securing logins to your website, ensuring that users' data is secure during the login process. NEPA Geeks offers static IP address allocation, which you will need for an SSL certificate. Certain other web apps and software platforms will also require a static IP address allocation. Along with our hosting packages, we also have server data backup services offering from 10GBs of storage up to 1TB of RAID5 storage, with unmetered inbound bandwidth. (Outbound bandwidth is limited to 500GB/month.) As you can see, when it comes to hosting services, NEPA Geeks has you covered. Give us a call at 570.474.5100 or email us at staff@nepageeks.com and we'll be happy to discuss hosting solutions for you!...
31 Oct Hurricane Sandy Update: Back in business!
Hurricane Sandy has mostly passed our area, yet she's still dumping large amounts of rain and snow on many areas along her path. We were very lucky that the worst we had to deal with was a power outage for a few hours, considering the devastation many people saw. Our thoughts are certainly with those who have lost their homes or loved ones. As I came in to work today, I was surprised to see a detour around a section of Route 309 between Hazleton and Mountain Top -- which has since been opened so that normal traffic flow may resume. In the meantime, Jason and I are here in the office and ready to return to business as usual. Jason replanted the NEPA Geeks' computer repair sign in front the office and we are open for business! On the blogging front, we're working on a series about how to build a blog using NEPA Geeks as your hosting solution. If you've always wanted to start blogging, keep your eyes on this space to learn more about what NEPA Geeks can do for you! As always, if you have any questions or need help with your computers, remember, we're always just a phone call away!...
28 Oct How to protect your electronic equipment from Hurricane Sandy
Learn how protect your electronic equipment from Hurricane Sandy [caption id="attachment_1279" align="alignright" width="300"] From the National Hurricane Center in Miami[/caption] Hurricane Sandy is rapidly approaching, and this thing is set to make a historical impact on our area. Governor Tom Corbett has already announced that we are in a state of emergency, and many parts of New York and New Jersey are shutting down. The immediate future is looking pretty scary, but for the moment, the weather is calm. This is the time to get things done and learn how to protect your electronic equipment, before it's too late. By all means, your family's safety should be first and foremost on your mind. It would be a shame if your computer got fried and wouldn't turn on anymore, but that's nothing compared to the immeasurable loss of losing a loved one. Therefore, water, food, medicine and an evacuation plan are things you need to be working on immediately. However, if you've taken care of all that, here are some last minute things you need to do to ensure the safety of your computers and electronic equipment. Backup Your Data First of all, make sure you have your data backed up to an external hard drive or online data storage solution. This is something you should be doing regardless of an impending storm. Family photos, documents, school or work projects, emails and other important information that you don't want to lose should be taken care of immediately. But don't just assume that the data is safe simply because it's on an external disc, make sure the disc is kept somewhere safe, away from flood waters, extreme temperatures and sources of physical harm. Check Batteries for Power, Fuel-Up the Generator If you have vital equipment that needs to be powered at all times, now is a good time to make sure the battery backup system/generator is working and can maintain power for an extended period of time. If the power grid goes down, there's a possibility that it could be out for a few days. Charge up cell phones, flashlights, portable radios and anything else you might need that has a battery. Make sure the generator has fuel. Also, NEVER run a gas or diesel powered generator inside the house. Deadly levels of carbon monoxide gas can quickly build up and kill you. Likewise, a malfunctioning furnace or blocked-up chimney (for those of you building a fire in the fireplace to keep warm in the event of power loss) can quickly contribute to dangerous carbon monoxide levels. Learn and look for the warning signs of carbon monoxide poisoning and keep the house well ventilated. Flood Protection On the other side of the spectrum, a power surge or lightning strike can damage or destroy equipment. You should keep whatever you don't need unplugged and safely put away -- preferably in a high area of the house, just in case of flooding. Speaking of floods, if you live in an area prone to flooding, do a quick sweep of the basement/lower levels of the house to make sure that anything important is moved high up, out of the reach of flood waters. Sealing them in plastic would add extra insurance from water damage. Document Everything Sometimes, despite all precautions, accidents still happen. For that reason (and, more importantly, for the reasons we can't think of) everyone should have some kind of insurance. It might be too late to get a policy, but if you already have one, now is the best time to take pictures and document everything of value in your home. Electronics, vehicles, external views of your house...
25 Oct Virus removal on a professional level
Professional Virus Removal, Right Here in Mountain Top, PA When you drive a car, you buckle your seatbelt, right? When you ride a bike, you wear a helmet. And you wouldn't jump out of a plane without a parachute, would you? So why doesn't your computer have any antivirus software installed? You know that viruses and spyware are dangerous, but do you know how to keep your computer safe from malware? NEPA Geeks have the tools keep you safe It's about protection -- not just to keep you safe, but to give you peace of mind. Leaving your computer open to malware is like inviting burglars to come in and steal your valuables. However, when your computer gets hacked, the hackers don't just walk out with a TV and some jewelry, they get the pictures of your family, emails, passwords and financial information. They grab whatever they can from your computer, and you probably don't even know they are there. NEPA Geeks can help you avoid this scary scenario. Professional Virus Removal We're locally owned and operated in Mountain Top, PA, just a few minutes from Wilkes-Barre, Scranton, Dallas and Hazleton. Bring your computer to us, and let us take a look at it. We offer a powerful anti-malware application that can keep your computer safe and secure. If it's been infected already, we'll clean out the spyware, viruses and other malware that is plaguing your computer and get it back up to running like it was new. We'll even show you how to prevent getting infected again. Call us today! So, if you want peace of mind AND a computer that runs like new, stop in and see us, or give us a call. Our address is 108 N. Mountain Blvd Suite B Mountain Top, PA 18707. Our phone number is 570.474.5100....
24 Oct Apple unveils iPad Mini and publicly executes the optical drive – Should you care?
Apple's October 23rd event didn't just unveil the iPad Mini, it buried the optical drive. [caption id="attachment_1245" align="alignright" width="273"] R.I.P. Optical Drive[/caption] As I sat down to watch the live stream of Apple's October 23rd event, I was eager to see the new MacBook models, as well as various other upgrades to the iMac and Mac Mini lines. But the big enchilada, the one thing we were all anticipating, was the iPad Mini, a new iPad that is 2/3rds the size of the iPad 2 while remaining about as powerful under the hood. Starting at $329, the iPad Mini may be a bit more expensive than most had hoped, but given the increased convenience of a smaller device -- with a 7.9 inch display as opposed to the iPad's 9.7 inches -- the iPad Mini is sure to be found in places even the full-sized model can't go. As excited as we were for this new iPad, however, I felt a twinge of guilt at what I'd seen during Apple's presentations of their new Macs. I couldn't help but notice that Apple was publicly killing the optical drive. The new 13 inch MacBook Pro with Retina display doesn't have one, the Mac Mini lost one a while ago, and the MacBook Air never had one. On top of that, the new iMac is now 5mm thin -- a feat achieved by, you guessed it, removing the optical drive. "What does Apple have against the optical drive?" I wondered. Try as I might, however, I really couldn't recall the last time I personally used mine. So why should I care? We should care because the optical drive is useful for booting from when something goes wrong with the computer's hard disc. You can also use it to watch movies and burn CDs or DVDs. And it's still useful for copying a music CD to your computer for importing into iTunes, something we often overlook as being a big deal. As important a role as the mp3 format, iPod and iTunes played in the digital music revolution, the one thing that almost no one recalls is the role the compact disc played. If the music industry hadn't introduced this convenient, high-quality format, we might not be where we are today. In the days before Napster and iTunes, the only way to get music on your computer was to rip it yourself. Think about what would happen if we were still relying on the analog format of records or tapes; not only would digitally recording music to your computer suffer from the lower quality of analog, but you'd have to do it in real-time. In other words, if it takes 44 minutes and 28 seconds to listen to Pink Floyd's "Wish You Were Here," it would take you at least that long to record it to your computer's hard drive. Now multiply that by the number of albums you probably own -- that's a lot of time! With CDs and optical drives, we were able to reduce the time it takes to import an album down to seconds rather than minutes. But, of course, this is all ancient history. These days, we just download or stream everything. With the ubiquity of USB thumb drives, cloud storage and digital distribution, we almost don't need the optical drive for anything, anymore. While the optical drive does still have some life left in it, if getting rid of it means thinner devices with fewer moving parts (and less that can go wrong with them), then perhaps this really is time to say goodbye. So long, optical drive. Shine on, you crazy diamond!...
22 Oct NEPA Geeks has a New Computer Repair Flag
See our new computer repair sign at NEPA Geeks Here at the NEPA Geeks headquarters we've been working hard to make our computer repair business more visible to the public. One of the big things Jason has been excited about is installing a "Computer Repair" flag that people can easily see from the street. Well, we finally got one! Here are some unboxing photos, including a photo of the flag in all its glory. [gallery size="thumbnail"] So, the next time you're driving through Mountain Top, PA, be sure to look for our flag at the side of the road. And if you need your PC, Mac or iPhone fixed, stop in and talk to us! We'll be more than happy to help you out....
08 Jul What the DNSChanger malware is — and why you should care (FAQ)
Originally posted by CNET: This graphic shows how the DNSChanger malware worked. (Credit: FBI) The DNSChanger malware has been around for years, but its deleterious effects are coming to a head this Monday. Here's what you have to know about it, and how to fix it. What is DNSChanger? DNSChanger is a Trojan horse malware with many variants. It changes an infected computer's DNS settings to point to rogue, bad guy-controlled servers. These then show you ads that look real, but aren't. Basically, it redirects your legitimate Web surfing to malicious Web sites that then attempt to steal personal information and generate illegitimate ad revenue. How much money did DNSChanger make? From the time it was discovered around 2007 until six Estonian scammers were caught in November 2011, DNSChanger scored them upwards of $14 million, reportedly. What does DNSChanger do? DNSChanger changes your Domain Name System settings without your permission. This is bad because DNS is basically the Internet's phone book crossed with a map. DNS links a URL, such as CNET.com, to an IP address. (An IPv4 address would be something like 192.1.56.10, while an IPv6 address would look like 1050:0:0:0:5:600:300c:326b.) DNSChanger changes that and redirects search results and URLs to malicious sites that are designed to either serve you ads to malicious sites, or intend to illegitimately collect your login information. Related stories FBI tackles DNSChanger malware scam Operation Ghost Click DNS servers to remain online until July Web could vanish for hordes of people in July, FBI warns Google will alert users to DNSChanger malware infection New DNSChanger Trojan variant targets routers If the bad guys have been caught already, why does DNSChanger still affect people? Simply put, the malware was exceedingly effective and infected hundreds of thousands of computers. Prior to the bad guys being arrested, the Federal Bureau of Investigation and German Federal Office for Information Security created a redirect of the redirect, so that many people infected by DNSChanger would still go to the legitimate Web sites that they intended to visit. After the arrests, the two governments agreed to keep the rogue DNS servers running until March. Then they learned that there were still around 450,000 active DNSChanger infections, and so the servers got a reprieve until Monday, July 9. If your computer's been infected and you haven't fixed it by July 8, your Monday morning will be even worse than normal. So the Facebook alerts and Google warnings about DNSChanger were legit? Yep. And around 330,000 people were still infected with DNSChanger as of the end of May, with about 77,000 of those in the U.S. Google's warning that appeared at the top of search results. (Credit: CNET) How can I tell if I'm infected? If you're in the United States, go to dns-ok.us or its parent site, the DNSChanger Working Group for computers based outside of the U.S. Click on the URL appropriate to your country, and you'll see an image with a green background if you're clean. A red background means you're infected. Help! My computer's infected with DNSChanger. How can I fix it? The DCWG has a list of free tools to download and instructions on how to clean a computer infected with DNSChanger. How can I avoid malware like DNSChanger in the future? Security suites aren't perfect, but they will protect you from the vast majority of threats out there including DNSChanger. Whether you're on Windows or Mac, Android or iOS, you really ought to have some kind of security program installed. And always double-check the URL before entering personal information into any kind of online text field or form, no matter what operating system or device you're using....
24 Jun Live from New York, its GDGT
By: Patrick Gensel The Altman building in NYC was filled to the brim with geeks and tech toys this past Tuesday evening. The popular social knowledge base for all things tech, GDGT, held its second event in New York City. The lighting in the venue was dim, the athmosphere felt "Cutting Edge" which was fitting considering the nearly 30 vendors all showing off the latest and greatest in consumer electronics. case maker Incipio was the first vendor visible upon entering the Altman building. They showed off new toys like their NGP iphone case which was made of a unique next generation polymer which resisted breaking and wear like traditional plastic or silicone cases would. They also had an external backup battery called the off grid which allowed you to charge your iPad, iPhone, iPod and more when you can't plug into an outlet. The next vendor in line was Roku. Their booth screamed “come play with us” thanks to the Angry Birds plush toys strewn about. If this seems a bit odd to you, thats alright, it caught me off guard too. Roku has recently inked a partnership deal with Rovio, the company behind the wildly popular game which has had folks glued to their mobile devices for hours on end. In addition to bringing the Angry Birds experience to the TV screen, the Roku marketplace will also enable folks to buy Angry Birds plush dolls. Another notable step for Roku is their move into big box retail. Look for their set top boxes this fall in places like Best Buy and others. Marvell Semiconductor was present showing off their recent acquisition. Kinoma is a mobile applications platform that can be likened to that of Adobe Air; the big difference being that, unlike Air, Kinoma is completely open source. This allows for a more community driven experience. Marvell demonstrated Kinoma using a suite of apps on a mobile phone and simulated mobile phone on the LCD. Out of all of the amazing innovations on the show floor, nothing was quite as peculiar as the Thing-O-Matic by MakerBot Industries. Think Creepy Crawlers oven meets desktop printer and you won't be too far off from the Thing-O-Matic. The concept is simple: design an object on your computer and let the Thing-O-Matic do the rest. This open source 3D printer will churn out plastic sculptures of just about anything under 5”x 5” x 5”. Speaking of bots, IRobot was present with the latest iterations of their Roomba and Scuba housekeeping robots. Why clean your floors when a robot will do it for you? The GDGT New York event was a great show. In terms of scale, it was no CES, but the small size made it possible to visit most, if not all of the vendors. All the reps for the brands were really passionate about the products they represented and GDGT founders Peter Rojas and Ryan Block mingled with everyone as if they were part of the show going crowd themselves. Keep up the good work guys and lets see this thing back in New York soon for round 3. ...
21 Feb Look for our new ad.
Be on the look out for our first print advertisement coming soon in The Target Shopper. The ad was designed by Kristen Blake of Kristen Blake Creative. We highly recommend her for any creative work you may need, she produced an ad that kept our branding image in mind and was very responsive to any changes we requested. ...
01 Jan Web hosting services now available
We are pleased to announce the launch of our web hosting site nepageeks.net. We have hosting plans starting as low as $5.99 a month, or $69.99 a year. All yearly hosting plans also come with free domain name registration....