23 Jan Will That Click Cost You Thousands?
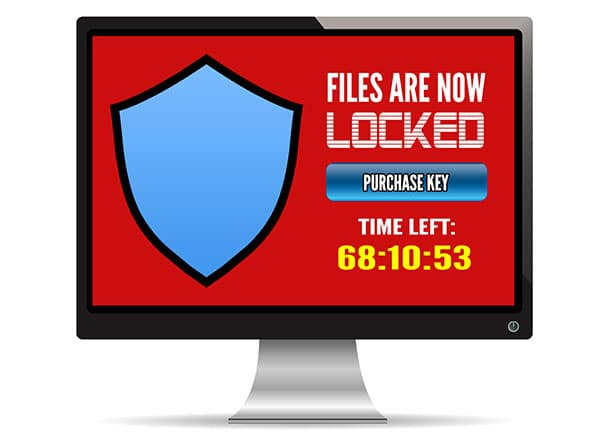
Will That Click Cost You Thousands? Just one click can cost thousands. Ransomware has undeniably been the biggest security threat of 2016. No-one was safe. Hackers targeted everyone and everything, including home PCs, earning themselves upwards of $846million from US reported incidents alone. Business is booming for hackers, with thousands of attacks each day bringing in an average of $640 per target. More alarmingly, the financial cost of each individual attack is on the rise. The more ransomware proves to be an easy earner for them, the more they demand each time. For a quick payday, some hackers offer to ‘rescue’ you from immediate danger – for a fee. One method is to trick you into thinking you have a virus that will spread if you don’t pay money to remove it immediately. Another much scarier method is to pretend to be the FBI and say your computer was involved in a crime (anything from money laundering to child pornography) and you can avoid going to prison by paying a few hundred dollars. Thousands of regular people are also waking up every day to discover they’ve been locked out of their own files. Entire music and video libraries, digital photos from the past 5 years, personal budget files and even their secret novel draft …all held hostage until the user pays a ransom. The encryption is so strong and unbreakable that paying the ransom often becomes the only solution. Ways Ransomware Gets Into PCs The way ransomware gets onto your computer is deviously simple. Generally, the hackers convince you to click an email attachment/link or pop-up. With both approaches, the hacker usually offers helpful information, for example: Tracking an unclaimed parcel Alerting that a virus was found and needs to be removed Advising details of a recent traffic fine It’s so tempting to click through for more details and that’s what the hackers count on. Their messages and pop-ups aren’t obvious threats and so slip easily under our radar. Unfortunately, they’re not the most trustworthy bunch so paying may not actually unlock your files, and one payment can quickly become several. To make matters worse, they can encrypt any backups connected to your computer too, like a USB drive. Having a backup is super important in any situation, but in cases like this, the right backup is needed. Not only one stored separate from your network, but one created recently with all the files you can’t bear to lose. Before restoring your backup, however, you’ll need to make sure the malware isn’t lurking in the background, ready to not just re-infect your restored files but also the backup drive itself. To avoid finding yourself up to the waist in ransom demands or sending hackers money each month, we recommend being wary of email attachments, even from friends and family. If you’re not sure what the file is, don’t click it. They may not have sent that email intentionally; their infected system may be auto-emailing everyone in the address book. You should also be careful with any popups that appear out of place, especially ones that try to make you panic. If it doesn’t sound right or look right, don’t click it. Ransomware is just too dangerous to risk. Call us at 570.235.1946 or visit our Contact Page...