20 Sep Apple’s iOS 17 Brings Assistive Access
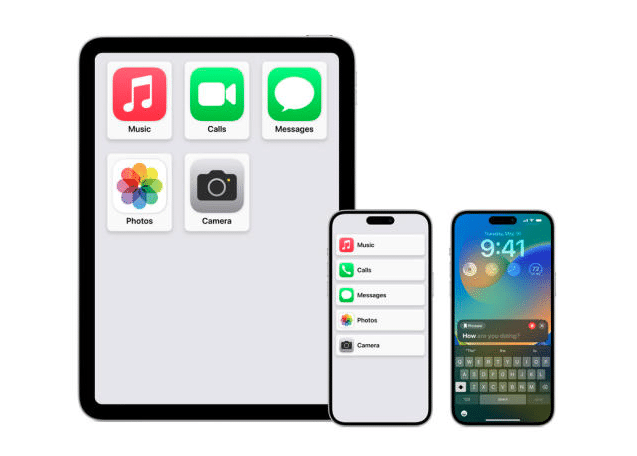
Apple's iOS 17 brings many new accessibility features aimed to lighten cognitive load. Among these features is Assistive Access. "Assistive Access uses innovations in design to distill apps and experiences to their essential features in order to lighten cognitive load" (Apple, 2023). This brings many cognitive accessibility features to the table. Tim Cook aims for Apple to be usable by any one with disabilities. Key Features of Assistive Access "Assistive access includes a customized experience for Phone and FaceTime, which have been combined into a single Calls app, as well as Messages, Camera, Photos, and Music. The feature offers a distinct interface with high contrast buttons and large text labels, as well as tools to help trusted supporters tailor the experience for the individual they support" (Miller, 2023). This makes it much easier to see apps and text on the screen, as well as streamlining the most essential apps. "For example, for users who prefer communicating visually, Messages includes an emoji-only keyboard and the option to record a voice message to share with loved ones" (Miller, 2023). How to Setup Assistive Access on iPhone Make sure you have iOS 17 installed. Step 1: Go to Settings > Accessibility > Assistive Access, tap Set Up Assistive Access, then tap Continue. Step 2: Verify Apple ID. Step 3: Choose layouts for apps. Step 4: Choose and customize apps. Step 5: Verify device passcode. Step 6: Set Assistive Access passcode. Step 7: Learn how to exit assistive access. Step 8: To enter Assistive Access later, go to Settings > Accessibility > Assistive Access, tap Start Assistive Access, then enter the Assistive Access passcode (Apple Support, 2023). These steps can be found in more detail here Need help setting up Assistive Access? Contact Us References Apple. “Apple Introduces New Features for Cognitive Accessibility, Along With Live Speech, Personal Voice, and Point and Speak in Magnifier.” Apple Newsroom, 28 Aug. 2023, apple.com/newsroom/2023/05/apple-previews-live-speech-personal-voice-and-more-new-accessibility-features Miller, Chance. “Apple Previews iOS 17 Accessibility Features: Assistive Access, Personal Voice and Live Speech, More - 9to5Mac.” 9to5Mac, 16 May 2023, 9to5mac.com/2023/05/16/apple-ios-17-accessibility-features “Set up Assistive Access on iPhone.” Apple Support, support.apple.com/guide/assistive-access-iphone/set-up-assistive-access-devcd5016d31/17.0/ios/17.0 ...