03 Dec New malware, CryptoLocker, locks your files and holds them for ransom
Because we care about our customers, we want you all to be on alert for a new strain of malware going around. It’s called CryptoLocker, and it extorts money from victims by encrypting their files and holding them for ransom.
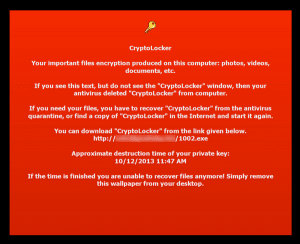
Image source: GrahamCluely.com
What is CryptoLocker? It’s a nasty piece of malware (or ransomware) that encrypts the files on a victim’s hard drive, rendering them unreadable. Photos, documents, PowerPoint Slides, etc… nearly everything you have stored on your hard drive becomes garbled bits of useless data without the key to unlock them. To get the key, victims are asked to pay hundreds of dollars in untraceable currency — with no guarantee that they will ever get them back, of course. To add insult to injury, it seems the bad guys don’t like credit cards, which can be easily traced and revoked by the card issuing companies. They accept only BitCoin, MoneyPak and other annoyingly difficult methods of payment on their ransom.
CryptoLocker only affects Windows users, for the time being. Linux and Apple’s OSX remain immune to the attack, although this could change in the future.
So, what can you do about it?
Currently, the only way to get your files back from CrytpoLocker is to not lose them in first place. What this means is that, if you haven’t been infected yet, buy yourself an external backup drive (many fine models exist at your local retailer for less than $100) and save everything that is important to you on the drive. It’s important that you buy a model with enough space to store your important information but that has enough room to store future backups, as well. If you can, buy 2 drives — one to do automatic backups on a nightly/weekly basis and another that will have only your most precious data, disconnected and safely tucked away where it will be safe from physical damage and/or theft.
If you have malware/virus protection, make sure it is running and up to date! Most of the vendors have already updated their products to check for and defend against CryptoLocker, but there’s nothing they can do once the malware has already ransacked your drive. Encrypted files are EXTREMELY difficult to decrypt. In much the same way data stored by government and financial institutions are encrypted to protect them from hackers, so too will be the data on your hard drive. CryptoLocker is that nasty!
Be wary of any .exe files you might have acquired from unfamiliar sources, and especially don’t run anything sent to you in an email, even from trusted sources. Most often, these programs are spread by people you know who don’t know they are infected.
If you have been infected by CryptoLocker, it’s already too late. We can purge your system of the malware, but encrypted files are encrypted files… There’s nothing we can do. This last fact cannot be stressed enough: encrypted files are very, very difficult to decrypt without the key, and there’ s no guarantee that the files will be decrypted even if you do pay the ransom. Therefore, backup your data immediately and keep it somewhere safe. If you do get infected, all we’ll have to do is get rid CryptoLocker and restore your computer from the backup.
For more information on CryptoLocker, Graham Cluely has an excellent write-up on. Or contact us, and we’ll more than happy to help you out.


